How to Become a Cybersecurity Engineer: Complete Career Guide 2025 [₹12L Average Salary]
Master cybersecurity and protect digital assets from evolving threats
Cybersecurity engineers are among the most critical and well-compensated professionals in technology today, with average salaries ranging from ₹6-20 LPA in India and senior cybersecurity architects earning ₹35+ LPA. As cyber threats become increasingly sophisticated and businesses face mounting regulatory requirements, the ability to design, implement, and maintain comprehensive security frameworks has become one of the most valuable and essential skills in the digital economy.
Whether you’re an IT professional seeking specialization in security, a network administrator looking to advance into cybersecurity, or a fresh graduate entering the growing security field, this comprehensive guide provides the proven roadmap to building a successful cybersecurity career. Having trained over 280 cybersecurity professionals at Frontlines EduTech with a 91% job placement rate, I’ll share the strategies that consistently deliver results in this high-demand, rapidly evolving field.
What you’ll master in this guide:
- Complete cybersecurity learning pathway from fundamentals to advanced threat detection
- Essential security tools and technologies for enterprise protection
- Portfolio projects demonstrating real security implementations and incident response
- Industry certifications and compliance frameworks driving career advancement
- Career opportunities in security operations, architecture, and consulting
🚀 Kickstart Your Cybersecurity Career — Join Our Cybersecurity Training Program!
1. What is Cybersecurity Engineering?
Cybersecurity engineering involves designing, implementing, and maintaining comprehensive security architectures to protect organizations from cyber threats, ensure regulatory compliance, and maintain business continuity. This discipline encompasses threat assessment, security architecture design, incident response, risk management, and the integration of security controls across all aspects of an organization’s technology infrastructure.
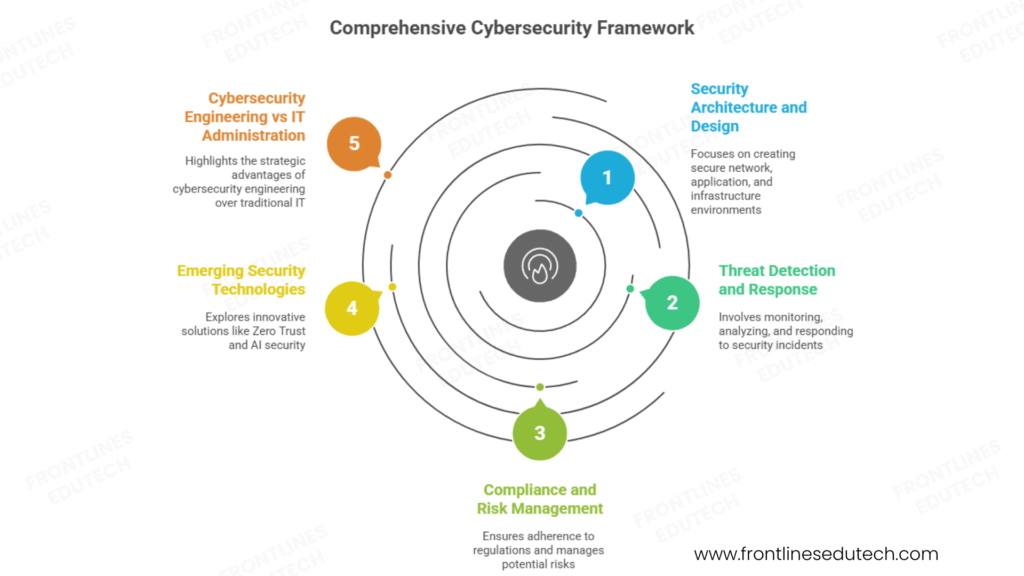
Core Components of Cybersecurity Engineering:
Security Architecture and Design:
- Network Security – Firewalls, intrusion detection/prevention systems, network segmentation, VPN implementation
- Application Security – Secure coding practices, vulnerability assessment, penetration testing, security testing
- Infrastructure Security – Server hardening, endpoint protection, identity and access management, privileged access
- Cloud Security – AWS, Azure, GCP security configurations, container security, serverless security
Threat Detection and Response:
- Security Operations Center (SOC) – SIEM implementation, log analysis, threat hunting, incident coordination
- Incident Response – Forensic analysis, containment strategies, recovery procedures, lessons learned
- Threat Intelligence – Attack pattern analysis, threat actor profiling, indicator of compromise (IOC) management
- Vulnerability Management – Risk assessment, patch management, security scanning, remediation prioritization
Compliance and Risk Management:
- Regulatory Compliance – ISO 27001, SOX, PCI DSS, GDPR, HIPAA implementation and auditing
- Risk Assessment – Business impact analysis, threat modeling, quantitative risk analysis
- Security Governance – Policy development, security awareness training, audit coordination
- Business Continuity – Disaster recovery planning, backup strategies, business impact assessment
Emerging Security Technologies:
- Zero Trust Architecture – Identity verification, least privilege access, micro-segmentation
- AI/ML Security – Behavioral analytics, anomaly detection, automated threat response
- DevSecOps – Security automation, secure CI/CD pipelines, infrastructure as code security
- IoT and Edge Security – Device management, secure communications, edge computing protection
Cybersecurity Engineering vs IT Administration
Traditional IT Administration Focus:
- System uptime, performance optimization, user support
- Basic security measures, password policies, antivirus management
- Reactive approach to security incidents and breaches
- Limited understanding of advanced threat landscapes
Cybersecurity Engineering Advantages:
- Proactive threat hunting and advanced persistent threat (APT) detection
- Comprehensive security architecture spanning people, processes, and technology
- Deep understanding of attack vectors and defense-in-depth strategies
- Strategic alignment of security investments with business risk tolerance
🛡️ Want a Clear Learning Path? Explore the Complete Cybersecurity Roadmap →
2. Why Choose Cybersecurity in 2025?
Critical Security Skills Shortage and Growing Threat Landscape
According to Cybersecurity Workforce Study 2025, the global cybersecurity workforce shortage has reached 3.4 million professionals. In India specifically, cybersecurity demand has exploded across all sectors:
Enterprise Cybersecurity Transformation:
- Banking and Financial Services – Regulatory compliance, fraud prevention, customer data protection, digital banking security
- Healthcare and Pharmaceuticals – Patient data privacy, medical device security, telemedicine protection, regulatory compliance
- Government and Defense – Critical infrastructure protection, national security, citizen data privacy, cyber warfare defense
- Technology and E-commerce – Platform security, customer data protection, payment processing security, API security
Emerging Threat Vectors Driving Demand:
- Ransomware and Cyber Extortion – 300% increase in attacks targeting critical infrastructure and healthcare
- Supply Chain Attacks – SolarWinds-style attacks compromising software supply chains globally
- Cloud Security Challenges – Multi-cloud environments creating new attack surfaces and compliance requirements
- IoT and 5G Security – Billions of connected devices requiring comprehensive security frameworks
Premium Compensation and Career Security
Cybersecurity professionals command high salaries due to critical skills shortage and business risk:
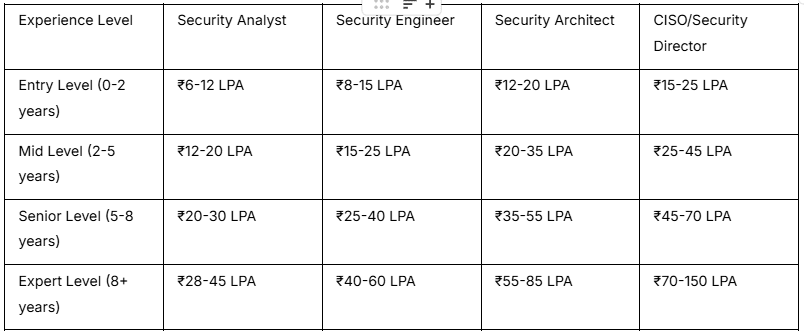
Source: PayScale India 2025, Glassdoor Cybersecurity Salaries
Recession-Proof Career with Global Opportunities
Cybersecurity offers exceptional career stability:
- Business Critical Function – Security is essential regardless of economic conditions
- Regulatory Requirements – Compliance mandates ensure continued investment in security
- Remote Work Friendly – Security operations and consulting can be performed globally
- Multiple Career Paths – Technical, management, consulting, and entrepreneurial opportunities
High-Impact Work with Societal Value
Cybersecurity professionals protect critical infrastructure and individual privacy:
- National Security – Protect critical infrastructure from nation-state attacks
- Individual Privacy – Safeguard personal information and financial data
- Business Continuity – Ensure organizations can operate securely and efficiently
- Innovation Enablement – Enable digital transformation through secure technology adoption
📘 Explore 200+ Cybersecurity Learning Resources — Start Learning Smarter!
