Cyber Security Interview Questions Preparation Guide
💡 Kickstart Your Cybersecurity Journey — Follow Our Complete Roadmap!
🧭 Explore Cybersecurity Roadmap →

✅ Module 1: 220+ Cyber Security Interview Questions & Answers
✅ Module 2: 50 Self-Preparation Prompts Using ChatGPT
✅ Module 3: Communication Skills and Behavioral Interview Preparation
✅ Module 4: Additional Preparation Elements (Pre-Interview, During, Post-Interview, Resume Tips, Common Mistakes)
📚 Want all tech interview prep guides in one place? 🔗 Browse All Interview Resources →
Module 1: 220+ Technical Interview Questions & Answers
- Cyber Security Fundamentals Questions 1-25
- Linux Fundamentals for Cyber Security Questions 26-50
- Networking Fundamentals Questions 51-85
- Web Application Security Questions 86-125
- Cryptography Questions 126-150
- Penetration Testing & Ethical Hacking Questions 151-180
- Security Operations Centre (SOC) Questions 181-205
- Active Directory & Windows Security Questions 206-220
For Daily Preparation:
- Study 1 section per day (approximately 25-35 questions)
- Complete all 8 sections in 8 days
- Revise 2-3 sections daily after first round
For Quick Revision:
- Focus on sections matching your job role (SOC = Section 7, Pentesting = Section 6)
- Review questions you marked as difficult
- Practice explaining answers in your own words
For Interview Day:
- Quick scan of all section titles
- Review your weak areas
- Focus on Questions 1-25 (Fundamentals) for confidence boost
🎓 Master Cybersecurity Concepts with Hands-On Training !
Section 1: Cyber Security Fundamentals (Questions 1-25)
Q1. What is Cyber Security?
Cyber Security means protecting computers, networks, mobile devices, and data from digital attacks, damage, or unauthorized access. Think of it as a digital lock and key system that keeps your information safe from hackers and criminals online.
Q2. Why is Cyber Security important today?
Everything is online now—banking, shopping, health records, and personal photos. Hackers constantly try to steal this information to make money or cause harm. Cyber Security protects businesses from losing millions and keeps people’s private information safe.
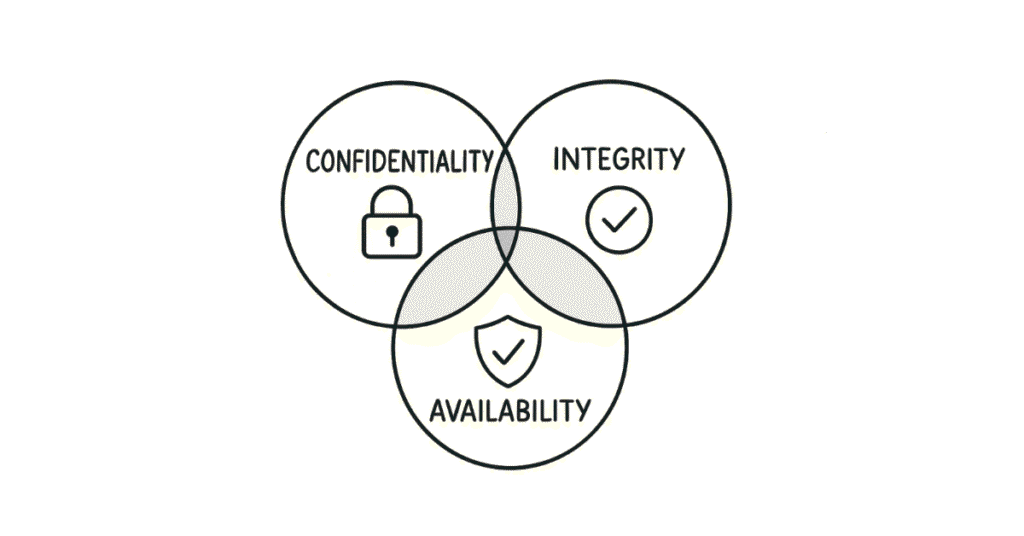
Q3. What are the three main goals of Cyber Security? (CIA Triad)
The CIA Triad stands for:
- Confidentiality: Only authorized people can see the data
- Integrity: Data remains accurate and unchanged
- Availability: Systems work when people need them
Q4. What is the difference between a Threat, Vulnerability, and Risk?
- Threat: A danger that could harm your system (like a hacker)
- Vulnerability: A weakness in your system (like an outdated password)
- Risk: The possibility that a threat will exploit a vulnerability (the chance of getting hacked)
Q5. What are the different types of hackers?
- White Hat Hackers: Good guys who test security with permission
- Black Hat Hackers: Criminals who break into systems illegally
- Grey Hat Hackers: People who hack without permission but don’t cause harm
- Script Kiddies: Beginners using existing tools without deep knowledge
- Hacktivists: Hackers with political or social goals
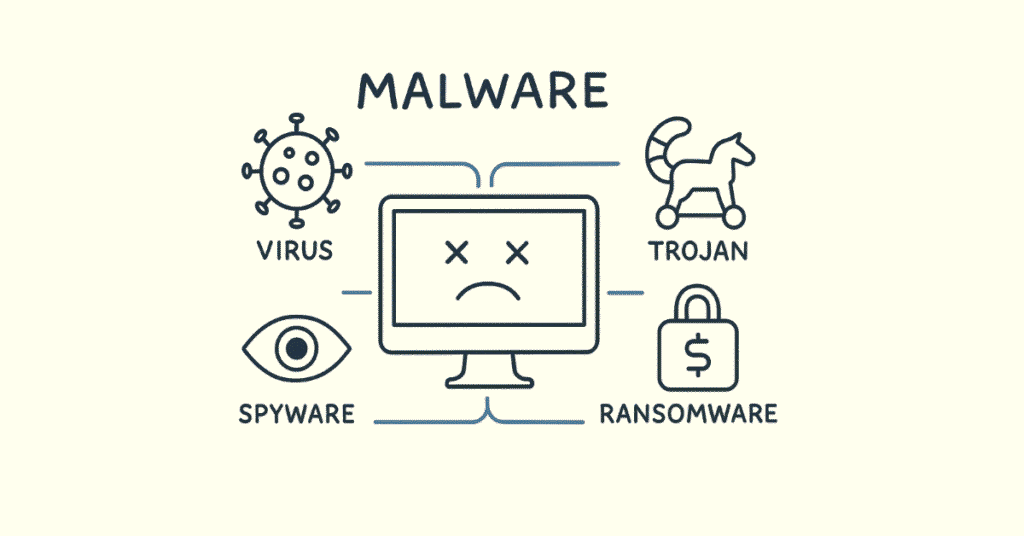
Q6. What is Malware?
Malware is malicious software designed to harm computers. It includes viruses, worms, trojans, ransomware, and spyware. Each type damages systems differently.
Q7. What is the difference between a Virus and a Worm?
- Virus: Needs human action to spread (like opening an email attachment)
- Worm: Spreads automatically without human help through networks
Q8. What is Ransomware?
Ransomware is malware that locks your files and demands money to unlock them. It encrypts everything on your computer, and hackers ask for payment (usually in cryptocurrency) to give you the decryption key.
Q9. What is a Trojan?
A Trojan pretends to be legitimate software but actually contains malicious code. It’s named after the Trojan Horse story where soldiers hid inside a wooden horse. Users unknowingly install it, giving hackers access.
Q10. What is Phishing?
Phishing is a fraud technique where attackers send fake emails or messages pretending to be trusted companies. They trick people into revealing passwords, credit card numbers, or other sensitive information.
Q11. What is Social Engineering?
Social Engineering manipulates people psychologically to give up confidential information. Instead of hacking technology, attackers hack human behavior through trust, fear, or urgency.
Q12. What is a DDoS attack?
DDoS (Distributed Denial of Service) attack floods a website or server with massive traffic from multiple computers, making it crash or become unavailable to real users. It’s like blocking a store entrance with too many people.
Q13. What is a Firewall?
A Firewall is a security system that monitors and controls incoming and outgoing network traffic. It acts as a barrier between trusted internal networks and untrusted external networks, blocking suspicious traffic.
Q14. What are the types of Firewalls?
- Hardware Firewall: Physical device protecting entire networks
- Software Firewall: Program installed on individual computers
- Packet Filtering Firewall: Checks data packets against rules
- Stateful Inspection Firewall: Monitors active connections
- Proxy Firewall: Acts as intermediary between users and internet
- Next-Generation Firewall: Advanced features including application awareness
Q15. What is Encryption?
Encryption converts readable data (plaintext) into unreadable code (ciphertext) using mathematical algorithms. Only someone with the correct key can decrypt and read it. It’s like writing in a secret code.
Q16. What is the difference between Symmetric and Asymmetric Encryption?
- Symmetric Encryption: Uses one key for both encryption and decryption (faster but key sharing is risky)
- Asymmetric Encryption: Uses two keys—public key for encryption and private key for decryption (slower but more secure)
Q17. What is a VPN?
VPN (Virtual Private Network) creates a secure, encrypted connection over the internet. It hides your IP address and location, making your online activity private. Companies use VPNs to let employees securely access office networks remotely.
Q18. What is Two-Factor Authentication (2FA)?
2FA adds an extra security layer beyond passwords. After entering your password, you must provide a second proof of identity—like a code sent to your phone, fingerprint, or security token.
Q19. What is the difference between IDS and IPS?
- IDS (Intrusion Detection System): Monitors network traffic and alerts you about suspicious activity (passive)
- IPS (Intrusion Prevention System): Detects AND automatically blocks threats (active)
Q20. What is a Zero-Day Vulnerability?
A Zero-Day vulnerability is a security flaw in software that hackers discover before the software maker knows about it. There’s “zero days” to fix it because it’s already being exploited.
Q21. What is Penetration Testing?
Penetration Testing (Pen Testing) is ethical hacking where security experts deliberately attack systems with permission to find vulnerabilities before real hackers do. It’s like hiring someone to test if your house locks work.
Q22. What is the difference between Penetration Testing and Vulnerability Assessment?
- Vulnerability Assessment: Scans and identifies weaknesses (makes a list)
- Penetration Testing: Actually exploits weaknesses to see how much damage is possible (tests the locks)
Q23. What is SSL/TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols that encrypt data transmitted between web browsers and servers. Websites using HTTPS have SSL/TLS certificates, showing they’re secure.
Q24. What are Cookies?
Cookies are small text files websites store on your computer to remember information about you—like login details, shopping cart items, or preferences. They make browsing convenient but can track your activity.
Q25. What is a Botnet?
A Botnet is a network of infected computers (called “bots” or “zombies”) controlled remotely by hackers. Attackers use botnets to send spam, steal data, or launch DDoS attacks without the computer owners knowing.
Section 2: Linux Fundamentals for Cyber Security (Questions 26-50)
Q26. Why is Linux important in Cyber Security?
Most servers and security tools run on Linux because it’s open-source, stable, customizable, and has powerful command-line capabilities. Hackers and security professionals both prefer Linux for its flexibility and control.
Q27. What is the Linux File System?
Linux organizes files in a tree structure starting from the root directory “/”. Everything—documents, programs, hardware devices—is treated as a file in Linux.
Q28. What are the important directories in Linux?
- /bin: Essential command binaries
- /etc: Configuration files
- /home: User home directories
- /var: Variable files like logs
- /tmp: Temporary files
- /usr: User programs and utilities
- /root: Root user home directory
Q29. What is the difference between Root and Normal User?
- Root: Superuser with complete system control and all permissions (like an administrator)
- Normal User: Limited permissions, can only access their own files and specific programs
Q30. What are File Permissions in Linux?
Linux files have three permission types for three user categories:
- Read (r): View file contents
- Write (w): Modify file contents
- Execute (x): Run file as program
Permissions apply to: Owner, Group, and Others
Q31. How do you read Linux file permissions?
The format looks like: -rwxr-xr–
- First character: File type (- for file, d for directory)
- Next 3: Owner permissions (rwx = read, write, execute)
- Next 3: Group permissions (r-x = read, execute only)
- Last 3: Others permissions (r– = read only)
Q32. What is the chmod command?
chmod (change mode) modifies file permissions. You can use numbers or symbols:
- chmod 755 file.txt (numeric method)
- chmod u+x file.txt (symbolic method—adds execute permission for user)
Q33. What is the difference between SUID, SGID, and Sticky Bit?