3. Complete Learning Roadmap (4-6 Months)
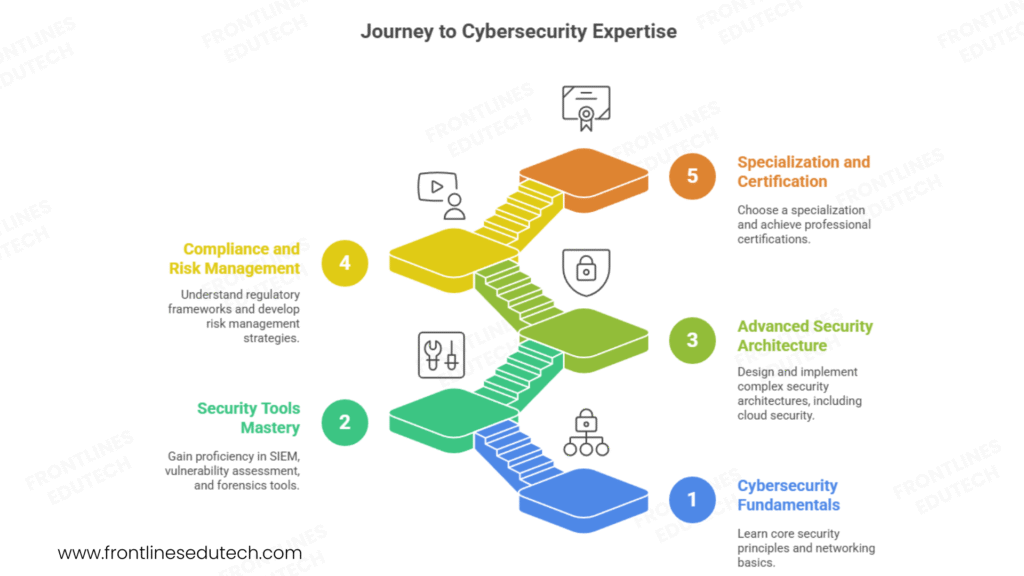
Phase 1: Cybersecurity Fundamentals and Networking (Month 1)
Cybersecurity Foundation Concepts (2-3 weeks)
Understanding core security principles is essential before diving into specific technologies:
- CIA Triad – Confidentiality, integrity, availability as security pillars
- Risk Management – Asset identification, threat assessment, vulnerability analysis, risk calculation
- Security Frameworks – NIST Cybersecurity Framework, ISO 27001, CIS Controls
- Attack Vectors – Social engineering, malware, network attacks, physical security
Networking and Infrastructure Security (2-3 weeks)
- Network Fundamentals – TCP/IP, subnetting, routing, switching, DNS, DHCP
- Network Security – Firewalls, IDS/IPS, VPNs, network segmentation, DMZ design
- Wireless Security – WPA/WPA2/WPA3, enterprise wireless, rogue access point detection
- Infrastructure Hardening – Server security, endpoint protection, patch management
Operating Systems Security (1-2 weeks)
- Windows Security – Active Directory, Group Policy, Windows Defender, event logs
- Linux Security – User management, file permissions, systemd, iptables, SELinux
- Mobile Security – iOS/Android security models, mobile device management (MDM)
- Virtualization Security – Hypervisor security, container security, virtual network isolation
Foundation Projects:
- Home Network Security Audit – Comprehensive security assessment with remediation plan
- Virtual Lab Setup – Create isolated environment for security testing and learning
- Security Policy Development – Write comprehensive security policies for small business
Phase 2: Security Tools and Threat Detection (Month 2-3)
Security Information and Event Management (SIEM) (3-4 weeks)
- SIEM Fundamentals – Log collection, correlation, alerting, dashboard creation
- Splunk – Search Processing Language (SPL), data ingestion, alert creation, dashboard development
- Elastic Stack (ELK) – Elasticsearch, Logstash, Kibana for log analysis and visualization
- IBM QRadar – Rules engine, offense management, custom properties, reporting
Vulnerability Assessment and Penetration Testing (3-4 weeks)
- Vulnerability Scanning – Nessus, OpenVAS, Qualys for automated vulnerability detection
- Network Penetration Testing – Nmap, Metasploit, Wireshark, Burp Suite for security testing
- Web Application Security – OWASP Top 10, SQL injection, cross-site scripting, security testing
- Social Engineering – Phishing simulation, awareness training, human factor security
Digital Forensics and Incident Response (2-3 weeks)
- Forensic Fundamentals – Evidence preservation, chain of custody, forensic imaging
- Memory Analysis – Volatility framework, malware analysis, live system investigation
- Network Forensics – Packet analysis, traffic patterns, intrusion investigation
- Incident Response – NIST incident response framework, containment, eradication, recovery
Security Tool Mastery Projects:
- SIEM Implementation – Deploy Splunk or ELK stack with custom dashboards and alerts
- Penetration Testing Report – Complete security assessment of vulnerable applications
- Incident Response Simulation – End-to-end incident response from detection to recovery
Phase 3: Advanced Security Architecture and Cloud Security (Month 3-4)
Enterprise Security Architecture (4-5 weeks)
- Zero Trust Model – Identity verification, least privilege, network micro-segmentation
- Identity and Access Management – Single sign-on (SSO), multi-factor authentication, privileged access management
- Security Operations Center (SOC) – SOC design, analyst workflows, threat hunting processes
- Threat Modeling – STRIDE methodology, attack trees, security requirements analysis
Cloud Security Implementation (3-4 weeks)
- AWS Security – IAM, VPC security groups, CloudTrail, GuardDuty, Security Hub
- Azure Security – Azure Active Directory, Network Security Groups, Azure Security Center
- Google Cloud Security – Cloud IAM, VPC firewall rules, Cloud Security Command Center
- Container Security – Docker security, Kubernetes security, container scanning, runtime protection
DevSecOps and Automation (2-3 weeks)
- Secure CI/CD Pipelines – Static application security testing (SAST), dynamic application security testing (DAST)
- Infrastructure as Code Security – Terraform security, CloudFormation security, configuration management
- Security Automation – Python scripting for security tasks, API integration, automated response
- Compliance as Code – Automated compliance checking, policy as code, audit automation
Advanced Architecture Projects:
- Zero Trust Network Design – Comprehensive zero trust implementation plan
- Multi-Cloud Security Architecture – Unified security framework across cloud providers
- Automated Security Response System – Python-based automation for incident response
Phase 4: Compliance and Risk Management (Month 4-5)
Regulatory Compliance Frameworks (4-5 weeks)
- ISO 27001 – Information Security Management System implementation
- NIST Framework – Cybersecurity framework implementation and maturity assessment
- PCI DSS – Payment card industry security requirements and validation
- GDPR/Data Privacy – Privacy by design, data protection impact assessments, breach notification
Risk Management and Business Continuity (3-4 weeks)
- Quantitative Risk Analysis – Asset valuation, threat frequency, impact assessment
- Business Impact Analysis – Critical process identification, recovery time objectives
- Disaster Recovery Planning – Recovery strategies, testing procedures, communication plans
- Vendor Risk Management – Third-party security assessments, supply chain risk
Governance and Program Management (2-3 weeks)
- Security Program Development – Metrics, KPIs, executive reporting, budget planning
- Security Awareness Training – Program design, phishing simulations, culture development
- Audit and Assessment – Internal audits, external assessments, remediation tracking
- Incident Management – Process design, stakeholder communication, lessons learned
Compliance and Risk Projects:
- ISO 27001 Implementation Plan – Complete ISMS implementation for medium organization
- Business Continuity Plan – Comprehensive disaster recovery and business continuity framework
- Risk Assessment and Remediation – Quantitative risk analysis with prioritized remediation plan
Phase 5: Specialization and Professional Certification (Month 5-6)
Choose Specialization Track:
Security Operations Center (SOC) Analyst:
- Advanced SIEM administration and threat hunting
- Malware analysis and reverse engineering
- Incident response coordination and forensics
- Threat intelligence analysis and IOC development
Cloud Security Specialist:
- Multi-cloud security architecture and implementation
- Container and serverless security
- Cloud compliance and governance
- DevSecOps pipeline security integration
Penetration Tester/Ethical Hacker:
- Advanced penetration testing methodologies
- Mobile application and IoT security testing
- Social engineering and physical security testing
- Red team operations and adversary simulation
Compliance and Risk Manager:
- Regulatory framework implementation
- Risk management program development
- Audit coordination and remediation management
- Executive communication and business alignment
Professional Certification Preparation:
- CompTIA Security+ – Foundation certification covering broad security topics
- CISSP – Advanced certification for security professionals with experience
- CEH – Certified Ethical Hacker for penetration testing specialization
- CISM – Certified Information Security Manager for management roles
🔥 Master Cybersecurity Skills Faster — Join Our Expert-Led Course →
4. Essential Cybersecurity Tools and Technologies
Security Information and Event Management (SIEM)
Enterprise SIEM Platforms:
- Splunk – Market-leading SIEM with powerful search capabilities and extensive integration
- IBM QRadar – Enterprise SIEM with advanced threat detection and response automation
- ArcSight – HP ArcSight for large-scale enterprise security monitoring and compliance
- LogRhythm – Integrated SIEM platform with built-in network and endpoint monitoring
Open Source and Cloud SIEM:
- Elastic Stack (ELK) – Elasticsearch, Logstash, Kibana for scalable log analysis
- OSSIM – Open Source Security Information Management with correlation engine
- Wazuh – Open source security monitoring with host-based intrusion detection
- AWS Security Hub – Cloud-native security monitoring and compliance management
Vulnerability Assessment and Penetration Testing
Vulnerability Scanners:
- Nessus – Comprehensive vulnerability scanner with extensive vulnerability database
- OpenVAS – Open source vulnerability assessment with customizable scanning policies
- Qualys – Cloud-based vulnerability management with continuous monitoring
- Rapid7 Nexpose – Enterprise vulnerability management with risk prioritization
Penetration Testing Frameworks:
- Metasploit – Exploitation framework with extensive exploit database and payload generation
- Kali Linux – Specialized Linux distribution with 600+ penetration testing tools
- Burp Suite – Web application security testing platform with automated and manual testing
- Cobalt Strike – Advanced adversary simulation and red team operations platform
Network Security and Monitoring
Network Security Appliances:
- Palo Alto Networks – Next-generation firewalls with application and user identification
- Fortinet FortiGate – Unified threat management with high-performance security processing
- Cisco ASA/Firepower – Enterprise firewall and intrusion prevention systems
- Check Point – Security gateways with threat prevention and advanced persistent threat protection
Network Monitoring and Analysis:
- Wireshark – Network protocol analyzer for packet-level traffic analysis
- Nagios – Infrastructure monitoring with alerting and performance tracking
- SolarWinds – Network performance monitoring with security event correlation
- PRTG – Network monitoring with sensor-based architecture and custom alerts
Identity and Access Management
Enterprise IAM Solutions:
- Microsoft Active Directory – Windows-centric identity and access management
- Okta – Cloud-based identity management with single sign-on and multi-factor authentication
- CyberArk – Privileged access management for critical system and application access
- Ping Identity – Enterprise identity solutions with API security and customer identity
Multi-Factor Authentication:
- RSA SecurID – Hardware and software token-based authentication
- Duo Security – Cloud-based multi-factor authentication with device trust
- Authy – Mobile and desktop authenticator with backup and sync capabilities
- YubiKey – Hardware security keys for strong authentication and passwordless login
⚙️ Master SIEM & Security Tools — Explore Practical interview Guides!