- SUID: File runs with owner’s permissions regardless of who executes it
- SGID: File runs with group’s permissions; new files inherit directory’s group
- Sticky Bit: Only file owner can delete their files in a shared directory
Q34. What is the purpose of /etc/passwd file?
The /etc/passwd file stores basic information about all user accounts—username, user ID, group ID, home directory, and default shell. It’s readable by everyone but doesn’t store actual passwords.
Q35. What is the /etc/shadow file?
The /etc/shadow file stores encrypted password hashes and password policies. Unlike /etc/passwd, only root can read this file, making it more secure.
Q36. What are Environment Variables in Linux?
Environment Variables store system-wide or user-specific information that programs use. Examples include PATH (where system looks for commands) and HOME (user’s home directory path).
Q37. What is the PATH variable?
PATH is an environment variable containing directories where the system searches for executable commands. When you type a command, Linux checks these directories to find and run it.
Q38. What are Cron Jobs?
Cron Jobs are scheduled tasks that run automatically at specified times. Security professionals use them for automated backups, log monitoring, and regular security scans.
Q39. How do you create a Cron Job?
Use the crontab -e command to edit the cron table. The format is:
* * * * * command
(minute) (hour) (day) (month) (weekday)
Q40. What is the purpose of the sudo command?
sudo (superuser do) lets normal users execute commands with root privileges temporarily. It’s safer than logging in as root because it logs who did what.
Q41. What is the difference between su and sudo?
- su: Switches to another user account (usually root) completely
- sudo: Executes single commands with elevated privileges without switching users
Q42. What are Linux Log Files used for?
Log files record system events, errors, and activities. Security analysts examine logs to detect suspicious behavior, troubleshoot problems, and investigate incidents.
Q43. Where are Linux log files located?
Most log files are in the /var/log directory:
- /var/log/syslog: General system logs
- /var/log/auth.log: Authentication attempts
- /var/log/kern.log: Kernel messages
Q44. What is the netstat command?
netstat displays network connections, routing tables, and network statistics. Security professionals use it to identify suspicious connections or open ports.
Q45. What is the ps command?
ps (process status) shows currently running processes. It helps identify unauthorized programs or malware running on the system.
Q46. What is the difference between kill and killall?
- kill: Terminates specific process by process ID (PID)
- killall: Terminates all processes with a specific name
Q47. What is SSH?
SSH (Secure Shell) is an encrypted protocol for securely connecting to remote computers over networks. It replaced insecure protocols like Telnet.
Q48. What is the difference between SSH and Telnet?
- SSH: Encrypted, secure remote connection
- Telnet: Unencrypted, data visible to anyone monitoring the network (never use for sensitive data)
Q49. What is a Shell Script?
A Shell Script is a text file containing Linux commands that execute automatically in sequence. It automates repetitive tasks and security operations.
Q50. What is the grep command?
grep searches for specific patterns in files or output. Security analysts use it to filter log files and find specific information quickly.
Section 3: Networking Fundamentals (Questions 51-85)
Q51. What is a Network?
A Network is a collection of computers and devices connected together to share resources and communicate. It can be as small as home WiFi or as large as the internet.
Q52. What is an IP Address?
IP (Internet Protocol) Address is a unique numerical label assigned to each device on a network. It’s like a home address for computers, helping data reach the correct destination.
Q53. What is the difference between IPv4 and IPv6?
- IPv4: Uses 32-bit addresses (like 192.168.1.1), provides about 4 billion addresses (running out)
- IPv6: Uses 128-bit addresses (like 2001:0db8:85a3::8a2e:0370:7334), provides virtually unlimited addresses
Q54. What are IP Address Classes?
IPv4 addresses are divided into classes:
- Class A: 1.0.0.0 to 126.255.255.255 (large networks)
- Class B: 128.0.0.0 to 191.255.255.255 (medium networks)
- Class C: 192.0.0.0 to 223.255.255.255 (small networks)
- Class D: 224.0.0.0 to 239.255.255.255 (multicast)
- Class E: 240.0.0.0 to 255.255.255.255 (experimental)
Q55. What is a MAC Address?
MAC (Media Access Control) Address is a permanent physical address burned into network hardware at manufacturing. It’s like a serial number for network devices.
Q56. What is the difference between IP Address and MAC Address?
- IP Address: Logical address that can change, works at Network Layer
- MAC Address: Physical address that’s permanent, works at Data Link Layer
Q57. What is a Subnet Mask?
Subnet Mask divides IP addresses into network and host portions. It tells computers which part of an IP address identifies the network and which part identifies the specific device.
Q58. What is a Default Gateway?
Default Gateway is the router that connects your local network to other networks or the internet. When your computer doesn’t know where to send data, it sends it to the default gateway.
Q59. What are Network Topologies?
Network Topology is the physical or logical arrangement of devices:
- Star: All devices connect to a central hub
- Bus: All devices connect to a single cable
- Ring: Devices connect in a circular chain
- Mesh: Every device connects to every other device
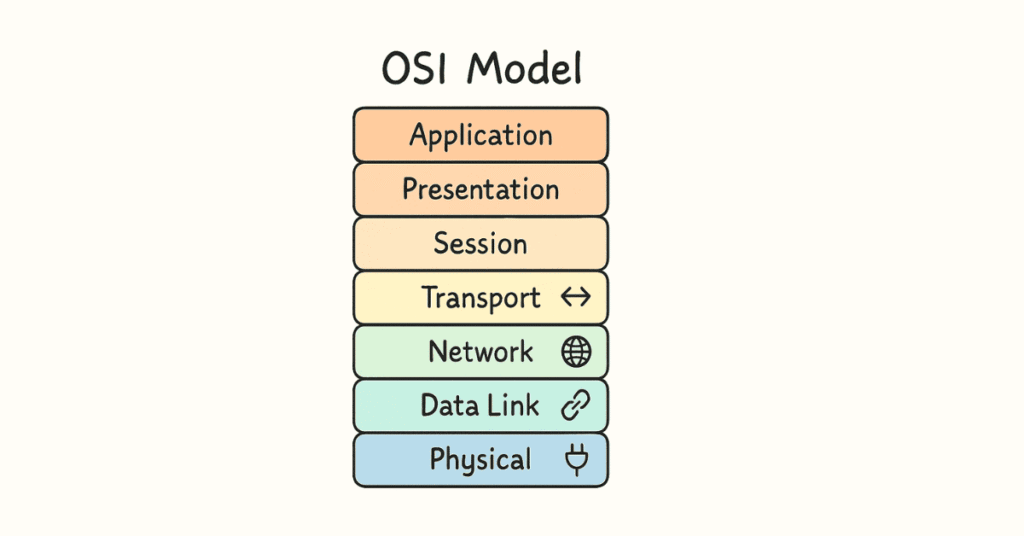
Q60. What is the OSI Model?
OSI (Open Systems Interconnection) Model is a 7-layer framework that standardizes how networks communicate. Each layer has specific functions in data transmission.
Q61. What are the 7 layers of the OSI Model?
From bottom to top:
- Physical Layer: Physical connection (cables, signals)
- Data Link Layer: Node-to-node transfer (MAC addresses, switches)
- Network Layer: Routing and IP addressing
- Transport Layer: End-to-end communication (TCP/UDP)
- Session Layer: Establishes and manages connections
- Presentation Layer: Data formatting and encryption
- Application Layer: User interfaces and applications
Q62. What is the TCP/IP Model?
TCP/IP Model is a 4-layer practical implementation used on the internet:
- Network Access Layer (combines OSI Physical and Data Link)
- Internet Layer (like OSI Network Layer)
- Transport Layer (same as OSI Transport Layer)
- Application Layer (combines OSI Session, Presentation, Application)
Q63. What is the difference between TCP and UDP?
- TCP (Transmission Control Protocol): Connection-oriented, reliable, slower (like registered mail)
- UDP (User Datagram Protocol): Connectionless, faster but less reliable (like throwing a letter over the fence)
Q64. What is a Three-Way Handshake?
Three-Way Handshake establishes TCP connections:
- SYN: Client sends synchronization request
- SYN-ACK: Server acknowledges and sends its own synchronization
- ACK: Client acknowledges server’s response
Connection is now established.
Q65. What is a Port Number?
Port Numbers identify specific applications or services on a computer. They range from 0 to 65535 and help direct traffic to the right program.
Q66. What are Well-Known Ports?
Well-Known Ports (0-1023) are reserved for common services:
- Port 80: HTTP (web traffic)
- Port 443: HTTPS (secure web traffic)
- Port 22: SSH (secure remote access)
- Port 21: FTP (file transfer)
- Port 25: SMTP (email sending)
- Port 53: DNS (domain name resolution)
Q67. What is DNS?
DNS (Domain Name System) translates human-readable domain names (like google.com) into IP addresses that computers understand. It’s like a phonebook for the internet.
Q68. How does DNS work?
When you type a website name:
- Your computer checks its cache
- Asks local DNS server
- If not found, queries root DNS servers
- Gets referred to authoritative DNS server
- Receives IP address
- Connects to website using that IP
Q69. What is ARP?
ARP (Address Resolution Protocol) maps IP addresses to MAC addresses on local networks. When a computer knows an IP address but needs the MAC address to communicate, it uses ARP.
Q70. What is DHCP?
DHCP (Dynamic Host Configuration Protocol) automatically assigns IP addresses to devices joining a network. Instead of manually configuring each device, DHCP does it automatically.
Q71. What is NAT?
NAT (Network Address Translation) allows multiple devices on a private network to share one public IP address when accessing the internet. It saves IP addresses and adds security.
Q72. What is the difference between Hub, Switch, and Router?
- Hub: Broadcasts data to all connected devices (dumb, inefficient)
- Switch: Sends data only to the intended device (smart, efficient)
- Router: Connects different networks and routes traffic between them
Q73. What is a VLAN?
VLAN (Virtual Local Area Network) logically segments a physical network into separate networks. It improves security and performance by isolating traffic.
Q74. What is HTTP?
HTTP (Hypertext Transfer Protocol) is the protocol used to transfer web pages over the internet. When you browse websites, your browser uses HTTP to request and receive content.
Q75. What is the difference between HTTP and HTTPS?
- HTTP: Unencrypted, data visible to attackers (Port 80)
- HTTPS: Encrypted with SSL/TLS, secure (Port 443)
Always look for HTTPS for secure websites.
Q76. What is FTP?
FTP (File Transfer Protocol) transfers files between computers over networks. It’s commonly used to upload websites to servers but isn’t secure without encryption.
Q77. What is SMTP?
SMTP (Simple Mail Transfer Protocol) sends emails between mail servers. When you hit “send” on an email, SMTP handles delivery to the recipient’s mail server.
Q78. What is an ICMP?
ICMP (Internet Control Message Protocol) sends error messages and operational information. The “ping” command uses ICMP to test if a device is reachable.
Q79. What is the Ping command?
Ping tests connectivity between your computer and another device by sending ICMP echo requests. If you get replies, the connection works.
Q80. What is Traceroute?
Traceroute shows the path data packets take to reach a destination, listing every router along the way. It helps diagnose where network problems occur.
Q81. What is a Proxy Server?
A Proxy Server acts as an intermediary between users and the internet. It can filter content, improve performance through caching, and hide user identities.
Q82. What is a Load Balancer?
Load Balancer distributes incoming network traffic across multiple servers to prevent any single server from becoming overwhelmed. It improves performance and reliability.
Q83. What is Wireshark?
Wireshark is a network protocol analyzer that captures and displays network traffic in real-time. Security analysts use it to troubleshoot networks and detect suspicious activity.
Q84. What is a Packet?
A Packet is a small unit of data transmitted over networks. Large data is broken into packets, sent separately, and reassembled at the destination.
Q85. What is Packet Sniffing?
Packet Sniffing captures and analyzes network packets. Security professionals use it legitimately for monitoring, but hackers use it maliciously to steal data on unsecured networks.
🌐 Map Out Networking to Security Analyst Transition 🧭 See Complete Cybersecurity Roadmap →
Section 4: Web Application Security (Questions 86-125)

Q86. What is a Web Application?
A Web Application is software that runs on web servers and users access through browsers (like Gmail, Facebook, online banking). Unlike desktop apps, they don’t need installation.
Q87. What is the OWASP Top 10?
OWASP Top 10 is a list of the most critical web application security risks published by the Open Web Application Security Project. It guides developers and security professionals on what to prioritize.
Q88. What is Broken Access Control?
Broken Access Control lets users access resources or perform actions they shouldn’t be allowed to. For example, changing a URL parameter to view someone else’s private account information.
Q89. What is IDOR (Insecure Direct Object Reference)?
IDOR occurs when applications expose direct references to internal objects (like database keys or filenames) in URLs. Attackers can manipulate these references to access unauthorized data.
Example: Changing profile.php?id=123 to profile.php?id=124 to view another user’s profile.
Q90. What is SQL Injection?
SQL Injection attacks insert malicious SQL code into application inputs. If the application doesn’t validate input properly, attackers can read, modify, or delete database contents.
Q91. How does SQL Injection work?
Normal login query: SELECT * FROM users WHERE username=’admin’ AND password=’pass123′
Malicious input: Username = admin’ — and any password
Resulting query: SELECT * FROM users WHERE username=’admin’ –‘ AND password=’anything’
The — comments out the rest, bypassing password check.
Q92. What are the types of SQL Injection?
- Error-based: Uses error messages to extract database information
- Union-based: Combines malicious query with original using UNION
- Blind SQL Injection: No visible errors, attacker asks true/false questions
- Time-based: Uses database delays to confirm vulnerabilities
Q93. How can you prevent SQL Injection?
- Use prepared statements (parameterized queries)
- Validate and sanitize all user inputs
- Use ORM (Object-Relational Mapping) frameworks
- Implement least privilege for database accounts
- Never show detailed error messages to users
Q94. What is Cross-Site Scripting (XSS)?
XSS injects malicious JavaScript code into web pages viewed by other users. When victims load the page, the attacker’s script executes in their browser, stealing cookies or session data.
Q95. What are the types of XSS?
- Stored XSS: Malicious script permanently stored on target server (like in comments)
- Reflected XSS: Script reflected off server in response (like in search results)
- DOM-based XSS: Vulnerability exists in client-side code, not server-side
Q96. How can you prevent XSS attacks?
- Encode/escape user inputs before displaying
- Validate and sanitize all inputs
- Implement Content Security Policy (CSP) headers
- Use frameworks with built-in XSS protection
- Never insert untrusted data directly into HTML
Q97. What is Cross-Site Request Forgery (CSRF)?
CSRF tricks authenticated users into performing unwanted actions on web applications where they’re logged in. Attackers craft malicious requests that execute with the victim’s credentials.
Example: While logged into your bank, you visit a malicious site that secretly submits a money transfer form using your active session.
Q98. How can you prevent CSRF attacks?
- Use anti-CSRF tokens in forms
- Implement SameSite cookie attribute
- Require re-authentication for sensitive actions
- Validate Referer headers
- Use custom request headers for AJAX calls
Q99. What is Command Injection?
Command Injection executes arbitrary system commands on the server by injecting malicious input into application functions that execute shell commands.
Example: If an application runs ping [user_input], attacker enters google.com && cat /etc/passwd to execute both commands.
Q100. What is XML External Entity (XXE) attack?
XXE exploits vulnerable XML processors that parse external entities. Attackers can read files, perform SSRF attacks, or cause denial of service by including malicious external entities.
Q101. What is Server-Side Request Forgery (SSRF)?
SSRF forces the server to make requests to internal or external resources on the attacker’s behalf. It can expose internal systems not directly accessible from the internet.
Q102. What is a Directory Traversal attack?
Directory Traversal (Path Traversal) accesses files outside the intended directory by manipulating file paths with sequences like ../ to navigate up directories.
Example: download.php?file=../../../../etc/passwd
Q103. What is File Upload vulnerability?
File Upload vulnerabilities occur when applications don’t properly validate uploaded files. Attackers can upload malicious scripts (like web shells) and execute them on the server.
Q104. How can you secure File Uploads?
- Validate file types (check content, not just extension)
- Rename uploaded files randomly
- Store uploads outside web root
- Set restrictive permissions
- Scan files for malware
- Limit file size
Q105. What is Remote File Inclusion (RFI)?
RFI includes remote files (usually from attacker’s server) into application code. If executed, it gives attackers control over the application.
Q106. What is Local File Inclusion (LFI)?
LFI includes existing files from the server into application code. While less dangerous than RFI, it can expose sensitive files or be chained with other vulnerabilities.
Q107. What is Session Hijacking?
Session Hijacking steals or predicts session tokens to impersonate legitimate users. Once hijacked, attackers access the application as the victim without knowing their password.
Q108. What is Cookie Poisoning?
Cookie Poisoning modifies cookie contents to gain unauthorized access or change application behavior. Attackers manipulate cookies before sending them back to the server.
Q109. What is Clickjacking?
Clickjacking tricks users into clicking something different from what they perceive. Attackers overlay invisible frames over legitimate buttons, making users unknowingly perform actions.
Q110. How can you prevent Clickjacking?
- Implement X-Frame-Options header
- Use Content-Security-Policy frame-ancestors directive
- Implement frame-busting JavaScript
- Avoid rendering sensitive actions in frames
Q111. What is Insecure Deserialization?
Insecure Deserialization occurs when applications deserialize untrusted data without proper validation. Attackers can inject malicious objects that execute code or manipulate application logic.
Q112. What is Security Misconfiguration?
Security Misconfiguration happens when security settings aren’t properly defined or maintained. Examples include default passwords, unnecessary features enabled, or verbose error messages revealing system details.
Q113. What are common Security Misconfigurations?
- Default admin credentials not changed
- Directory listing enabled
- Unnecessary services running
- Outdated software versions
- Detailed error messages exposing stack traces
- Missing security headers
Q114. What is an API?
API (Application Programming Interface) allows different software applications to communicate. Web applications use APIs to send and receive data between client and server or integrate third-party services.
Q115. What are common API security issues?
- Broken authentication
- Excessive data exposure
- Lack of rate limiting
- Missing encryption
- Insufficient logging
- Injection flaws
Q116. What is Authentication?
Authentication verifies user identity—confirming you are who you claim to be. Common methods include passwords, biometrics, security tokens, or multi-factor authentication.
Q117. What is Authorization?
Authorization determines what authenticated users can access or do. Even after proving identity, authorization controls which resources and actions are permitted.
Q118. What is the difference between Authentication and Authorization?
- Authentication: Who are you? (Identity verification)
- Authorization: What can you do? (Permission checking)
Example: Username/password verifies identity (authentication), but your role determines if you can delete files (authorization).
Q119. What is OAuth?
OAuth is an authorization framework that allows websites to access user information from other services without sharing passwords. It’s what happens when you “Login with Google” on third-party sites.
Q120. What is JWT (JSON Web Token)?
JWT is a compact, URL-safe token format for securely transmitting information between parties. It’s commonly used for authentication—after logging in, servers issue JWTs that clients include in subsequent requests.
Q121. What is Burp Suite?
Burp Suite is a comprehensive web application security testing platform. It intercepts and modifies HTTP requests, scans for vulnerabilities, and helps penetration testers find security flaws.
Q122. What is OWASP ZAP?
OWASP ZAP (Zed Attack Proxy) is a free, open-source web application security scanner. Like Burp Suite, it finds vulnerabilities by intercepting traffic and performing automated scans.
Q123. What is a Web Application Firewall (WAF)?
WAF monitors, filters, and blocks HTTP traffic to and from web applications. It protects against common attacks like SQL injection and XSS by analyzing requests before they reach the application.
Q124. What is Content Security Policy (CSP)?
CSP is a security header that tells browsers which content sources are legitimate. It helps prevent XSS attacks by restricting where scripts, styles, and other resources can load from.
Q125. What are Security Headers?
Security Headers are HTTP response headers that configure browser security features:
- X-Frame-Options: Prevents clickjacking
- X-XSS-Protection: Enables browser XSS filters
- Strict-Transport-Security: Enforces HTTPS
- X-Content-Type-Options: Prevents MIME-sniffing
🧠 Want to Learn Ethical Hacking Step-by-Step?
Section 5: Web Application Security (Questions 86-125)
Q126. What is Cryptography?
Cryptography is the science of securing communication through encryption and decryption. It transforms readable data into unreadable formats that only authorized parties can decode.
Q127. What is Plaintext and Ciphertext?
- Plaintext: Original, readable message before encryption
- Ciphertext: Encrypted, unreadable message after encryption
Q128. What is an Encryption Key?
An Encryption Key is a piece of information (usually a string of characters) used by encryption algorithms to transform plaintext into ciphertext and back.
Q129. What is Symmetric Encryption?
Symmetric Encryption uses the same key for both encryption and decryption. It’s faster but requires secure key exchange between parties.
Q130. Give examples of Symmetric Encryption algorithms.
- AES (Advanced Encryption Standard): Most widely used, very secure
- DES (Data Encryption Standard): Older, now considered weak
- 3DES (Triple DES): Applies DES three times, more secure than DES
- Blowfish: Fast, free alternative to DES
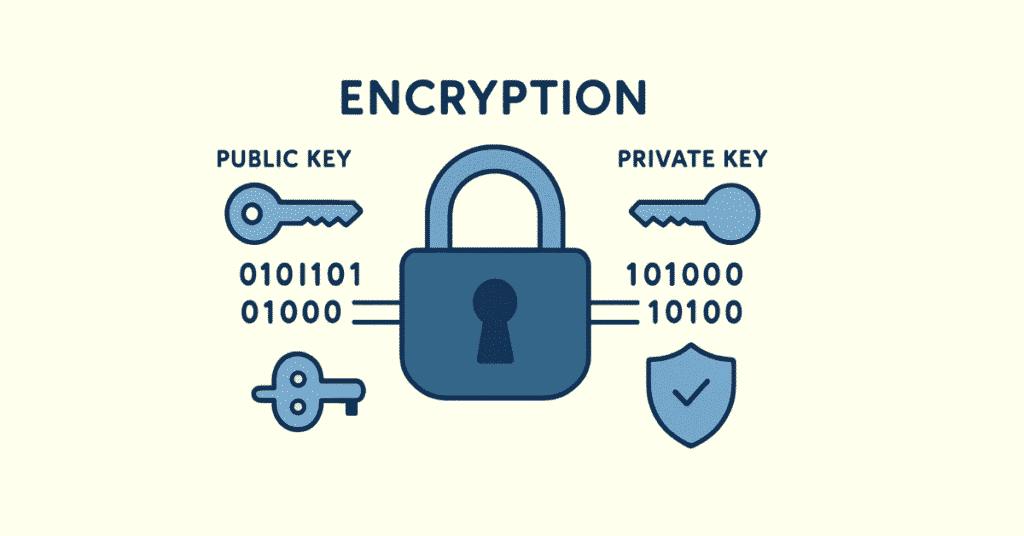
Q131. What is Asymmetric Encryption?
Asymmetric Encryption uses two different keys—a public key for encryption and a private key for decryption. Anyone can encrypt with the public key, but only the private key holder can decrypt.
Q132. Give examples of Asymmetric Encryption algorithms.
- RSA (Rivest-Shamir-Adleman): Most popular, used in SSL/TLS
- ECC (Elliptic Curve Cryptography): More efficient than RSA
- Diffie-Hellman: Used for secure key exchange
Q133. What is the advantage of Asymmetric Encryption?
No need to share secret keys—you can publicly distribute your public key. Anyone can encrypt messages only you can decrypt, solving the key distribution problem.
Q134. What is Hashing?
Hashing converts data into a fixed-size string (hash value) using a one-way function. Unlike encryption, hashing cannot be reversed—you cannot get the original data from the hash.
Q135. What is a Hash Function?
A Hash Function is a mathematical algorithm that produces a unique fixed-size output (hash) from any input. The same input always produces the same hash, but even tiny changes create completely different hashes.
Q136. Give examples of Hash Functions.
- MD5: 128-bit hash, fast but weak (not recommended)
- SHA-1: 160-bit hash, also considered weak now
- SHA-256: Part of SHA-2 family, 256-bit hash, currently secure
- SHA-3: Latest standard, more secure
- bcrypt: Designed for passwords, includes salt
Q137. What is the difference between Encryption and Hashing?
- Encryption: Two-way process, can be decrypted back to original
- Hashing: One-way process, cannot retrieve original data
Use encryption for confidentiality, hashing for integrity verification and password storage.