5. Building Your Cybersecurity Portfolio
Portfolio Strategy and Structure
Cybersecurity Portfolio Objectives:
- Demonstrate Technical Proficiency – Show mastery of security tools, frameworks, and methodologies
- Highlight Risk Management – Quantify security improvements and risk reduction achievements
- Showcase Compliance Knowledge – Display understanding of regulatory requirements and implementation
- Present Incident Response – Document security incident handling and forensic analysis capabilities
Foundation Level Projects (Months 1-3)
- Comprehensive Security Assessment and Remediation
- Scope: Complete security audit of small-medium business infrastructure including network, systems, and applications
- Technical Implementation: Vulnerability scanning, penetration testing, configuration review, policy assessment
- Deliverables: Executive summary, technical findings, risk assessment, remediation roadmap, cost-benefit analysis
- Business Impact: Identify and prioritize security risks, provide actionable recommendations, estimate risk reduction
- Documentation: Professional security assessment report with executive and technical sections
Security Assessment Implementation:
#!/bin/bash
# Automated Security Assessment Script
# Network Discovery and Port Scanning
echo “Starting Network Discovery…”
nmap -sn 192.168.1.0/24 > network_hosts.txt
nmap -sS -O -sV -A -T4 -iL network_hosts.txt -oA network_scan
# Vulnerability Scanning with OpenVAS
echo “Launching Vulnerability Scan…”
omp –username admin –password admin –host localhost \
–xml “<create_target><name>Assessment_Target</name><hosts>192.168.1.0/24</hosts></create_target>”
# Web Application Security Testing
echo “Testing Web Applications…”
nikto -h http://target-web-app.com -o nikto_results.txt
sqlmap -u “http://target-app.com/login.php” –forms –dbs –batch
# System Configuration Review
echo “Auditing System Configurations…”
# Windows systems
wmic qfe list
net user
net localgroup administrators
# Linux systems
sudo lynis audit system –quick
sudo chkrootkit
sudo rkhunter –check –skip-keypress
# Generate Comprehensive Report
echo “Generating Security Assessment Report…”
python3 generate_security_report.py \
–network-scan network_scan.xml \
–vulnerability-scan vuln_results.xml \
–web-app-scan nikto_results.txt \
–config-audit lynis_report.dat \
–output security_assessment_report.pdf
- Security Operations Center (SOC) Implementation
- Business Challenge: Organization needs 24/7 security monitoring and incident response capabilities
- Technical Solution: Design and implement comprehensive SOC using open-source tools (ELK stack, Wazuh, TheHive)
- Advanced Features: Custom correlation rules, automated alerting, threat intelligence integration, incident workflow
- Metrics: Mean time to detection (MTTD), mean time to response (MTTR), false positive rate, coverage assessment
- Business Value: Proactive threat detection, reduced incident impact, compliance demonstration
Intermediate Level Projects (Months 3-5)
- Cloud Security Architecture Design
- Challenge: Multi-cloud environment requiring unified security architecture and compliance framework
- Solution: Comprehensive cloud security design spanning AWS, Azure, and Google Cloud with automated compliance monitoring
- Technical Components: Identity federation, network security, data encryption, logging, monitoring, incident response
- Advanced Implementation: Infrastructure as code, automated security scanning, compliance reporting, cost optimization
- Business Impact: Unified security posture, regulatory compliance, reduced operational overhead
Cloud Security Architecture Example:
# Terraform configuration for multi-cloud security
# AWS Security Configuration
provider “aws” {
region = “us-east-1”
}
# VPC with security groups
resource “aws_vpc” “secure_vpc” {
cidr_block = “10.0.0.0/16”
enable_dns_hostnames = true
enable_dns_support = true
tags = {
Name = “SecureVPC”
Environment = “Production”
Compliance = “PCI-DSS”
}
}
# Security groups with least privilege
resource “aws_security_group” “web_sg” {
name_prefix = “web-sg”
vpc_id = aws_vpc.secure_vpc.id
ingress {
from_port = 443
to_port = 443
protocol = “tcp”
cidr_blocks = [“0.0.0.0/0”]
}
ingress {
from_port = 80
to_port = 80
protocol = “tcp”
cidr_blocks = [“0.0.0.0/0”]
}
egress {
from_port = 0
to_port = 0
protocol = “-1”
cidr_blocks = [“10.0.0.0/16”] # Internal traffic only
}
tags = {
Name = “WebSecurityGroup”
Type = “DMZ”
}
}
# CloudTrail for audit logging
resource “aws_cloudtrail” “security_audit” {
name = “security-audit-trail”
s3_bucket_name = aws_s3_bucket.audit_logs.bucket
include_global_service_events = true
is_multi_region_trail = true
enable_logging = true
event_selector {
read_write_type = “All”
include_management_events = true
data_resource {
type = “AWS::S3::Object”
values = [“arn:aws:s3:::${aws_s3_bucket.audit_logs.bucket}/*”]
}
}
}
# GuardDuty for threat detection
resource “aws_guardduty_detector” “security_detector” {
enable = true
datasources {
s3_logs {
enable = true
}
kubernetes {
audit_logs {
enable = true
}
}
}
tags = {
Name = “SecurityDetector”
Purpose = “ThreatDetection”
}
}
# Azure Security Configuration
provider “azurerm” {
features {}
}
# Network Security Group
resource “azurerm_network_security_group” “web_nsg” {
name = “web-nsg”
location = azurerm_resource_group.security_rg.location
resource_group_name = azurerm_resource_group.security_rg.name
security_rule {
name = “HTTPS”
priority = 1001
direction = “Inbound”
access = “Allow”
protocol = “Tcp”
source_port_range = “*”
destination_port_range = “443”
source_address_prefix = “*”
destination_address_prefix = “*”
}
security_rule {
name = “SSH”
priority = 1002
direction = “Inbound”
access = “Allow”
protocol = “Tcp”
source_port_range = “*”
destination_port_range = “22”
source_address_prefix = “10.0.0.0/16” # Internal only
destination_address_prefix = “*”
}
}
# Azure Security Center
resource “azurerm_security_center_subscription_pricing” “security_pricing” {
tier = “Standard”
resource_type = “VirtualMachines”
}
# Key Vault for secrets management
resource “azurerm_key_vault” “security_kv” {
name = “security-keyvault”
location = azurerm_resource_group.security_rg.location
resource_group_name = azurerm_resource_group.security_rg.name
tenant_id = data.azurerm_client_config.current.tenant_id
sku_name = “standard”
access_policy {
tenant_id = data.azurerm_client_config.current.tenant_id
object_id = data.azurerm_client_config.current.object_id
secret_permissions = [
“get”, “list”, “set”, “delete”, “recover”, “backup”, “restore”
]
}
network_acls {
default_action = “Deny”
bypass = “AzureServices”
virtual_network_subnet_ids = [
azurerm_subnet.security_subnet.id
]
}
}
Advanced Level Projects (Months 5-6)
- Advanced Persistent Threat (APT) Simulation and Detection
- Sophisticated Challenge: Design and execute red team exercise simulating nation-state attack against enterprise environment
- Technical Complexity: Multi-stage attack chain, living-off-the-land techniques, custom malware development, evasion techniques
- Blue Team Response: Advanced threat hunting, behavioral analysis, machine learning detection, incident containment
- Metrics: Detection coverage, response time, containment effectiveness, lessons learned integration
- Business Impact: Validate security controls, identify gaps, improve incident response capabilities
- Zero Trust Architecture Implementation
- Enterprise Challenge: Legacy network-based security model insufficient for modern threat landscape and remote work
- Comprehensive Solution: Complete zero trust implementation including identity, device, network, and application layers
- Advanced Technologies: Software-defined perimeters, micro-segmentation, continuous verification, risk-based authentication
- Integration Complexity: Legacy system integration, user experience optimization, performance monitoring
- Measurable Outcomes: 90% reduction in lateral movement, 60% improvement in breach detection time
Portfolio Presentation Standards
Professional Documentation Framework:
Cybersecurity Project Documentation Template:
Executive Summary:
– Security challenge and business risk assessment
– Solution approach and architectural decisions
– Risk reduction achieved and compliance status
– Implementation timeline and resource requirements
Technical Architecture:
– Security framework and control mapping
– Technology stack and integration architecture
– Threat model and attack surface analysis
– Performance and scalability considerations
Implementation Details:
– Configuration standards and hardening guides
– Custom scripts and automation workflows
– Monitoring and alerting configuration
– Incident response procedures and playbooks
Risk and Compliance:
– Risk assessment methodology and results
– Regulatory compliance demonstration
– Security metrics and KPI tracking
– Continuous improvement recommendations
Business Impact:
– Risk reduction quantification
– Compliance cost avoidance
– Operational efficiency improvements
– Return on security investment (ROSI)
Live Demonstration Environment:
- Home Security Lab – Virtualized environment for hands-on security testing and incident response
- Cloud Security Showcase – Multi-cloud security implementation with real-time monitoring
- Incident Response Simulation – Documented incident response exercises with lessons learned
- Threat Intelligence Platform – Custom threat intelligence gathering and analysis tools
🧩 Build a Strong Cybersecurity Portfolio — Download Templates & Project Files!