Q138. What is a Salt in password hashing?
Salt is random data added to passwords before hashing. It ensures identical passwords produce different hashes, preventing rainbow table attacks and making cracking much harder.
Q139. What is a Rainbow Table attack?
Rainbow Table attack uses precomputed hash databases to crack password hashes quickly. Attackers look up hashes in these tables instead of recalculating them, dramatically speeding up cracking.
Q140. What is a Digital Signature?
Digital Signature verifies message authenticity and integrity using asymmetric cryptography. The sender encrypts a hash of the message with their private key; recipients decrypt with the sender’s public key to verify.
Q141. How do Digital Signatures work?
- Sender creates hash of message
- Sender encrypts hash with private key (creating signature)
- Sender sends message and signature
- Recipient decrypts signature with sender’s public key
- Recipient hashes received message
- If hashes match, signature is valid
Q142. What is a Digital Certificate?
Digital Certificate is an electronic document issued by Certificate Authorities (CAs) that binds a public key to an identity. It verifies that a public key belongs to a specific person or organization.
Q143. What is a Certificate Authority (CA)?
Certificate Authority is a trusted organization that issues and manages digital certificates. They verify identities before issuing certificates, acting as a trusted third party.
Q144. What is Public Key Infrastructure (PKI)?
PKI is a framework of policies, procedures, hardware, and software to manage digital certificates and public-key encryption. It enables secure communication, authentication, and data integrity.
Q145. What is Diffie-Hellman Key Exchange?
Diffie-Hellman is a method for two parties to securely establish a shared secret key over an insecure channel. Even if someone intercepts the communication, they cannot determine the shared key.
Q146. What is Base64 Encoding?
Base64 Encoding converts binary data into ASCII text format using 64 characters. It’s not encryption—anyone can decode it. It’s used to safely transmit binary data through text-only channels.
Q147. What is URL Encoding?
URL Encoding converts special characters into a format that can be transmitted over the internet in URLs. Spaces become %20, special characters get converted to %XX format.
Q148. What is the difference between Encoding and Encryption?
- Encoding: Makes data usable in different contexts (like Base64), easily reversible, not for security
- Encryption: Secures data with keys, requires key to reverse, specifically for security
Q149. What is End-to-End Encryption?
End-to-End Encryption ensures only communicating users can read messages—not even the service provider. Data is encrypted on sender’s device and only decrypted on recipient’s device.
Q150. What is Perfect Forward Secrecy?
Perfect Forward Secrecy ensures that session keys aren’t compromised even if the server’s private key is compromised later. Each session uses unique keys that aren’t derived from long-term keys.
Section 6: Penetration Testing & Ethical Hacking (Questions 151-180)

Q151. What is Penetration Testing?
Penetration Testing is authorized simulated cyberattack on systems to evaluate security. Ethical hackers deliberately try to breach security to find vulnerabilities before malicious hackers do.
Q152. What are the phases of Penetration Testing?
- Reconnaissance: Gathering information about target
- Scanning: Identifying open ports, services, vulnerabilities
- Gaining Access: Exploiting vulnerabilities to enter system
- Maintaining Access: Installing backdoors for future access
- Covering Tracks: Removing evidence of intrusion
- Reporting: Documenting findings and recommendations
Q153. What is the difference between Black Box, White Box, and Grey Box testing?
- Black Box: Tester has no prior knowledge (simulates external attacker)
- White Box: Tester has complete knowledge (simulates insider threat)
- Grey Box: Tester has partial knowledge (realistic scenario)
Q154. What is Reconnaissance in penetration testing?
Reconnaissance is information gathering about the target before attacking. It includes discovering network infrastructure, employee information, technologies used, and potential vulnerabilities.
Q155. What is the difference between Active and Passive Reconnaissance?
- Active Reconnaissance: Directly interacting with target (port scanning, vulnerability scanning)—may be detected
- Passive Reconnaissance: Gathering information without direct contact (social media, public records, WHOIS)—harder to detect
Q156. What is OSINT?
OSINT (Open Source Intelligence) is gathering information from publicly available sources like social media, websites, forums, and public databases for security research or investigations.
Q157. What is Footprinting?
Footprinting is collecting information about target systems, networks, and organizations to understand their security posture before launching attacks.
Q158. What is Enumeration?
Enumeration is extracting detailed information about systems like usernames, network shares, services, and configurations through active probing after initial reconnaissance.
Q159. What is Port Scanning?
Port Scanning identifies open ports and services running on target systems. It helps attackers find potential entry points and defenders understand their exposure.
Q160. What is Nmap?
Nmap (Network Mapper) is a powerful open-source tool for network discovery and security auditing. It scans networks to discover hosts, ports, services, operating systems, and vulnerabilities.
Q161. What are common Nmap scan types?
- TCP Connect Scan (-sT): Complete TCP connection
- SYN Scan (-sS): Stealthy half-open scan
- UDP Scan (-sU): Scans UDP ports
- OS Detection (-O): Identifies operating system
- Service Version Detection (-sV): Determines service versions
Q162. What is Metasploit?
Metasploit is a comprehensive penetration testing framework containing exploits, payloads, and tools for testing system vulnerabilities. It’s the most widely used exploitation tool.
Q163. What is an Exploit?
Exploit is code or technique that takes advantage of a vulnerability to compromise a system. Exploits allow attackers to execute commands, install malware, or steal data.
Q164. What is a Payload in penetration testing?
Payload is the code that runs after an exploit successfully compromises a system. It performs the attacker’s desired action like opening a shell, stealing files, or installing backdoors.
Q165. What is a Reverse Shell?
Reverse Shell connects back from the compromised target to the attacker’s machine. Unlike normal shells, the victim initiates the connection, bypassing firewall restrictions.
Q166. What is a Bind Shell?
Bind Shell opens a listening port on the compromised target. The attacker connects to this port to gain shell access. Firewalls often block these.
Q167. What is Privilege Escalation?
Privilege Escalation exploits vulnerabilities to gain higher-level permissions. After initial access, attackers escalate from normal user to administrator/root for complete system control.
Q168. What is the difference between Vertical and Horizontal Privilege Escalation?
- Vertical: Moving to higher privilege level (user to admin)
- Horizontal: Accessing resources of another user at same privilege level
Q169. What is a Web Shell?
Web Shell is a script uploaded to web servers that provides remote command execution through a web interface. It gives attackers persistent access to compromised servers.
Q170. What is Kali Linux?
Kali Linux is a specialized Linux distribution pre-loaded with hundreds of penetration testing and security tools. It’s the industry standard for ethical hacking.
Q171. What is Burp Suite used for?
Burp Suite is an integrated platform for web application security testing. Its proxy intercepts and modifies HTTP requests, allowing testers to manipulate traffic and discover vulnerabilities.
Q172. What is Social Engineering in penetration testing?
Social Engineering tests human vulnerabilities by manipulating people into revealing confidential information or performing actions that compromise security.
Q173. What is Phishing simulation?
Phishing simulation sends fake phishing emails to employees to test awareness and identify who needs additional security training. It’s a controlled test of human defenses.
Q174. What is Brute Force attack?
Brute Force attack systematically tries all possible passwords or keys until finding the correct one. It’s time-consuming but guaranteed to work eventually if not prevented.
Q175. What is Password Cracking?
Password Cracking attempts to recover passwords from hashed or encrypted data using various techniques like dictionary attacks, brute force, or rainbow tables.
Q176. What is Hashcat?
Hashcat is a fast password recovery tool supporting numerous hashing algorithms. It uses CPU and GPU power to crack password hashes efficiently.
Q177. What is John the Ripper?
John the Ripper is a popular open-source password cracking tool. It detects hash types automatically and supports various cracking modes including dictionary, brute force, and hybrid attacks.
Q178. What is Hydra?
Hydra is a network logon cracker supporting numerous protocols (SSH, FTP, HTTP, etc.). It performs fast dictionary and brute-force attacks against authentication services.
Q179. What is a Backdoor?
Backdoor is a hidden method of bypassing normal authentication to access a system. Attackers install backdoors for persistent access even after original vulnerability is patched.
Q180. What is Lateral Movement?
Lateral Movement is moving through a network after initial compromise, accessing additional systems and escalating privileges across the infrastructure to reach high-value targets.
Section 7: Security Operations Center (SOC) (Questions 181-205)

Q181. What is a Security Operations Center (SOC)?
SOC is a centralized facility where security teams monitor, detect, analyze, and respond to cybersecurity incidents 24/7. It’s the organization’s security command center.
Q182. What are the different SOC Analyst levels?
- L1 (Tier 1): Alert monitoring, ticket creation, basic triage
- L2 (Tier 2): Deep investigation, incident analysis, containment
- L3 (Tier 3): Advanced threat hunting, malware analysis, complex incidents
Q183. What is SIEM?
SIEM (Security Information and Event Management) collects, analyzes, and correlates log data from multiple sources to detect security threats and generate alerts.
Q184. Name some popular SIEM tools.
- Splunk: Industry-leading commercial SIEM
- ELK Stack (Elasticsearch, Logstash, Kibana): Open-source alternative
- Wazuh: Free, open-source security monitoring
- IBM QRadar: Enterprise SIEM solution
- ArcSight: HP’s SIEM platform
Q185. What are Security Logs?
Security Logs record events occurring in systems, applications, and networks. SOC analysts review logs to identify suspicious activities, security incidents, and compliance violations.
Q186. What types of logs do SOC analysts monitor?
- Windows Event Logs: System, security, application events
- Linux Syslogs: System messages and authentication
- Firewall Logs: Network traffic allowed/blocked
- IDS/IPS Logs: Intrusion detection alerts
- Web Server Logs: HTTP requests and responses
- DNS Logs: Domain name resolution queries
Q187. What is an Indicator of Compromise (IOC)?
IOC is evidence that a system has been breached—like specific IP addresses, file hashes, or malicious URLs associated with attacks. SOC teams use IOCs to detect threats.
Q188. What is an Indicator of Attack (IOA)?
IOA focuses on attacker behaviors and tactics rather than specific artifacts. It detects attacks in progress by identifying suspicious actions and techniques.
Q189. What is Threat Hunting?
Threat Hunting is proactively searching for hidden threats that evaded automated detection systems. Instead of waiting for alerts, hunters actively look for signs of compromise.
Q190. What is Incident Response?
Incident Response is the systematic approach to managing security breaches, minimizing damage, reducing recovery time, and preventing future incidents.
Q191. What are the phases of Incident Response?
- Preparation: Establishing policies, tools, teams
- Detection/Identification: Recognizing security incidents
- Containment: Limiting damage and scope
- Eradication: Removing threats from systems
- Recovery: Restoring normal operations
- Lessons Learned: Analyzing and improving
Q192. What is Alert Triage?
Alert Triage is the process of reviewing, prioritizing, and categorizing security alerts to determine which require immediate investigation and which are false positives.
Q193. What is a False Positive?
False Positive is a security alert that incorrectly identifies normal activity as malicious. Too many false positives waste analyst time and can cause real alerts to be missed.
Q194. What is a False Negative?
False Negative occurs when security systems fail to detect actual malicious activity. This is more dangerous than false positives because threats go undetected.
Q195. What is Mean Time to Detect (MTTD)?
MTTD measures the average time between when a security incident occurs and when it’s detected. Shorter MTTD means faster threat discovery.
Q196. What is Mean Time to Respond (MTTR)?
MTTR measures the average time from incident detection to complete resolution. Faster MTTR limits attacker dwell time and reduces damage.
Q197. What is a Security Playbook?
Security Playbook is a documented procedure for responding to specific types of security incidents. It provides step-by-step instructions for consistent, effective responses.
Q198. What is Endpoint Detection and Response (EDR)?
EDR solutions monitor endpoint devices (computers, servers, mobile devices) continuously, detecting threats and enabling rapid response to security incidents.
Q199. What is the difference between EDR and XDR?
- EDR: Focuses only on endpoints (computers, servers)
- XDR (Extended Detection and Response): Correlates data from multiple sources (endpoints, network, cloud, email) for holistic visibility
Q200. What is Data Loss Prevention (DLP)?
DLP prevents sensitive data from leaving the organization unauthorized. It monitors, detects, and blocks confidential information transfers via email, USB, cloud, or other channels.
Q201. What is a Security Incident?