6. Job Search Strategy
Resume Optimization for Cybersecurity Roles
Technical Skills Section:
Cybersecurity Technologies:
• Security Frameworks: NIST Cybersecurity Framework, ISO 27001, CIS Controls, OWASP
• SIEM Platforms: Splunk, IBM QRadar, Elastic Stack (ELK), LogRhythm, AWS Security Hub
• Vulnerability Assessment: Nessus, OpenVAS, Qualys, Rapid7, Metasploit, Burp Suite
• Network Security: Firewalls (Palo Alto, Fortinet), IDS/IPS, VPN, Network Segmentation
• Cloud Security: AWS Security, Azure Security Center, GCP Security, Container Security
• Identity Management: Active Directory, Okta, CyberArk PAM, Multi-Factor Authentication
• Incident Response: Digital Forensics, Malware Analysis, Threat Hunting, SOAR Platforms
Certifications:
• CompTIA Security+ (Current)
• CISSP – Certified Information Systems Security Professional
• CEH – Certified Ethical Hacker
• AWS Certified Security – Specialty
Project Experience Examples:
Enterprise Security Operations Center Implementation
- Challenge: Financial services company needed 24/7 security monitoring and compliance reporting for 5,000+ users
- Solution: Designed and implemented comprehensive SOC using Splunk SIEM, custom correlation rules, and automated incident response
- Technical Achievement: Deployed 15+ security tools, created 200+ correlation rules, integrated threat intelligence feeds
- Business Impact: Reduced mean time to detection from 4 hours to 15 minutes, achieved SOX compliance, prevented $2.5M in potential fraud losses
Multi-Cloud Security Architecture
- Challenge: Technology company required unified security framework across AWS, Azure, and on-premises infrastructure
- Solution: Implemented zero trust architecture with identity federation, micro-segmentation, and continuous monitoring
- Advanced Implementation: Infrastructure as code, automated compliance scanning, integrated SIEM across all environments
- Results: Achieved 99.5% uptime, reduced security incidents by 70%, passed all regulatory audits with zero findings
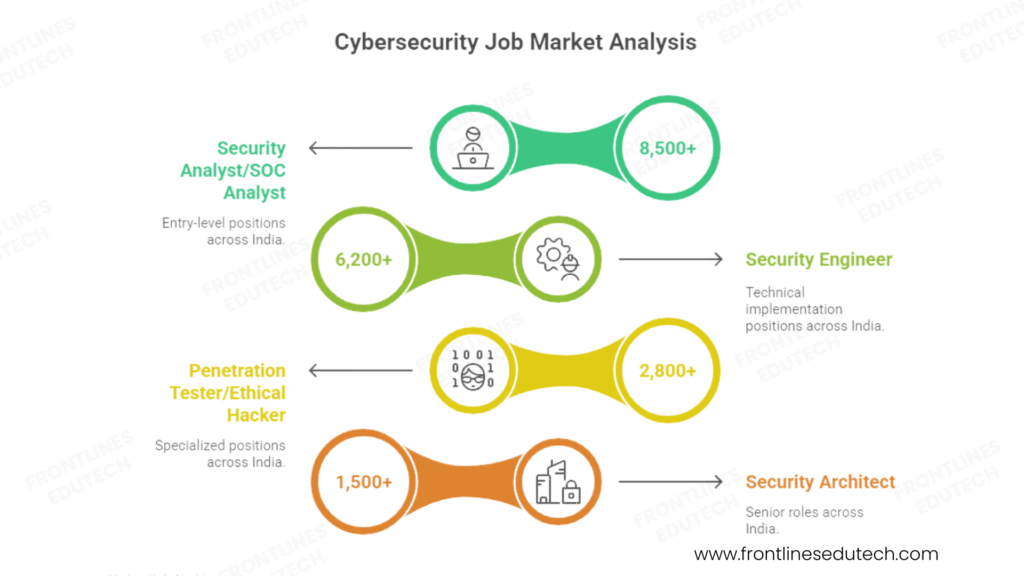
Cybersecurity Job Market Analysis
High-Demand Role Categories:
- Security Analyst/SOC Analyst (Entry Level)
- Salary Range: ₹6-20 LPA
- Open Positions: 8,500+ across India
- Key Skills: SIEM administration, incident response, vulnerability assessment, log analysis
- Growth Path: Analyst → Senior Analyst → SOC Manager → Security Manager
- Security Engineer (Technical Implementation)
- Salary Range: ₹8-25 LPA
- Open Positions: 6,200+ across India
- Key Skills: Security architecture, firewall management, penetration testing, automation
- Growth Path: Engineer → Senior Engineer → Principal Engineer → Security Architect
- Penetration Tester/Ethical Hacker (Specialized)
- Salary Range: ₹10-30 LPA
- Open Positions: 2,800+ across India
- Key Skills: Vulnerability assessment, exploitation techniques, report writing, social engineering
- Growth Path: Penetration Tester → Senior Pentester → Lead Security Consultant → Red Team Leader
- Security Architect (Senior Role)
- Salary Range: ₹20-55 LPA
- Open Positions: 1,500+ across India
- Key Skills: Security framework design, risk assessment, compliance, strategic planning
- Growth Path: Architect → Principal Architect → CISO → VP Security
Top Hiring Companies and Opportunities
Technology and Product Companies:
- Microsoft India – Cloud security, identity management, threat intelligence, security research
- Amazon Web Services – Cloud security services, compliance, threat detection, security automation
- Google India – Security engineering, privacy protection, threat analysis, security research
- Accenture – Cybersecurity consulting, managed security services, security transformation
Financial Services and Banking:
- HDFC Bank – Information security, fraud prevention, regulatory compliance, digital banking security
- ICICI Bank – Cybersecurity operations, risk management, payment security, customer data protection
- Axis Bank – Security architecture, incident response, compliance management, threat intelligence
- Paytm – Payment security, fraud detection, data protection, API security, mobile app security
Cybersecurity Specialized Companies:
- Wipro Cybersecurity – Managed security services, security consulting, threat intelligence
- TCS Cyber Security – Security transformation, compliance services, incident response
- Quick Heal – Endpoint security, threat research, malware analysis, consumer security products
- K7 Security – Antivirus development, threat research, security product development
Government and Defense:
- CERT-In – National cybersecurity incident response, threat intelligence, policy development
- NIC – Government IT security, critical infrastructure protection, citizen data security
- DRDO – Defense cybersecurity research, cyber warfare defense, national security
- Indian Army Cyber Command – Military cybersecurity operations, cyber warfare capabilities
Interview Preparation Framework
Technical Competency Areas:
Security Architecture and Design:
- “Design a security architecture for a cloud-first organization with 10,000 employees”
- Identity and access management strategy
- Network security design with zero trust principles
- Data protection and encryption requirements
- Monitoring and incident response capabilities
- Compliance and governance framework
- “How would you secure a microservices architecture?”
- API security and authentication mechanisms
- Container and Kubernetes security
- Service mesh security implementation
- Secrets management and rotation
- Runtime protection and monitoring
Incident Response and Forensics:
3. “Walk through your incident response process for a ransomware attack”
# Incident Response Playbook Example
# Phase 1: Identification and Containment
# Isolate affected systems
iptables -A INPUT -j DROP # Block all incoming connections
iptables -A OUTPUT -j DROP # Block all outgoing connections
# Preserve evidence
dd if=/dev/sda of=/forensics/disk_image.dd bs=4096
# Phase 2: Investigation
# Analyze system logs
grep -i “ransom\|encrypt\|crypto” /var/log/syslog
# Check running processes
ps aux | grep -E “(crypto|ransom|encrypt)”
# Network connection analysis
netstat -antup | grep ESTABLISHED
# Phase 3: Eradication and Recovery
# Remove malware
# Restore from clean backups
# Apply security patches
# Monitor for reinfection
# Phase 4: Lessons Learned
# Document timeline and actions
# Identify improvement opportunities
# Update incident response procedures
Compliance and Risk Management:
4. “How would you implement PCI DSS compliance for an e-commerce platform?”