Security Incident is any event that threatens confidentiality, integrity, or availability of information systems—including malware infections, unauthorized access, data breaches, or DDoS attacks.
Q202. What is an Incident Severity Level?
Incidents are classified by impact and urgency:
- P1/Critical: Severe impact, immediate response required
- P2/High: Significant impact, urgent attention needed
- P3/Medium: Moderate impact, scheduled response
- P4/Low: Minimal impact, routine handling
Q203. What is a Security Information Sharing Community?
These are groups where organizations share threat intelligence, IOCs, and best practices to collectively improve security. Examples include ISACs (Information Sharing and Analysis Centers).
Q204. What is Threat Intelligence?
Threat Intelligence is analyzed information about current and emerging threats including attacker tactics, techniques, procedures (TTPs), and IOCs used to make informed security decisions.
Q205. What is the MITRE ATT&CK Framework?
MITRE ATT&CK is a knowledge base documenting adversary tactics and techniques based on real-world observations. SOC teams use it to understand attack patterns and improve detection.
Section 8: Active Directory & Windows Security (Questions 206-220)
Q206. What is Active Directory (AD)?
Active Directory is Microsoft’s directory service for Windows networks. It manages users, computers, and resources centrally, handling authentication and authorization across the network.
Q207. What is a Domain Controller?
Domain Controller is a server running Active Directory that authenticates users, enforces security policies, and stores directory information for the domain.
Q208. What is a Domain?
Domain is a logical group of network objects (users, computers, devices) that share the same Active Directory database and security policies.
Q209. What is LDAP?
LDAP (Lightweight Directory Access Protocol) is the protocol used to query and modify Active Directory. It’s how applications communicate with directory services.
Q210. What is Kerberos?
Kerberos is the default authentication protocol in Active Directory. It uses tickets to prove identity without sending passwords over the network.
Q211. What is a Golden Ticket attack?
Golden Ticket attack creates forged Kerberos tickets with domain admin privileges by compromising the KRBTGT account hash. Attackers gain unlimited domain access.
Q212. What is Pass-the-Hash attack?
Pass-the-Hash uses captured password hashes to authenticate without knowing the actual password. Attackers replay hashes to access systems as legitimate users.
Q213. What is Mimikatz?
Mimikatz is a powerful post-exploitation tool that extracts passwords, hashes, and Kerberos tickets from Windows memory. It’s widely used by both pentesters and attackers.
Q214. What is Group Policy?
Group Policy centrally manages Windows configurations and security settings across the domain. Administrators apply policies to users and computers for consistent security.
Q215. What is LLMNR Poisoning?
LLMNR Poisoning exploits Link-Local Multicast Name Resolution to capture credentials. Attackers respond to LLMNR queries, tricking victims into authenticating and revealing password hashes.
Q216. What is SMB Relay attack?
SMB Relay intercepts and relays SMB authentication attempts to other servers. Attackers don’t crack passwords but use captured authentication to access resources.
Q217. What is BloodHound?
BloodHound is a tool that maps Active Directory relationships and attack paths. It visualizes how attackers could move laterally through the network to reach domain admins.
Q218. What is the difference between Local and Domain accounts?
- Local Account: Exists only on one computer, can’t access network resources
- Domain Account: Stored in Active Directory, can access resources across the domain
Q219. What is NTLM?
NTLM (NT LAN Manager) is Microsoft’s older authentication protocol, now considered less secure than Kerberos but still widely supported for backward compatibility.
Q220. What is PowerShell used for in security?
PowerShell is Windows’ powerful scripting language. Attackers use it for fileless malware and lateral movement; defenders use it for automation and threat hunting.
Module 2: 50 Self-Preparation Prompts Using ChatGPT
How to Use These Prompts
Copy and paste these prompts directly into ChatGPT or any AI assistant to practice, learn, and prepare for your cyber security interviews. These prompts are designed to help you understand concepts deeply, practice explanations, and build confidence.
Pro Tips:
- Use these prompts daily during your preparation
- Save the AI responses for quick revision
- Ask follow-up questions to dive deeper
- Practice explaining answers in your own words
- Use voice input to practice verbal communication
Section 1: Fundamental Concepts & Theory (Prompts 1-10)
Prompt 1:
“Explain the CIA Triad in cyber security to me like I’m a 10-year-old. Then give me 3 real-world examples of how each principle (Confidentiality, Integrity, Availability) can be violated in everyday technology.”
Prompt 2:
“I’m preparing for a cyber security interview. Act as an interviewer and ask me 5 random questions about different types of malware. After I answer each question, tell me if my answer is correct and explain what I should improve.”
Prompt 3:
“Create a simple comparison table showing the differences between Virus, Worm, Trojan, Ransomware, and Spyware. Include columns for: Definition, How it Spreads, Main Purpose, and Real-World Example.”
Prompt 4:
“Explain the concept of Defense in Depth strategy in cyber security. Give me an analogy using a physical bank’s security measures, then map each physical security layer to a cyber security equivalent.”
Prompt 5:
“I need to understand encryption better. Explain Symmetric vs Asymmetric encryption using a simple story or analogy. Then explain when to use each type in real-world applications.”
Prompt 6:
“Quiz me on networking fundamentals. Ask me 10 questions covering OSI Model, TCP/IP, ports, protocols, and IP addressing. Grade my answers and provide detailed explanations for anything I get wrong.”
Prompt 7:
“Explain the complete journey of an email from the moment I click ‘Send’ until it reaches the recipient’s inbox. Include all security protocols, servers, and potential security vulnerabilities at each step.”
Prompt 8:
“Create a beginner-friendly guide explaining what happens during a SQL Injection attack. Use simple language, include a step-by-step breakdown, and show both the attacker’s perspective and how to prevent it.”
Prompt 9:
“I’m confused about firewalls, IDS, and IPS. Explain the difference between these three using a real-world security guard analogy. Then tell me when an organization would need each one.”
Prompt 10:
“Test my understanding of authentication vs authorization. Give me 10 different scenarios and ask me to identify whether each involves authentication, authorization, or both. Then explain the correct answers.”
Section 2: Linux & Command Line Mastery (Prompts 11-15)
Prompt 11:
“I’m new to Linux for cyber security. Create a beginner’s roadmap of the top 30 Linux commands every cyber security professional must know. For each command, give me the purpose, basic syntax, and a practical security use case.”
Prompt 12:
“Explain Linux file permissions to me step by step. Then give me 10 practice scenarios where I need to set specific permissions using chmod, and tell me the exact commands I should use.”
Prompt 13:
“Act as a Linux system administrator interviewer. Ask me practical scenario-based questions about troubleshooting, security hardening, and user management. Evaluate my thinking process and suggest better approaches.”
Prompt 14:
“I need to understand log analysis. Explain what each of these log files contains and why they’re important for security: /var/log/auth.log, /var/log/syslog, /var/log/kern.log, /var/log/apache2/access.log. Then give me example entries and how to analyze them.”
Prompt 15:
“Create a practice challenge for me. Give me 5 Linux command-line scenarios that a SOC analyst might face daily, and let me explain how I would solve each one. Then provide the optimal solutions.”
Section 3: Networking Deep Dive (Prompts 16-20)
Prompt 16:
“Explain the complete TCP Three-Way Handshake process like I’m explaining it to a hiring manager with limited technical knowledge. Use simple terms but be technically accurate. Then explain what can go wrong and how attackers exploit this.”
Prompt 17:
“Create a detailed comparison between HTTP and HTTPS. Include how SSL/TLS works, the encryption process, certificate validation, and why HTTPS is essential. Use diagrams described in words if necessary.”
Prompt 18:
“I need to master subnetting for interviews. Teach me subnet calculation step by step with multiple examples. Start from basics and gradually increase complexity. Include practice problems with solutions.”
Prompt 19:
“Explain how DNS works from start to finish. Include all types of DNS records (A, AAAA, MX, CNAME, TXT), the resolution process, caching, and common DNS-based attacks like DNS spoofing and DNS tunneling.”
Prompt 20:
“Quiz me on networking protocols. Give me 15 port numbers randomly, and I’ll tell you which protocol uses that port and what it does. Then correct me and explain any I get wrong, including why those specific port numbers were assigned.”
Section 4: Web Application Security (Prompts 21-25)
Prompt 21:
“Explain the OWASP Top 10 vulnerabilities for 2024. For each vulnerability, provide: a simple explanation, a real-world analogy, how attackers exploit it, the potential impact, and prevention methods.”
Prompt 22:
“I want to deeply understand SQL Injection. Give me 10 different SQL Injection payload examples with increasing complexity. For each, explain what the payload does, why it works, and show me the vulnerable code vs secure code.”
Prompt 23:
“Create an interview roleplay. You ask me questions about XSS (Cross-Site Scripting) attacks – types, exploitation, impact, and prevention. After each of my answers, provide feedback and share what experienced professionals would say.”
Prompt 24:
“Explain CSRF attacks using a step-by-step story involving a banking website. Make it detailed enough that I can explain this attack to a non-technical person. Then show me 3 different ways to prevent CSRF.”
Prompt 25:
“I’m preparing to answer questions about authentication vulnerabilities. Teach me about: Broken Authentication, Session Hijacking, Session Fixation, Weak Password Policies, and Missing MFA. Include real-world examples and how to test for these.”
Section 5: Cryptography Concepts (Prompts 26-30)
Prompt 26:
“I struggle with cryptography concepts. Explain hashing, encryption, and encoding using simple real-world analogies. Then explain why we use hashing for passwords instead of encryption, and what salting means.”
Prompt 27:
“Create a detailed guide about digital certificates and SSL/TLS. Explain: What certificates are, how they work, the role of Certificate Authorities, the SSL handshake process, and how to identify certificate issues.”
Prompt 28:
“Quiz me on cryptographic algorithms. Ask me to explain the differences between MD5, SHA-1, SHA-256, AES, DES, 3DES, RSA, and ECC. Tell me which are deprecated, which to use today, and why.”
Prompt 29:
“Explain Public Key Infrastructure (PKI) from the ground up. Include all components, how they work together, trust chains, certificate validation, and real-world applications in enterprises and websites.”
Prompt 30:
“I need to understand digital signatures completely. Explain: What they are, how they work cryptographically, the difference between signing and encrypting, use cases, and how to verify signatures.”
🔐 Understand Encryption, Hashing & Real-World Security Tools
🎓 Enroll in the → Cybersecurity Masterclass
Section 6: Penetration Testing & Ethical Hacking (Prompts 31-38)
Prompt 31:
“Create a complete penetration testing methodology guide for me. Cover each phase: Reconnaissance, Scanning, Enumeration, Exploitation, Post-Exploitation, and Reporting. For each phase, list tools, techniques, and what information to gather.”
Prompt 32:
“I need to master Nmap for interviews. Teach me: different scan types, when to use each, how to interpret results, common flags and options, and give me 10 practical scanning scenarios with the exact commands I should use.”
Prompt 33:
“Explain Metasploit framework completely. Cover: architecture, modules (exploits, payloads, encoders, auxiliaries), how to search for exploits, how to use exploits, setting options, and post-exploitation. Include example workflows.”
Prompt 34:
“Act as a penetration testing interviewer. Ask me scenario-based questions like: ‘You’ve gained initial access to a Windows machine with standard user privileges. Walk me through your privilege escalation process.’ Evaluate my methodology.”
Prompt 35:
“Teach me about different types of shells in penetration testing: Bind shell, Reverse shell, Web shell. Explain how each works, when to use them, how to establish them, and their advantages/disadvantages.”
Prompt 36:
“I want to understand password cracking deeply. Explain: brute-force attacks, dictionary attacks, rainbow tables, hybrid attacks. Then teach me about tools like John the Ripper, Hashcat, and Hydra with practical examples.”
Prompt 37:
“Create a comprehensive guide about privilege escalation on both Linux and Windows. Include: common misconfigurations, vulnerable services, kernel exploits, and how to identify escalation paths. Provide step-by-step methodologies.”
Prompt 38:
“Explain OSINT (Open Source Intelligence) gathering for penetration testing. List all sources, tools, and techniques. Then give me a practice scenario where I need to gather information about a fictional company for a pentest.”
⚡ Access Pentesting Roadmaps, Tools & Cheat Sheets
Section 7: SOC Operations & Incident Response (Prompts 39-44)
Prompt 39:
“I’m interviewing for a SOC Analyst position. Prepare me by asking typical SOC interview questions covering: alert triage, log analysis, incident response, SIEM tools, and threat hunting. Provide model answers after I respond.”