- Cardholder data environment (CDE) segmentation
- Access control and authentication requirements
- Encryption implementation for data in transit and at rest
- Vulnerability management program
- Regular security testing and monitoring
Threat Analysis:
5. “Analyze this network traffic and identify potential security threats”
- Packet analysis skills using Wireshark
- Anomaly detection in network patterns
- Malware command and control identification
- Data exfiltration detection techniques
- Indicator of compromise (IOC) analysis
Salary Negotiation and Career Advancement
Cybersecurity Value Propositions:
- Risk Reduction Quantification – Document prevented security incidents, compliance achievements, cost avoidance
- Technical Expertise Breadth – Demonstrate proficiency across multiple security domains and technologies
- Industry Certifications – Maintain current certifications and pursue advanced specializations
- Business Impact Alignment – Connect security initiatives to business objectives and revenue protection
Negotiation Strategy:
Cybersecurity Compensation Package:
Base Salary: ₹X LPA (Premium for specialized skills and critical role)
Performance Bonus: 15-25% of base (Risk reduction, incident response, compliance achievements)
Certification Bonuses: ₹50,000-1,50,000 per advanced certification (CISSP, CISM, etc.)
Learning Budget: ₹75,000-1,50,000 annually (Training, conferences, certification maintenance)
Stock Options: Significant equity in product companies and cybersecurity startups
Flexible Benefits: Conference attendance, security research time, consulting opportunities
Career Advancement Factors:
- Technical Depth – Advanced specialization in high-demand areas (cloud security, AI security, IoT security)
- Business Acumen – Understanding of business risk, regulatory requirements, and strategic alignment
- Leadership Skills – Team management, cross-functional collaboration, executive communication
- Industry Recognition – Speaking at conferences, publishing research, contributing to security communities
- Continuous Learning – Staying current with emerging threats, new technologies, and evolving regulations
🎯 Crack Your First Cybersecurity Job — Access 150+ Interview Q&As!
7. Salary Expectations and Career Growth
2025 Compensation Benchmarks by Role and Specialization
Security Analyst Track:
- Junior Security Analyst (0-2 years): ₹6-12 LPA
- Security Analyst (2-4 years): ₹12-20 LPA
- Senior Security Analyst (4-7 years): ₹20-30 LPA
- Principal Security Analyst (7+ years): ₹28-42 LPA
Security Engineer Track:
- Security Engineer (1-3 years): ₹8-15 LPA
- Senior Security Engineer (3-6 years): ₹15-25 LPA
- Principal Security Engineer (6-10 years): ₹25-40 LPA
- Distinguished Security Engineer (10+ years): ₹40-60 LPA
Penetration Testing Track:
- Penetration Tester (1-3 years): ₹10-18 LPA
- Senior Penetration Tester (3-6 years): ₹18-30 LPA
- Lead Security Consultant (6-10 years): ₹30-45 LPA
- Principal Security Consultant (10+ years): ₹45-70 LPA
Security Architecture and Management Track:
- Security Architect (4-8 years): ₹20-35 LPA
- Principal Security Architect (8-12 years): ₹35-55 LPA
- CISO/Security Director (12-20 years): ₹55-100 LPA
- VP Security/Chief Security Officer (15+ years): ₹80-200 LPA
Industry and Geographic Salary Variations
High-Paying Industries:
- Investment Banking and Financial Services – 35-45% premium for regulatory compliance and high-value asset protection
- Technology and Cloud Service Providers – 30-40% premium for advanced security research and product security
- Government and Defense Contracting – 25-35% premium for security clearance and critical infrastructure protection
- Healthcare and Pharmaceuticals – 20-30% premium for patient data protection and regulatory compliance
Geographic Salary Distribution:
- Bangalore – Technology hub with highest cybersecurity demand, 20-28% above national average
- Mumbai – Financial services center, 18-25% above national average for fintech security roles
- Delhi/NCR – Government and enterprise security focus, 15-22% above national average
- Hyderabad – Growing cybersecurity center, 12-18% above national average
Career Progression Pathways
Technical Specialist Track:
Security Analyst (0-3 years)
↓
Senior Security Engineer (2-6 years)
↓
Principal Security Engineer (5-10 years)
↓
Distinguished Engineer (10-15 years)
↓
Security Fellow/Chief Scientist (15+ years)
Management and Leadership Track:
Senior Security Analyst (3-6 years)
↓
Security Manager (5-9 years)
↓
Security Director (8-15 years)
↓
CISO/VP Security (12-20 years)
↓
Chief Security Officer (15+ years)
Consulting and Entrepreneurial Track:
Security Consultant (3-6 years)
↓
Principal Consultant (6-10 years)
↓
Practice Lead (10-15 years)
↓
Cybersecurity Firm Founder (12+ years)
↓
Security Industry Leader (15+ years)
Skills for Accelerated Career Growth
Technical Mastery (Years 1-4):
- Security Tool Expertise – Deep knowledge of SIEM, vulnerability scanners, penetration testing tools
- Cloud Security – Multi-cloud security architecture and implementation across AWS, Azure, GCP
- Automation and Scripting – Python, PowerShell, Bash for security automation and custom tool development
- Incident Response – Advanced forensics, malware analysis, threat hunting, and emergency response
Strategic and Business Skills (Years 4-8):
- Risk Management – Quantitative risk assessment, business impact analysis, security metrics development
- Compliance Expertise – Deep knowledge of regulatory frameworks and implementation strategies
- Architecture Design – Enterprise security architecture, zero trust implementation, strategic planning
- Communication Skills – Executive reporting, stakeholder management, security awareness training
Leadership and Innovation (Years 8+):
- Team Leadership – Security team building, talent development, cross-functional collaboration
- Business Strategy – Security program development, budget management, vendor relations
- Industry Influence – Conference speaking, security research, thought leadership, community involvement
- Innovation Leadership – Emerging technology adoption, security product development, startup advising
Emerging Opportunities and Future Trends
High-Growth Cybersecurity Specializations:
- AI/ML Security – Adversarial machine learning, AI model protection, automated threat detection
- IoT and Edge Security – Device security, edge computing protection, industrial control system security
- Privacy Engineering – Privacy by design, data protection, consent management, privacy automation
- DevSecOps – Security automation, secure CI/CD, infrastructure as code security, container security
- Quantum Cryptography – Post-quantum cryptography, quantum key distribution, quantum-safe algorithms
Market Trends Creating New Opportunities:
- Zero Trust Architecture – Identity-centric security, micro-segmentation, continuous verification
- Cloud Security Posture Management – Multi-cloud security, configuration management, compliance automation
- Extended Detection and Response (XDR) – Integrated security operations, automated response, threat hunting
Security Orchestration and Response (SOAR) – Incident response automation, playbook development, case management
📈 Grow Your Cybersecurity Career — Explore Advanced Cybersecurity Roadmaps →
8. Success Stories from Our Students
Ankit Sharma – From Network Administrator to Security Architect
Background: 5 years as network administrator with CCNA certification and basic security exposure
Challenge: Limited security knowledge preventing advancement to cybersecurity specialist roles
Transformation Strategy: Systematic progression from networking foundation to advanced security architecture
Timeline: 16 months from cybersecurity fundamentals to security architect position
Current Position: Senior Security Architect at Accenture Cyber Defense
Salary Progression: ₹8.5 LPA → ₹14.2 LPA → ₹22.8 LPA → ₹35.5 LPA (over 28 months)
Ankit’s Security Evolution:
- Foundation Building – Leveraged networking knowledge to understand network security and perimeter defense
- Tool Mastery – Became expert in Splunk SIEM, Nessus vulnerability scanning, Metasploit penetration testing
- Cloud Security Focus – Specialized in AWS and Azure security architecture and implementation
- Compliance Expertise – Developed deep knowledge of ISO 27001, NIST Framework, and PCI DSS
Key Success Factors:
- Practical Application – “I built a comprehensive home lab to practice every concept I learned, from SIEM configuration to penetration testing.”
- Certification Strategy – “I earned Security+, CEH, and AWS Security certifications within 18 months, demonstrating commitment to employers.”
- Business Focus – “I learned to speak in terms of business risk and ROI rather than just technical vulnerabilities.”
Current Impact: Leading security architecture for Fortune 500 clients, managing multi-million dollar security transformation projects, responsible for protecting assets worth $50+ billion across client portfolio.