Prompt 40:
“Explain how a Security Operations Center works. Cover: SOC analyst levels (L1, L2, L3), daily responsibilities, tools used (SIEM, EDR, SOAR), typical workflows, and how incidents are escalated.”
Prompt 41:
“Teach me log analysis for security. Show me examples of malicious activity in different types of logs (Windows Event Logs, Linux auth logs, firewall logs, web server logs). Help me understand what patterns indicate attacks.”
Prompt 42:
“Create a complete Incident Response guide following the NIST framework. For each phase (Preparation, Detection, Containment, Eradication, Recovery, Lessons Learned), explain actions, tools, documentation needed, and best practices.”
Prompt 43:
“I need to understand SIEM deeply. Explain: what SIEM does, how it works, correlation rules, use cases, common queries, alert creation, and dashboards. Then show me example scenarios of how SIEM detects different attacks.”
Prompt 44:
“Quiz me on Indicators of Compromise (IOCs). Give me 20 different scenarios or log entries, and ask me to identify if they’re suspicious. Then explain what each indicates and how a SOC analyst should respond.”
🛡️ Learn Real-World SOC Scenarios & Best Practices 🧠 Read SOC Analyst Guides →
Section 8: Advanced Topics & Current Trends (Prompts 45-50)
Prompt 45:
“Explain Active Directory security completely. Cover: AD structure, common attacks (Pass-the-Hash, Golden Ticket, Kerberoasting, LLMNR Poisoning), enumeration techniques, and defense strategies. Make it interview-ready.”
Prompt 46:
“I need to understand cloud security basics for interviews. Explain AWS/Azure security fundamentals, shared responsibility model, common misconfigurations, IAM, security groups, and cloud-specific vulnerabilities.”
Prompt 47:
“Teach me about the MITRE ATT&CK framework. Explain what it is, how it’s organized (Tactics, Techniques, Procedures), how security professionals use it, and give me examples of mapping real attacks to the framework.”
Prompt 48:
“Create a current cyber threat landscape overview for 2025. Cover: emerging threats, trending attack techniques, major vulnerabilities, ransomware trends, and what security professionals are focusing on. Make it interview-ready.”
Prompt 49:
“Explain Zero Trust Architecture concept thoroughly. Include: principles, how it differs from traditional security, implementation components, benefits, challenges, and real-world examples. Prepare me to discuss this in interviews.”
Prompt 50:
“I want to practice behavioral and scenario questions. Act as an interviewer and ask me complex scenario questions like: ‘Describe a time you detected a security breach’ or ‘How would you handle a ransomware incident?’ Guide me on structuring STAR-method responses.”
Bonus: Advanced Practice Prompts
Bonus Prompt 1:
“Create a mock technical interview for a Cyber Security Analyst position. Ask me 15 questions covering all topics (fundamentals, networking, web security, tools). Rate my answers from 1-10 and provide detailed feedback.”
Bonus Prompt 2:
“I want to practice explaining complex concepts simply. Give me a random advanced cyber security topic, and I’ll explain it like I’m teaching a beginner. Then critique my explanation and show me how experts would explain it.”
Bonus Prompt 3:
“Generate a personalized study plan for me based on a 4-week timeline before my cyber security interview. Include daily topics to cover, hands-on practice recommendations, and mock interview schedules.”
Bonus Prompt 4:
“Create a comprehensive cheat sheet of the most common interview questions for: Entry-level Cyber Security Analyst, SOC Analyst, Penetration Tester, and Security Engineer roles. Include both technical and behavioral questions.”
Bonus Prompt 5:
“Help me build a home lab for cyber security practice. Suggest free tools, virtual machine setups, vulnerable applications to practice on, and step-by-step projects that will prepare me for real-world scenarios and interviews.”
How to Maximize Learning with These Prompts
Daily Practice Routine
Week 1: Foundations
- Days 1-2: Use Prompts 1-10 (Fundamentals)
- Days 3-4: Use Prompts 11-15 (Linux)
- Days 5-7: Use Prompts 16-20 (Networking)
Week 2: Application Security
- Days 1-3: Use Prompts 21-25 (Web Security)
- Days 4-5: Use Prompts 26-30 (Cryptography)
- Days 6-7: Review Week 1 & 2 using AI quizzes
Week 3: Advanced Skills
- Days 1-4: Use Prompts 31-38 (Pentesting)
- Days 5-7: Use Prompts 39-44 (SOC Operations)
Week 4: Final Preparation
- Days 1-3: Use Prompts 45-50 (Advanced Topics)
- Days 4-5: Use all Bonus Prompts
- Days 6-7: Mock interviews and revision
Advanced Learning Techniques
- Progressive Learning:
Start with basic prompts, then ask ChatGPT: “Now explain this at an advanced level with technical depth.” - Scenario Building:
After learning a concept, ask: “Give me 5 real-world interview scenarios where I would need to apply this knowledge.” - Reverse Teaching:
After ChatGPT explains something, say: “Now ask ME to explain this back to you, and correct any mistakes.” - Connection Mapping:
Ask: “How does [Concept A] relate to [Concept B]? Give me scenarios where understanding both is crucial.” - Weakness Identification:
Say: “Based on my answers, identify gaps in my knowledge and create a focused learning plan.”
Interview Simulation Exercises
Technical Round Practice:
“Conduct a 45-minute technical interview for a [Job Role]. Ask progressively harder questions. At the end, rate my performance and identify improvement areas.”
HR Round Practice:
“Act as an HR interviewer for a cyber security position. Ask me about my background, motivation, salary expectations, and behavioral questions. Give feedback on my responses.”
Practical Assessment:
“Give me a practical cyber security incident scenario. I’ll walk you through my investigation and response process step by step. Critique my methodology.”
Tips for Using AI Tools Effectively
- Be Specific: Instead of “Explain firewalls,” ask “Explain firewalls to a cyber security beginner preparing for an interview, with examples and common interview questions.”
- Request Formats: Ask for information in tables, bullet points, step-by-step guides, or comparison formats based on what helps you learn best.
- Follow-Up Questions: Always ask “Can you explain that differently?” or “Give me a real-world example” if something isn’t clear.
- Save Everything: Keep a document of all AI responses. Review them the night before your interview for quick revision.
- Combine Learning: After using a prompt, immediately search for videos or articles on the same topic to reinforce learning.
- Practice Verbally: Use voice input to practice explaining concepts aloud. This prepares you for actual interview communication.
- Create Flashcards: Turn AI explanations into flashcards for quick revision of definitions, concepts, and tools.
🤖 Get AI Practice Prompts for Java, Python & More!
Module 3: Communication Skills and Behavioral Interview Preparation

Section 1: Mastering Communication Skills
Why Communication is Critical in Cyber Security
Reality Check:
- You discover a critical vulnerability. Can you explain the risk to your CEO in 2 minutes?
- During a ransomware attack, can you calmly coordinate between IT, legal, and management teams?
- Can you write a clear incident report that both technical and non-technical people understand?
If you answered “maybe” or “no” to any of these, you need communication training.
Types of Communication You’ll Need
- Technical to Non-Technical Translation : This is your most important skill. You must explain complex technical concepts to people who don’t understand technology.
Bad Example:
“The SQL injection vulnerability in the parameterized query function allows remote code execution through unsanitized user inputs exploiting the backend MySQL database.”
Good Example:
“We found a security hole in our website’s login form. Hackers can type special commands that trick our database into giving them access to customer information. We need to fix this within 24 hours to prevent data theft.”
Practice Exercise:
Take any 10 technical concepts from Part 1 and explain each in one simple sentence your grandmother would understand.
- Incident Communication : During security incidents, you’ll communicate with multiple stakeholders:
To Management:
- Focus on business impact (money, reputation, customers)
- Provide clear action items and timelines
- Avoid technical jargon
- Be calm and confident
To Technical Teams:
- Share detailed technical findings
- Provide specific IOCs and artifacts
- Discuss containment strategies
- Coordinate response actions
To End Users:
- Explain what happened in simple terms
- Tell them what actions they need to take
- Reassure them about protective measures
- Answer questions patiently
- Written Communication : You’ll write constantly in cyber security roles:
- Incident reports
- Vulnerability assessments
- Security policies
- Email updates
- Documentation
Writing Guidelines:
Be Clear: Use short sentences. One idea per sentence.
Be Concise: Remove unnecessary words. Say “now” instead of “at this point in time.”
Use Structure: Start with summary, then details. Use bullet points and headings.
Be Specific: Instead of “major vulnerability,” say “critical SQL injection allowing database access.”
Proofread: Grammar and spelling mistakes make you look careless.
- Presentation Skills : You’ll present security findings, training sessions, and project updates.
Presentation Structure:
- Opening: Hook their attention with a relevant statistic or story
- Problem: What security issue exists?
- Impact: Why should they care?
- Solution: What you recommend
- Action Items: What happens next
- Q&A: Handle questions confidently
Presentation Tips:
- Make eye contact with different people
- Speak clearly and at moderate pace
- Use visuals (charts, diagrams) to explain complex ideas
- Practice multiple times before the actual presentation
- Prepare for questions you might receive
- Don’t read from slides—talk naturally
- Active Listening : Cyber security professionals must listen carefully to:
- Understand user-reported security issues
- Gather incident details accurately
- Comprehend stakeholder concerns
- Follow complex technical discussions
How to Listen Actively:
- Give full attention—don’t check your phone
- Take notes during important discussions
- Ask clarifying questions
- Summarize what you heard to confirm understanding
- Don’t interrupt—let people finish speaking
🎯 Reading’s Great — Learning by Doing Is Better ! 🎓 Start Practical Training Now →
Section 2: The STAR Method for Behavioral Questions
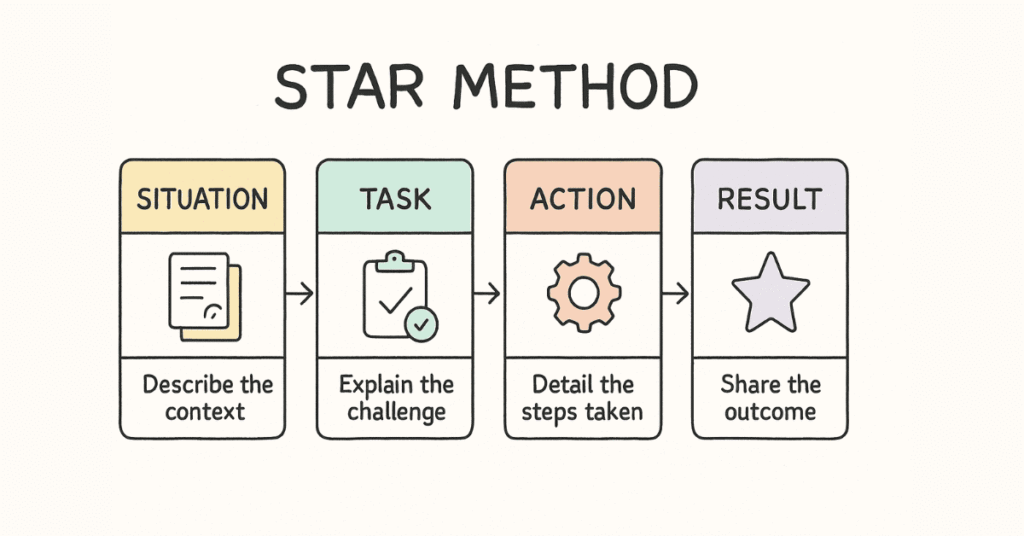
What is the STAR Method?
STAR is a framework for answering behavioral interview questions with clear, structured stories from your experience.
S – Situation: Set the context and background
T – Task: Explain your responsibility or challenge
A – Action: Describe specific steps you took
R – Result: Share the outcome and what you learned
Why Interviewers Ask Behavioral Questions
Companies want to know:
- How you handle pressure and stress
- How you solve problems
- How you work with teams
- How you deal with failures
- Whether you take initiative
- If you can learn from mistakes
Past behavior predicts future performance. Your stories show how you’ll act in their organization.
How to Structure Perfect STAR Answers
Step 1: Choose the Right Story
Pick experiences that show:
- Problem-solving abilities
- Technical skills applied practically
- Leadership or teamwork
- Overcoming challenges
- Learning and growth
Your stories can come from:
- Academic projects
- Internships
- Part-time jobs
- Personal projects or home labs
- Volunteer work
- Online competitions or CTFs
Step 2: Prepare Your Story Bank
Before interviews, write down 8-10 different stories covering:
- A challenging technical problem you solved
- A time you worked in a team
- When you handled conflict
- A security incident you managed
- A mistake you made and learned from
- When you took initiative
- A time you explained something technical to non-technical people
- When you worked under pressure
Step 3: Practice Your Delivery
For each story:
- Write it down following STAR format
- Practice saying it aloud (not just reading)
- Keep answers between 1.5 to 2.5 minutes
- Record yourself and improve
- Get feedback from friends or mentors
STAR Method Example
Question: “Tell me about a time you identified and resolved a security issue.”
Weak Answer:
“During my internship, I found a security problem in the company’s website. I told my manager and we fixed it. Everyone was happy.”
Strong STAR Answer:
Situation: “During my 3-month internship at XYZ Company, I was assigned to review their customer portal’s security as part of a routine assessment.”
Task: “My responsibility was to perform basic security testing and report any findings to the security team. While testing the password reset function, I noticed the application wasn’t validating password strength properly.”
Action: “I documented the vulnerability with screenshots and tested its potential impact. I found that users could set weak passwords like ‘123456,’ making accounts vulnerable to brute force attacks. I prepared a detailed report explaining the risk in simple terms, including potential business impact—unauthorized account access could expose customer data and damage the company’s reputation. I presented my findings to both the security team and development team, recommending implementing password complexity requirements and adding rate limiting on login attempts.”
Result: “The development team implemented my recommendations within one week. They added password strength validation requiring minimum 8 characters with mixed case, numbers, and symbols. They also added account lockout after 5 failed attempts. My manager praised my thoroughness and clear communication. This experience taught me the importance of not just finding vulnerabilities, but also effectively communicating risks to drive action. The company later made me responsible for monthly security reviews.”
Why This Answer Works:
- Specific details (company, timeframe, exact vulnerability)
- Shows technical knowledge (password validation, brute force)
- Demonstrates communication skills (explained to multiple audiences)
- Quantified outcome (one week implementation, specific security measures)
- Shows learning and growth (lesson learned, increased responsibility)
Section 3: Common Behavioral Questions with Model Answers
Category 1: Problem-Solving and Technical Challenges
Q1: Describe a complex security problem you solved. How did you approach it?
Model Answer Structure:
- Start with the challenging situation
- Explain your systematic approach
- Show your technical thinking process
- Highlight the successful resolution
- Mention what you learned
Example Answer:
“During my final year project, I was building a secure file-sharing application. After deployment on our test server, users complained about slow performance.
I approached this systematically. First, I used Wireshark to capture network traffic and noticed excessive database queries. Using query profiling tools, I discovered our encryption implementation was decrypting files on every access check, even just to verify permissions.
I restructured the code to separate permission validation from file decryption. I implemented caching for access control lists and only decrypted files when users actually downloaded them. I also added lazy loading for file metadata.
The result was a 75% reduction in response time and significantly lower server CPU usage. This taught me that security implementations must balance protection with performance. I also learned to always profile applications before optimizing, rather than guessing where problems exist.”
Q2: Tell me about a time when you encountered a technology or security concept you didn’t understand. How did you learn it?
Model Answer Structure:
- Admit the knowledge gap honestly
- Show your learning process
- Demonstrate resourcefulness
- Prove you mastered the concept
- Show ongoing learning commitment
Example Answer:
“When I started my cyber security course, I struggled with understanding how Public Key Infrastructure actually works. The concept of using two different keys seemed confusing.
I took a multi-approach learning strategy. First, I watched YouTube videos explaining PKI with real-world analogies. Then I read the official documentation and technical articles. What really helped was building a practical project—I set up my own Certificate Authority in my home lab and generated certificates for a test website.
I documented the entire process in a blog post, which forced me to understand each step deeply enough to explain it to others. Several people commented with questions, which pushed me to research even deeper.
Within two weeks, I went from confused to confident. I could explain PKI to both technical and non-technical audiences. This experience reinforced my learning philosophy—combine theory with hands-on practice and teach others to truly master concepts. Now whenever I encounter unfamiliar concepts, I follow this same approach.”
Q3: Describe a situation where you had to work with incomplete information to solve a security issue.
Model Answer Structure:
- Explain the uncertain situation
- Show your decision-making under uncertainty
- Describe how you gathered additional information
- Explain your risk assessment
- Share the outcome
Example Answer:
“During my internship’s final month, our monitoring system detected unusual outbound traffic at 3 AM. The senior analyst was unavailable, and I was the only one monitoring alerts.
With limited information, I followed our incident response playbook. I isolated the affected server from the network to prevent potential data exfiltration, documented everything I observed, and gathered log files for analysis. I noticed the traffic was going to an unfamiliar IP address in another country.
I used threat intelligence platforms to check if the IP was known for malicious activity—it was flagged as a command and control server. I immediately escalated to the security manager via phone and email, providing all details I’d gathered.
Investigation revealed a developer had accidentally installed compromised software from an unofficial source. My quick containment prevented potential data breach. The security manager commended my decision to isolate first and investigate after, following the principle of ‘assume breach until proven otherwise.’
This taught me that in security, it’s better to act conservatively with incomplete information than wait for perfect information while damage occurs. I also learned to trust established procedures and escalate appropriately.”
Category 2: Teamwork and Collaboration
Q4: Give an example of when you had to work with a difficult team member. How did you handle it?
Model Answer Structure:
- Describe the situation professionally (don’t badmouth people)
- Explain the difficulty objectively
- Show your mature approach
- Highlight positive outcome
- Emphasize lessons learned
Example Answer:
“During a group project for our web application security course, one team member consistently missed deadlines and submitted incomplete work, causing delays for everyone.
Rather than complaining to the professor, I requested a private conversation with this person. I asked if they were facing challenges I wasn’t aware of. They shared they were struggling to balance this project with family responsibilities and felt overwhelmed by the technical requirements.
I offered to pair-program with them during their available hours, breaking down complex tasks into smaller, manageable pieces. We created a more realistic timeline together. I also connected them with online resources that explained concepts at their level.
Their contributions improved significantly. We completed the project successfully and received an A grade. They later thanked me for the support rather than reporting them.
This experience taught me that perceived laziness or incompetence often masks underlying struggles. Direct, empathetic communication solves most team conflicts. As a security professional, I’ll work with diverse teams, so understanding people’s perspectives is as important as technical skills.”
Q5: Describe a time when you had to explain a technical security concept to someone without a technical background.
Model Answer Structure:
- Set the context
- Explain who your audience was
- Describe your communication strategy
- Show the successful outcome
- Highlight what you learned about communication
Example Answer:
“During an internship, my manager asked me to present our security assessment findings to the company’s marketing director, who needed to understand website security for an upcoming campaign but had no technical background.
I knew technical jargon would confuse rather than clarify. I structured my presentation around business impact rather than technical details. For example, instead of explaining ‘SSL/TLS encryption protocols,’ I said ‘This is like sending letters in locked boxes instead of postcards—only the recipient can read them.’
For the SQL injection vulnerability we found, I explained: ‘Imagine your website’s contact form is like a suggestion box. Right now, someone could drop in a note that says ‘give me everyone’s information’ and the system would obey. We need to teach the system to recognize and reject these malicious notes.’
The director completely understood the risks and approved the budget for fixes immediately. They later told my manager that my presentation was the clearest technical explanation they’d ever received.
This reinforced that effective security professionals must speak multiple languages—technical with engineers, business-focused with executives, and simplified with general users. Understanding your audience determines communication success.”
Q6: Tell me about a time you collaborated with other teams or departments to achieve a security objective.
Model Answer Structure:
- Describe the cross-functional project
- Explain coordination challenges
- Show your collaboration approach
- Highlight the successful outcome
- Emphasize teamwork lessons
Example Answer:
“During my final semester, I participated in a college-wide cybersecurity awareness campaign that required collaboration between the IT department, student council, and administration.
The challenge was coordinating three groups with different priorities and schedules. The IT team focused on technical solutions, student council wanted engaging content, and administration needed policy compliance.
I volunteered to be the liaison. I created a shared project timeline with clear responsibilities for each team. I scheduled weekly video calls at times that worked for everyone. I translated technical requirements into simple language for non-technical teams and explained administrative concerns to technical people.
We successfully launched a month-long campaign including phishing simulations, interactive workshops, and security tip posters. Student participation increased 40% compared to previous years. The administration was impressed with student engagement, and the IT department appreciated reduced security incidents after the campaign.
This experience showed me that cyber security isn’t just a technical function—it requires building relationships across the organization. Understanding different perspectives and facilitating communication between teams is crucial for implementing effective security programs.”
Category 3: Pressure and Stress Management
Q7: Describe a situation where you had to work under significant time pressure. How did you handle it?
Model Answer Structure:
- Set up the high-pressure situation
- Explain your prioritization approach
- Show you stayed calm and focused
- Describe the successful outcome
- Share stress management lessons
Example Answer:
“During my internship, our team discovered a critical vulnerability in a production application on Friday afternoon, just before a major weekend sales event expected to bring thousands of users.
The pressure was intense—fix it immediately or potentially expose customer data during high-traffic period. I was assigned to assist the senior engineer with testing the patch before deployment.
I stayed calm and focused on the process. I created a testing checklist covering all critical functions. While the developer worked on the fix, I prepared a test environment mirroring production. Once the patch was ready, I systematically tested each scenario, documenting results clearly.
We found and fixed two issues during testing that would have caused problems. The patch was successfully deployed within 4 hours, before the weekend traffic surge. No security incidents occurred during the sales event.
This experience taught me that staying methodical under pressure produces better results than rushing. Having clear processes and checklists prevents mistakes when stressed. I also learned that high-pressure situations are normal in cyber security, so developing calmness and systematic thinking is essential for this career.”
Q8: Tell me about a time when you had to handle multiple security tasks simultaneously. How did you prioritize?
Model Answer Structure:
- Describe the overwhelming situation
- Explain your prioritization framework
- Show your time management
- Highlight successful completion
- Share organizational lessons
Example Answer:
“During my final month internship, I was simultaneously assigned to complete a security audit, investigate suspicious login attempts, and prepare a presentation on security best practices—all with overlapping deadlines.
I used a priority matrix based on urgency and impact. The suspicious logins were investigated first since they represented active potential threats. I set up automated monitoring for the affected accounts and documented my findings within 2 hours.
For the ongoing tasks, I broke down the security audit into daily milestones and allocated specific time blocks each morning when I was most focused. The presentation was prepared during afternoon sessions, building it incrementally over several days rather than last-minute.
I also communicated my priorities to my supervisor and asked for guidance when conflicts arose. I used project management tools to track all tasks and deadlines.
All three tasks were completed successfully and on time. The suspicious activity investigation revealed a brute force attempt that we blocked. The audit uncovered 12 security improvements that were implemented. My presentation was well-received by 50+ employees.
This experience taught me that cyber security professionals constantly juggle multiple priorities. Success requires clear prioritization frameworks, disciplined time management, effective communication with stakeholders, and knowing when to ask for help or deadline adjustments.”
Category 4: Mistakes and Learning
Q9: Tell me about a time you made a mistake in your work. How did you handle it?
Model Answer Structure:
- Honestly describe the mistake
- Explain how you discovered it
- Show you took responsibility
- Describe your correction actions
- Highlight what you learned
Important: Never say “I’ve never made a mistake.” Everyone makes mistakes. What matters is owning them and learning.
Example Answer:
“During a security lab exercise, I was practicing penetration testing on our instructor’s authorized test environment. I misidentified which IP address belonged to the test system and accidentally started scanning a production university server.
I realized my mistake within minutes when I noticed the scan results didn’t match the expected test environment. I immediately stopped all scans and reported the incident to my instructor.
I took full responsibility for not double-checking the IP address before starting. I documented exactly what commands I ran and when. My instructor appreciated my honesty and quick reporting. We reviewed the incident together, and I learned to implement a pre-engagement checklist that includes verification of target systems.
As a result, I created a personal checklist I now use before any security testing: verify target IP, confirm authorization documents, check scope boundaries, and have emergency contact information ready.