Priya Gupta – From IT Support to Cybersecurity Consultant
Background: 3 years in IT support and help desk with strong troubleshooting skills but limited security experience
Challenge: Wanted to transition from reactive support to proactive security and eventual consulting
Strategic Approach: Combined customer service skills with technical security expertise for consulting success
Timeline: 20 months from security fundamentals to independent cybersecurity consultant
Career Trajectory: IT Support → SOC Analyst → Security Engineer → Senior Consultant → Independent Practice
Current Role: Principal Cybersecurity Consultant serving SME clients
Compensation and Business Growth:
- Pre-transition: ₹4.8 LPA (Senior IT Support Specialist)
- Year 1: ₹11.5 LPA (SOC Analyst with threat hunting specialization)
- Year 2: ₹18.2 LPA (Security Engineer focusing on incident response)
- Current: ₹1,85,000/month average (Independent consultant with 15+ active clients)
Priya’s Consulting Excellence:
- SME Specialization – Focused on small and medium enterprises lacking dedicated security teams
- Practical Security – Developed cost-effective security solutions appropriate for SME budgets and capabilities
- Compliance Services – Specialized in ISO 27001, PCI DSS, and GDPR implementation for growing businesses
- Incident Response – Built reputation through effective incident response and forensic analysis services
Consulting Business Achievements:
- Client Portfolio – 25+ active clients across healthcare, finance, manufacturing, and professional services
- Service Expansion – Evolved from security assessments to comprehensive managed security services
- Industry Recognition – Regularly invited to speak at cybersecurity conferences and business forums
- Team Growth – Built team of 4 specialized consultants handling different aspects of cybersecurity
Success Philosophy: “My support background taught me to understand business operations and communicate with non-technical stakeholders. When I added cybersecurity expertise, I could provide security solutions that actually worked for real businesses.”
Rohit Patel – From Software Developer to Penetration Testing Expert
Background: 4 years as Java developer with strong programming skills but limited security knowledge
Challenge: Interested in ethical hacking but needed to transition from development to offensive security
Technical Transition: Leveraged programming expertise to excel in advanced penetration testing and tool development
Timeline: 14 months from basic security concepts to senior penetration tester role
Career Evolution: Software Developer → Security Researcher → Penetration Tester → Senior Ethical Hacker
Current Position: Lead Penetration Tester at Rapid7
Technical Innovation and Recognition:
- Tool Development – Created custom penetration testing tools and exploits used by security community
- Research Contributions – Discovered and reported 15+ CVEs in commercial software applications
- Advanced Techniques – Specialized in web application security, mobile security, and IoT penetration testing
- Training and Mentorship – Developed penetration testing curriculum and trained 20+ junior security professionals
Professional Growth and Compensation:
- Pre-transition: ₹9.8 LPA (Senior Java Developer)
- 6 months: ₹15.2 LPA (Security Researcher with vulnerability discovery focus)
- 12 months: ₹24.5 LPA (Penetration Tester with advanced web app expertise)
- Current: ₹42.8 LPA + bug bounty income (Lead Penetration Tester with research responsibilities)
Penetration Testing Excellence:
- Methodology Innovation – Developed automated testing frameworks reducing assessment time by 60%
- Client Impact – Helped clients prevent potential breaches worth $20+ million through security assessments
- Industry Leadership – Regular speaker at security conferences, published security research papers
- Community Contribution – Active in bug bounty programs, contributing to open-source security tools
Technical Insights: “Programming skills gave me a deep understanding of how applications work, which is essential for finding sophisticated vulnerabilities. The combination of development experience and security knowledge created a unique advantage in penetration testing.”
9. Common Challenges and Solutions
Challenge 1: Staying Current with Rapidly Evolving Threat Landscape
Problem: Cybersecurity threats evolve constantly, making it difficult to stay current with new attack techniques and defense strategies
Impact: Outdated knowledge, ineffective security controls, missed threat detection, career stagnation
Symptoms: Unfamiliarity with recent attack campaigns, outdated security tools, limited threat intelligence awareness
Continuous Learning Strategy:
Threat Intelligence Integration:
#!/usr/bin/env python3
“””
Automated Threat Intelligence Aggregation System
Collects threat intelligence from multiple sources and generates actionable insights
“””
import requests
import json
import csv
from datetime import datetime, timedelta
import hashlib
class ThreatIntelligenceAggregator:
def __init__(self):
self.sources = {
‘mitre_attack’: ‘https://raw.githubusercontent.com/mitre/cti/master/enterprise-attack/enterprise-attack.json’,
‘cisa_alerts’: ‘https://www.cisa.gov/cybersecurity-advisories/aa22-047a’,
‘sans_isc’: ‘https://isc.sans.edu/api/threats’,
‘otx_alienvault’: ‘https://otx.alienvault.com/api/v1/indicators/export’
}
self.indicators = []
self.techniques = []
def collect_mitre_techniques(self):
“””Collect MITRE ATT&CK techniques and tactics”””
try:
response = requests.get(self.sources[‘mitre_attack’], timeout=30)
attack_data = response.json()
for obj in attack_data.get(‘objects’, []):
if obj.get(‘type’) == ‘attack-pattern’:
technique = {
‘id’: obj.get(‘external_references’, [{}])[0].get(‘external_id’),
‘name’: obj.get(‘name’),
‘description’: obj.get(‘description’, ”),
‘tactics’: [phase[‘phase_name’] for phase in obj.get(‘kill_chain_phases’, [])],
‘updated’: datetime.now().isoformat()
}
self.techniques.append(technique)
except Exception as e:
print(f”Error collecting MITRE data: {e}”)
def collect_threat_indicators(self):
“””Collect indicators of compromise from various sources”””
# Implement IOC collection from multiple threat intelligence feeds
indicators = [
{
‘type’: ‘domain’,
‘value’: ‘malicious-domain.com’,
‘confidence’: ‘high’,
‘source’: ‘manual_analysis’,
‘first_seen’: datetime.now().isoformat(),
‘tags’: [‘malware’, ‘c2’]
}
]
self.indicators.extend(indicators)
def generate_daily_brief(self):
“””Generate daily threat intelligence brief”””
brief = {
‘date’: datetime.now().strftime(‘%Y-%m-%d’),
‘new_techniques’: len([t for t in self.techniques if
datetime.fromisoformat(t[‘updated’]).date() == datetime.now().date()]),
‘new_indicators’: len([i for i in self.indicators if
datetime.fromisoformat(i[‘first_seen’]).date() == datetime.now().date()]),
‘top_threats’: self._analyze_trending_threats(),
‘recommendations’: self._generate_recommendations()
}
return brief
def _analyze_trending_threats(self):
“””Analyze trending threat patterns”””
# Implement threat trend analysis
return [‘Ransomware targeting healthcare’, ‘Supply chain attacks’, ‘Cloud misconfigurations’]
def _generate_recommendations(self):
“””Generate actionable security recommendations”””
return [
‘Update incident response procedures for ransomware’,
‘Review third-party vendor security assessments’,
‘Audit cloud security configurations’
]
# Usage
if __name__ == “__main__”:
aggregator = ThreatIntelligenceAggregator()
aggregator.collect_mitre_techniques()
aggregator.collect_threat_indicators()
daily_brief = aggregator.generate_daily_brief()
# Email brief to security team
with open(f”threat_brief_{datetime.now().strftime(‘%Y%m%d’)}.json”, ‘w’) as f:
json.dump(daily_brief, f, indent=2)
Professional Development Framework:
- Daily Learning Routine – 30 minutes daily reading security news, threat reports, vulnerability disclosures
- Weekly Deep Dives – One hour weekly studying new attack techniques, security tools, or compliance updates
- Monthly Hands-On Practice – Dedicated lab time practicing new tools, techniques, or technologies
- Quarterly Skill Assessment – Evaluate knowledge gaps and plan learning priorities for next quarter
Challenge 2: Building Practical Experience Without Access to Enterprise Security Tools
Problem: Many security tools and scenarios require enterprise environments that individuals cannot afford or access
Challenge: Difficulty gaining hands-on experience with commercial tools, real incident response, enterprise scale
Solution: Strategic use of free tools, cloud credits, and simulation environments
Practical Experience Development Strategy:
Home Security Lab Setup:
#!/bin/bash
# Comprehensive Security Lab Setup Script
# Create isolated network environment
sudo apt update && sudo apt upgrade -y
# Install virtualization platform
sudo apt install -y virtualbox vagrant docker.io docker-compose
# Security tools installation
echo “Installing security tools…”
# SIEM and log analysis
docker run -d –name splunk -p 8000:8000 -e SPLUNK_START_ARGS=’–accept-license’ splunk/splunk:latest
docker run -d –name elasticsearch -p 9200:9200 -e “discovery.type=single-node” docker.elastic.co/elasticsearch/elasticsearch:7.15.0
docker run -d –name kibana -p 5601:5601 docker.elastic.co/kibana/kibana:7.15.0
# Vulnerability scanning
wget https://www.tenable.com/downloads/api/v1/public/pages/nessus/downloads/12345/download?i_agree_to_tenable_license_agreement=true -O nessus.deb
sudo dpkg -i nessus.deb
sudo systemctl start nessusd
# Network security tools
sudo apt install -y nmap wireshark tcpdump nikto dirb gobuster
# Web application security
sudo apt install -y burpsuite zaproxy sqlmap
# Penetration testing framework
git clone https://github.com/rapid7/metasploit-framework.git
cd metasploit-framework && bundle install
# Digital forensics
sudo apt install -y autopsy sleuthkit volatility
# Create vulnerable applications for practice
git clone https://github.com/WebGoat/WebGoat.git
git clone https://github.com/bkimminich/juice-shop.git
docker run -d -p 3000:3000 bkimminich/juice-shop
# Malware analysis environment
sudo apt install -y clamav rkhunter chkrootkit
git clone https://github.com/cuckoosandbox/cuckoo.git
# Create practice scenarios
mkdir -p ~/security-lab/{scenarios,reports,scripts}
# Generate sample log data for SIEM practice
python3 -c “
import random
import datetime
import json
# Generate sample security events
events = []
for i in range(1000):
event = {
‘timestamp’: (datetime.datetime.now() – datetime.timedelta(hours=random.randint(0, 24))).isoformat(),
‘event_type’: random.choice([‘login_failure’, ‘malware_detected’, ‘suspicious_network’, ‘policy_violation’]),
‘source_ip’: f'{random.randint(1,255)}.{random.randint(1,255)}.{random.randint(1,255)}.{random.randint(1,255)}’,
‘severity’: random.choice([‘low’, ‘medium’, ‘high’, ‘critical’]),
‘description’: f’Sample security event {i}’
}
events.append(event)
with open(‘sample_security_events.json’, ‘w’) as f:
for event in events:
f.write(json.dumps(event) + ‘\n’)
“
echo “Security lab setup complete!”
echo “Access Splunk at http://localhost:8000 (admin/changeme)”
echo “Access Kibana at http://localhost:5601”
echo “Access WebGoat at http://localhost:8080/WebGoat”
echo “Access Juice Shop at http://localhost:3000”
Cloud Security Practice:
- AWS Free Tier – Practice cloud security configurations, implement security groups, CloudTrail, GuardDuty
- Azure Free Account – Configure Network Security Groups, Azure Security Center, Key Vault
- Google Cloud Credits – Set up Security Command Center, VPC security, Identity and Access Management
- Documentation – Create detailed implementation guides and security architecture diagrams
Challenge 3: Demonstrating Security ROI and Business Value
Problem: Difficulty quantifying the business value of security investments and demonstrating return on investment
Challenge: Security is often viewed as a cost center rather than business enabler
Solution: Develop frameworks for measuring and communicating security business value
Security Business Value Framework:
class SecurityROICalculator:
def __init__(self):
self.metrics = {
‘prevented_incidents’: 0,
‘compliance_cost_avoidance’: 0,
‘productivity_improvements’: 0,
‘reputation_protection’: 0
}
def calculate_breach_cost_avoidance(self, potential_breaches, avg_breach_cost):
“””Calculate cost avoidance from prevented security breaches”””
return potential_breaches * avg_breach_cost
def calculate_compliance_roi(self, compliance_investment, penalty_avoidance, audit_cost_reduction):
“””Calculate ROI from compliance initiatives”””
total_benefits = penalty_avoidance + audit_cost_reduction
roi_percentage = ((total_benefits – compliance_investment) / compliance_investment) * 100
return {
‘investment’: compliance_investment,
‘benefits’: total_benefits,
‘roi_percentage’: roi_percentage,
‘payback_period_months’: (compliance_investment / (total_benefits / 12))
}
def calculate_productivity_impact(self, downtime_prevented_hours, avg_hourly_productivity_cost):
“””Calculate productivity impact of security measures”””
return downtime_prevented_hours * avg_hourly_productivity_cost
def generate_security_scorecard(self, security_investments, business_outcomes):
“””Generate executive security scorecard”””
scorecard = {
‘total_security_investment’: sum(security_investments.values()),
‘quantified_benefits’: {
‘breach_cost_avoidance’: self.calculate_breach_cost_avoidance(
business_outcomes.get(‘prevented_breaches’, 0),
business_outcomes.get(‘avg_breach_cost’, 4200000) # Average cost in INR
),
‘compliance_savings’: business_outcomes.get(‘compliance_cost_avoidance’, 0),
‘productivity_gains’: self.calculate_productivity_impact(
business_outcomes.get(‘downtime_prevented_hours’, 0),
business_outcomes.get(‘hourly_productivity_cost’, 5000)
)
},
‘risk_reduction’: {
‘vulnerability_reduction’: business_outcomes.get(‘vulnerabilities_remediated’, 0),
‘incident_frequency_reduction’: business_outcomes.get(‘incident_reduction_percentage’, 0),
‘mean_time_to_detection_improvement’: business_outcomes.get(‘mttd_improvement_hours’, 0),
‘mean_time_to_response_improvement’: business_outcomes.get(‘mttr_improvement_hours’, 0)
}
}
# Calculate total ROI
total_benefits = sum(scorecard[‘quantified_benefits’].values())
total_investment = scorecard[‘total_security_investment’]
scorecard[‘overall_roi’] = ((total_benefits – total_investment) / total_investment) * 100
return scorecard
# Example usage for security program ROI analysis
def demonstrate_security_value():
calculator = SecurityROICalculator()
# Security investments over the year
investments = {
‘siem_implementation’: 2500000, # ₹25 lakhs
‘security_training’: 800000, # ₹8 lakhs
‘vulnerability_management’: 1200000, # ₹12 lakhs
‘incident_response_team’: 6000000, # ₹60 lakhs
‘compliance_program’: 1500000 # ₹15 lakhs
}
# Business outcomes achieved
outcomes = {
‘prevented_breaches’: 2,
‘avg_breach_cost’: 8500000, # ₹85 lakhs average breach cost
‘compliance_cost_avoidance’: 3000000, # ₹30 lakhs avoided in penalties
‘downtime_prevented_hours’: 500,
‘hourly_productivity_cost’: 8000, # ₹8,000 per hour productivity cost
‘vulnerabilities_remediated’: 450,
‘incident_reduction_percentage’: 65,
‘mttd_improvement_hours’: 12,
‘mttr_improvement_hours’: 8
}
scorecard = calculator.generate_security_scorecard(investments, outcomes)
return scorecard
# Generate executive report
security_scorecard = demonstrate_security_value()
print(f”Security Program ROI: {security_scorecard[‘overall_roi’]:.1f}%”)
print(f”Total Benefits: ₹{security_scorecard[‘quantified_benefits’][‘breach_cost_avoidance’]:,}”)
Challenge 4: Managing Security vs Usability Balance
Problem: Security measures often impact user productivity and system performance
Challenge: Implementing security controls that protect without hindering business operations
Solution: Risk-based security approach with user experience optimization
Balanced Security Implementation:
class SecurityUsabilityOptimizer:
def __init__(self):
self.risk_tolerance = {
‘low’: {‘security_level’: ‘high’, ‘usability_impact’: ‘significant’},
‘medium’: {‘security_level’: ‘medium’, ‘usability_impact’: ‘moderate’},
‘high’: {‘security_level’: ‘low’, ‘usability_impact’: ‘minimal’}
}
def assess_control_impact(self, control_type, user_group, data_sensitivity):
“””Assess security control impact on user experience”””
impact_matrix = {
‘mfa’: {
‘executives’: {‘friction’: ‘medium’, ‘adoption’: ‘high’},
‘developers’: {‘friction’: ‘low’, ‘adoption’: ‘high’},
‘general_users’: {‘friction’: ‘high’, ‘adoption’: ‘medium’}
},
’email_filtering’: {
‘executives’: {‘friction’: ‘low’, ‘adoption’: ‘high’},
‘developers’: {‘friction’: ‘medium’, ‘adoption’: ‘medium’},
‘general_users’: {‘friction’: ‘low’, ‘adoption’: ‘high’}
},
‘endpoint_protection’: {
‘executives’: {‘friction’: ‘medium’, ‘adoption’: ‘medium’},
‘developers’: {‘friction’: ‘high’, ‘adoption’: ‘low’},
‘general_users’: {‘friction’: ‘low’, ‘adoption’: ‘high’}
}
}
return impact_matrix.get(control_type, {}).get(user_group, {})
def design_adaptive_security(self, user_profile, access_context, risk_factors):
“””Design adaptive security controls based on context”””
base_score = 50 # Start with medium security
# Adjust based on user profile
if user_profile.get(‘role’) == ‘admin’:
base_score += 20
elif user_profile.get(‘role’) == ‘executive’:
base_score += 15
# Adjust based on access context
if access_context.get(‘location’) == ‘outside_office’:
base_score += 15
if access_context.get(‘device_trust’) == ‘low’:
base_score += 20
if access_context.get(‘time’) == ‘outside_hours’:
base_score += 10
# Adjust based on risk factors
base_score += risk_factors.get(‘recent_threats’, 0) * 5
base_score += risk_factors.get(‘data_sensitivity’, 0) * 10
# Determine security controls
if base_score >= 80:
return {
‘authentication’: ‘mfa_required’,
‘session_timeout’: 15, # minutes
‘monitoring_level’: ‘high’,
‘access_restrictions’: [‘time_based’, ‘location_based’]
}
elif base_score >= 60:
return {
‘authentication’: ‘mfa_optional’,
‘session_timeout’: 30,
‘monitoring_level’: ‘medium’,
‘access_restrictions’: [‘location_based’]
}
else:
return {
‘authentication’: ‘standard’,
‘session_timeout’: 60,
‘monitoring_level’: ‘standard’,
‘access_restrictions’: []
}
def optimize_security_workflow(self, security_requirements, usability_constraints):
“””Optimize security implementation for better user experience”””
optimizations = []
if ‘password_policy’ in security_requirements:
if usability_constraints.get(‘user_complaints’) > 50:
optimizations.append({
‘change’: ‘implement_sso’,
‘benefit’: ‘reduce_password_fatigue’,
‘security_impact’: ‘maintain_or_improve’
})
if ’email_encryption’ in security_requirements:
optimizations.append({
‘change’: ‘automatic_encryption_based_on_rules’,
‘benefit’: ‘transparent_to_users’,
‘security_impact’: ‘maintain’
})
return optimizations
# Example implementation
def implement_balanced_security():
optimizer = SecurityUsabilityOptimizer()
# Example user accessing sensitive data
user_profile = {
‘role’: ‘financial_analyst’,
‘trust_level’: ‘medium’,
‘training_completed’: True
}
access_context = {
‘location’: ‘home_office’,
‘device_trust’: ‘medium’,
‘time’: ‘business_hours’,
‘network’: ‘vpn_connected’
}
risk_factors = {
‘recent_threats’: 2, # Recent phishing attempts
‘data_sensitivity’: 8, # Highly sensitive financial data
‘compliance_requirements’: [‘sox’, ‘pci’]
}
adaptive_controls = optimizer.design_adaptive_security(
user_profile, access_context, risk_factors
)
return adaptive_controls
# Generate optimized security controls
security_controls = implement_balanced_security()
print(“Adaptive Security Controls:”, security_controls)
10. Your Next Steps
Week 1: Cybersecurity Foundation and Environment Setup
Day 1-2: Cybersecurity Landscape Assessment
- Threat Landscape Study – Research current cyber threats, attack techniques, notable security breaches
- Career Path Exploration – Understand different cybersecurity roles, specializations, and progression paths
- Industry Requirements – Research job postings, required skills, certifications, and salary ranges
- Learning Environment Setup – Install VirtualBox, create isolated network for security testing
Day 3-4: Networking and Security Fundamentals
- Network Security Basics – TCP/IP fundamentals, network protocols, basic security concepts
- Operating System Security – Windows and Linux security models, user management, access controls
- Security Frameworks – Introduction to NIST, ISO 27001, OWASP, and other security standards
- Threat Modeling Concepts – Understanding attack vectors, threat actors, and risk assessment
Day 5-7: Professional Development and Community Engagement
- Certification Planning – Research Security+, CEH, CISSP and other relevant certifications
- Professional Network Building – Join cybersecurity communities, LinkedIn groups, local meetups
- Learning Resources – Identify quality cybersecurity training materials, books, online courses
- Home Lab Planning – Design comprehensive security lab environment for hands-on practice
Month 1: Core Security Technologies and Tools
Week 1-2: Security Tools and Technologies
- SIEM Fundamentals – Install Splunk free version, learn basic log analysis and correlation
- Vulnerability Scanning – Practice with Nessus Essentials, OpenVAS, basic vulnerability assessment
- Network Security – Configure firewalls, understand IDS/IPS, practice network segmentation
- Endpoint Protection – Antivirus, endpoint detection and response, host-based security
Week 3-4: Hands-On Security Practice
- Penetration Testing Basics – Kali Linux introduction, Metasploit basics, ethical hacking principles
- Web Application Security – OWASP Top 10, Burp Suite basics, SQL injection, XSS testing
- Digital Forensics – Evidence preservation, disk imaging, memory analysis, forensic tools
- Incident Response – Response procedures, containment strategies, documentation requirements
Month-End Project: “Home Network Security Assessment”
- Perform comprehensive security audit of personal network infrastructure
- Identify vulnerabilities, misconfigurations, and security gaps
- Implement security controls and monitoring solutions
- Document findings and remediation steps in professional report format
Month 2: Advanced Security Operations and Compliance
Week 1-2: Security Operations Center (SOC)
- SIEM Advanced – Custom dashboards, correlation rules, automated alerting, threat hunting
- Log Analysis – Advanced log correlation, anomaly detection, behavioral analysis
- Threat Intelligence – IOC management, threat feeds integration, attribution analysis
- Incident Coordination – Multi-team coordination, stakeholder communication, escalation procedures
Week 3-4: Compliance and Risk Management
- Regulatory Frameworks – ISO 27001, NIST, PCI DSS, GDPR implementation requirements
- Risk Assessment – Quantitative and qualitative risk analysis, business impact assessment
- Audit Preparation – Documentation requirements, evidence collection, compliance reporting
- Policy Development – Security policies, procedures, awareness training programs
Advanced Learning Goals:
- SOC Analyst Skills – Advanced threat detection, incident analysis, forensic investigation
- Compliance Expertise – Framework implementation, audit coordination, risk management
- Business Communication – Executive reporting, stakeholder management, risk communication
- Technical Documentation – Professional security documentation, process improvement
Month 3: Cloud Security and Modern Architectures
Week 1-2: Cloud Security Implementation
- AWS Security – IAM, Security Groups, CloudTrail, GuardDuty, comprehensive security architecture
- Azure Security – Network Security Groups, Security Center, Key Vault, threat protection
- Multi-Cloud Security – Unified security management, configuration consistency, monitoring
- Container Security – Docker security, Kubernetes security, container vulnerability scanning
Week 3-4: Modern Security Challenges
- Zero Trust Architecture – Identity verification, micro-segmentation, continuous monitoring
- DevSecOps – Secure CI/CD pipelines, infrastructure as code security, automated testing
- IoT Security – Device management, secure communications, firmware security
- AI/ML Security – Model security, adversarial attacks, privacy-preserving techniques
Practical Implementation Focus:
- Cloud Security Project – Multi-cloud security implementation with monitoring and compliance
- Zero Trust Design – Comprehensive zero trust architecture plan for medium organization
- Automation Development – Python scripts for security automation and incident response
- Advanced Threat Simulation – Red team exercises and advanced persistent threat simulation
Long-Term Milestones (6-12 Months)
Professional Certification Achievement:
- Foundation Certifications – Security+, Network+, or equivalent vendor certifications
- Advanced Certifications – CEH, CISSP, CISM, or specialized cloud security certifications
- Continuous Education – Regular training updates, conference attendance, industry engagement
- Specialization Development – Choose focus area and develop deep expertise
Professional Portfolio and Experience:
- Comprehensive Portfolio – 5-7 security projects demonstrating increasing complexity and business impact
- Industry Involvement – Security community participation, volunteer work, conference speaking
- Professional Network – Strong relationships with cybersecurity professionals and potential employers
- Thought Leadership – Blog writing, research publications, security tool contributions
Career Transition and Growth:
- Resume Optimization – Security-focused resume with quantified achievements and technical skills
- Interview Preparation – Technical interview practice, security scenario discussions, portfolio presentation
- Job Market Navigation – Target company research, networking utilization, salary negotiation preparation
- Advanced Opportunities – Senior security roles, specialization positions, leadership track preparation
🌐 Need Help? Explore Resources → Roadmaps → Interview Guides → Courses!
Conclusion
Cybersecurity engineering represents one of the most critical and rewarding career paths in today’s digital economy, combining technical expertise with strategic thinking to protect organizations from increasingly sophisticated threats. As cyber attacks become more frequent and damaging, and regulatory requirements continue to expand, skilled cybersecurity professionals enjoy exceptional career opportunities, premium compensation, and the satisfaction of safeguarding critical digital assets and infrastructure.
The journey from cybersecurity beginner to professional typically requires 4-6 months of intensive learning and hands-on practice, but the investment delivers exceptional returns through immediate career advancement opportunities and long-term job security. Unlike many technology fields that may experience market fluctuations, cybersecurity demand continues to grow across all industries and economic conditions, making it one of the most recession-proof and future-secure career choices available.
Critical Success Factors for Cybersecurity Excellence:
- Continuous Learning Commitment – Stay current with rapidly evolving threats, tools, and regulatory requirements
- Hands-On Technical Skills – Master security tools, frameworks, and practical implementation techniques
- Business Risk Understanding – Connect technical security measures to business objectives and risk tolerance
- Professional Communication – Translate complex security concepts into business language and actionable recommendations
- Ethical Foundation – Maintain strong ethical standards and commitment to protecting digital privacy and security
The most successful cybersecurity professionals combine deep technical knowledge with business acumen and communication skills. As organizations increasingly recognize cybersecurity as a business enabler rather than just a cost center, security professionals who can bridge technical implementation with strategic business value will be most valued and well-compensated.
Whether you choose security operations specialization, penetration testing expertise, compliance and risk management focus, or security architecture leadership, cybersecurity skills provide a foundation for diverse high-impact career opportunities including consulting, research, product development, and executive leadership roles.
Ready to launch your cybersecurity career and protect the digital world?
Explore our comprehensive Cybersecurity Engineering Program designed for aspiring security professionals and career changers:
4-month intensive curriculum covering security fundamentals, advanced threat detection, cloud security, and compliance frameworks
Hands-on lab environment with enterprise security tools, vulnerable applications, and incident response simulations
Industry certifications preparation for Security+, CEH, and CISSP with practice exams and expert guidance
Real-world projects including security assessments, SOC implementation, and incident response scenarios
Job placement assistance with resume optimization, technical interview preparation, and security industry connections
Expert mentorship from certified security professionals with CISSP, CISM, and specialized industry experience
Lifetime learning support including threat intelligence updates, tool training, and career advancement guidance
Unsure which cybersecurity specialization aligns with your background and career goals? Schedule a free cybersecurity consultation with our security experts to receive personalized guidance and a customized learning roadmap.
Connect with our cybersecurity community: Join our Cybersecurity Professionals WhatsApp Group with 220+ students, alumni, and working security professionals for daily learning support, threat intelligence sharing, and job referrals