This mistake taught me crucial lessons that make me a better security professional. First, careful verification prevents errors. Second, immediate transparency when mistakes happen minimizes damage. Third, every mistake is a learning opportunity. In cyber security, where errors can have serious consequences, I’m actually glad I learned this lesson in a controlled environment where real harm couldn’t occur.”
Q10: Describe a situation where you received critical feedback. How did you respond?
Model Answer Structure:
- Describe the feedback situation
- Show your initial reaction
- Explain how you processed the feedback
- Describe improvements you made
- Show growth from the experience
Example Answer:
“After presenting my first security assessment report to my internship supervisor, they provided direct feedback that my report was too technical and lacked business context. They said management wouldn’t understand the importance of my findings.
Initially, I felt defensive—I’d worked hard on technical analysis. But after reflecting, I realized they were right. I was writing for an audience like myself rather than the actual readers.
I asked my supervisor for examples of well-written reports and studied their structure. I learned to start reports with executive summaries in plain language, organize findings by business risk rather than technical severity, and include specific remediation recommendations with cost and time estimates.
I rewrote the report using this approach. My supervisor approved it, and the management team actually acted on the findings quickly because they understood the business impact clearly.
This feedback transformed how I communicate. I now always consider my audience before writing or presenting. I also learned that good feedback, even when uncomfortable, is a gift that makes you better. I actively seek feedback now rather than waiting for it. In cyber security, where communicating risk to decision-makers is critical, this lesson was invaluable.”
Category 5: Initiative and Leadership
Q11: Give an example of when you went beyond your assigned responsibilities.
Model Answer Structure:
- Describe your standard responsibilities
- Explain what additional need you identified
- Show the initiative you took
- Describe the positive impact
- Highlight the lesson learned
Example Answer:
“During my internship as a security analyst assistant, my primary role was monitoring alerts and escalating issues. However, I noticed our team was repeatedly getting similar phishing alert types that were actually false positives from a specific email marketing service.
Without being asked, I spent time after hours analyzing these false positives. I identified patterns in email headers and sender characteristics that distinguished legitimate marketing from actual phishing attempts. I documented my findings and created a detailed proposal for updated alert rules.
I presented this to my supervisor, including before/after metrics showing we could reduce false positive alerts by approximately 30% while maintaining security. They were impressed with my initiative and worked with me to implement the new rules.
The result was our team saved roughly 5 hours weekly previously spent investigating these false positives. My supervisor mentioned this initiative in my performance review and used it as an example during team meetings.
This experience taught me that security professionals should always look for process improvements, not just complete assigned tasks. Taking initiative shows you think like an owner, not just an employee. Organizations value people who identify and solve problems independently.”
Q12: Describe a situation where you had to convince others to adopt a security measure they resisted.
Model Answer Structure:
- Describe the security measure needed
- Explain the resistance you faced
- Show your persuasion strategy
- Describe the successful outcome
- Share what you learned about influence
Example Answer:
“During a college club project, I suggested implementing two-factor authentication for our administrative accounts after learning about credential stuffing attacks. Several members resisted, saying it would be inconvenient and unnecessary since we were ‘just a student club.’
I understood their concern about added friction. Instead of just citing security risks, I researched whether similar clubs had been compromised. I found several documented cases where student organization accounts were hacked, leading to spam campaigns and reputational damage.
I prepared a brief presentation showing these real examples, demonstrating how quick and easy modern 2FA actually is, and offering to help everyone set it up. I framed it as protecting the club’s reputation and everyone’s work, not just abstract security.
The presentation changed minds. We implemented 2FA within a week, and I helped each admin set it up personally. Six months later, we detected a login attempt using old compromised credentials—2FA blocked it automatically.
This taught me that effective security advocacy requires understanding people’s concerns, using relatable examples rather than abstract threats, minimizing friction in your solutions, and offering support for implementation. In cyber security roles, getting buy-in from reluctant stakeholders is often harder than the technical work itself.”
Category 6: Adaptability and Learning
Q13: Tell me about a time you had to adapt to a significant change in your work or project.
Model Answer Structure:
- Describe the unexpected change
- Explain the challenge it created
- Show how you adapted
- Describe the outcome
- Share lessons about flexibility
Example Answer:
“I was three weeks into my internship focused on network security when my supervisor left the company unexpectedly. I was reassigned to the web application security team—a completely different area where I had minimal experience.
The transition was challenging. I had to quickly learn new tools like Burp Suite and OWASP ZAP, understand web vulnerabilities, and adapt to the new team’s workflow—all while contributing meaningfully.
I took a structured approach. I spent evenings completing web security tutorials and hands-on labs. I requested pair-programming sessions with experienced team members, taking detailed notes. I asked questions frequently but made sure they were thoughtful and showed I’d tried to find answers first.
Within two weeks, I was contributing to security testing tasks. By internship’s end, I’d completed vulnerability assessments on three applications and developed a genuine interest in web application security—which became my career focus.
This experience taught me that cyber security professionals must be comfortable with constant change and learning. Technologies evolve rapidly, roles shift, and new threats emerge continuously. Adaptability and quick learning aren’t just nice to have—they’re essential survival skills in this field.”
Category 7: Ethics and Professional Judgment
Q14: Describe a situation where you faced an ethical dilemma. How did you handle it?
Model Answer Structure:
- Describe the ethical situation
- Explain the competing considerations
- Show your decision-making process
- Describe your action and reasoning
- Highlight your ethical principles
Important: Be careful with this question. Never describe illegal activities or major policy violations as things you actually did.
Example Answer:
“During a security assessment project, I discovered that one of my classmates was taking shortcuts by using automated tools without understanding the results, copying analysis from online sources, and essentially fabricating parts of their security report.
I faced a dilemma. Reporting them could damage our relationship and their academic standing. But their approach was ethically wrong—in real jobs, fake security assessments could leave organizations vulnerable.
I decided to talk to them privately first. I explained my concerns and offered to help them understand the material properly. I said if they were overwhelmed, we could discuss workload management or getting professor guidance, but submitting inaccurate security work was dangerous.
They admitted feeling overwhelmed and appreciated that I approached them directly. They redid their work properly, and I helped them learn the correct methodology. They improved significantly and actually became interested in the field.
This situation reinforced my belief that ethical conduct in cyber security is non-negotiable. Security professionals are trusted with critical responsibilities—shortcuts and dishonesty can have serious consequences. I also learned that addressing ethical concerns directly but compassionately often works better than immediate escalation. However, I would escalate if the initial conversation didn’t resolve the issue.”
Q15: How would you handle discovering that your company is not following proper security practices?
Model Answer Structure:
- Show you understand the complexity
- Explain your assessment approach
- Describe proper escalation
- Show commitment to both security and professionalism
- Emphasize doing the right thing
Example Answer:
“If I discovered inadequate security practices, I would first ensure I fully understood the situation. Sometimes what appears to be a security gap might have documented exceptions, risk acceptances, or compensating controls I’m not aware of.
I would gather clear evidence documenting the security gap, the potential risk, and the business impact. I’d research industry standards and regulatory requirements that apply to understand if it’s a compliance issue.
I would raise the concern through proper channels—starting with my immediate supervisor. I’d present the issue professionally, focused on organizational risk rather than blaming individuals. I’d provide specific recommendations with feasibility considerations.
If the issue wasn’t addressed and represented significant risk, I would escalate appropriately according to company policy—potentially to the CISO, compliance officer, or ethics hotline if one exists.
Throughout this process, I’d maintain professionalism and confidentiality. I understand that security decisions involve balancing risks, costs, and business needs. However, if the issue involved illegal activity or created unacceptable risk, I have a professional and potentially legal obligation to ensure it’s addressed.
This reflects my understanding that security professionals are guardians of organizational and customer trust. That responsibility sometimes requires difficult conversations and decisions.”
Section 4: Interview Body Language and Presence
Non-Verbal Communication Matters
Research shows that 55% of communication impact comes from body language, 38% from tone of voice, and only 7% from actual words. Your body language can support or undermine your answers.
Positive Body Language
Eye Contact:
- Maintain natural eye contact 60-70% of the time
- Don’t stare intensely—look away occasionally when thinking
- In panel interviews, make eye contact with all interviewers, not just the person asking questions
- Looking away while thinking is natural and acceptable
Posture:
- Sit upright but relaxed, not rigid
- Lean slightly forward to show engagement
- Don’t slouch or lean back too much
- Keep shoulders back and chest open
Hand Gestures:
- Use natural hand movements while explaining concepts
- Keep hands visible—don’t hide them under the table
- Avoid fidgeting with pens, papers, or your phone
- Rest hands on the table or in your lap when not gesturing
Facial Expressions:
- Smile genuinely when greeting interviewers
- Show appropriate expressions—concern when discussing problems, satisfaction when sharing successes
- Nod occasionally when interviewers speak to show you’re listening
- Avoid blank expressions or constant serious faces
Voice:
- Speak clearly at moderate pace
- Vary your tone—avoid monotone delivery
- Show enthusiasm when appropriate
- Don’t speak too softly or too loudly
- Pause briefly between thoughts
Negative Body Language to Avoid
Don’t:
- Cross your arms (appears defensive)
- Look at your watch or phone
- Fidget excessively
- Touch your face repeatedly
- Rock back and forth in your chair
- Interrupt interviewers
- Look at the ceiling or floor when answering
- Display nervous habits (pen clicking, leg bouncing)
Virtual Interview Tips
For video interviews:
Technical Setup:
- Test your camera, microphone, and internet beforehand
- Use good lighting—face a window or use a lamp
- Position camera at eye level
- Choose a clean, professional background
- Close unnecessary applications to prevent notifications
During the Interview:
- Look at the camera when speaking, not the screen
- Dress professionally from head to toe (in case you need to stand)
- Minimize distractions—quiet environment, pets secured
- Have notes nearby but don’t read directly from them
- Keep water available but off-camera
- Mute when not speaking if there’s background noise
Section 5: Common Interview Mistakes to Avoid
Mistake 1: Memorizing Instead of Understanding
Problem: Students memorize answers and sound robotic or can’t handle follow-up questions.
Solution: Understand concepts deeply. Practice explaining them in different ways. If you can’t explain it simply, you don’t understand it well enough.
Mistake 2: Being Too Technical or Too Vague
Problem: Either overwhelming interviewers with jargon or giving vague, empty answers.
Solution: Calibrate based on your audience. Start at a moderate technical level and adjust based on their reactions. Balance technical accuracy with clarity.
Mistake 3: Negative Speaking
Problem: Badmouthing previous employers, professors, or colleagues.
Solution: Frame challenges positively. Instead of “My professor was terrible at explaining,” say “I took initiative to supplement class materials with additional resources.”
Mistake 4: Not Asking Questions
Problem: When asked “Do you have questions for us?” saying “No, you covered everything.”
Solution: Always prepare 5-6 thoughtful questions about the role, team, company culture, growth opportunities, or technologies used. Not asking questions suggests lack of interest.
Mistake 5: Rambling Answers
Problem: Answering for 5+ minutes without clear structure or endpoint.
Solution: Use STAR method. Keep answers focused and concise—2 to 3 minutes maximum. Practice timing your responses.
Mistake 6: Saying “I Don’t Know” Without More
Problem: Just saying “I don’t know” and stopping.
Solution: If you don’t know something, say: “I’m not familiar with that specific technology, but based on my understanding of similar concepts, I would approach it like… Can you tell me more so I can learn?” Shows you can think through unfamiliar situations.
Mistake 7: Not Preparing Questions
Problem: Generic questions you could ask any company.
Solution: Research the company beforehand. Ask specific questions about their security challenges, technologies, or recent news.
Mistake 8: Lying or Exaggerating
Problem: Claiming skills you don’t have or exaggerating experiences.
Solution: Be honest about your level. It’s better to say “I have foundational knowledge and I’m eager to develop expertise” than claim expertise you’ll fail to demonstrate.
🛡️ Learn Real-World SOC Scenarios & Best Practices
🧠 Read SOC Analyst Guides →
Section 6: Questions YOU Should Ask Interviewers
Asking intelligent questions shows genuine interest and helps you evaluate if the job is right for you.
About the Role
- “Can you describe what a typical day or week looks like in this position?”
- “What are the immediate priorities for the person in this role over the first 3 months?”
- “What security tools and technologies does the team currently use?”
- “How is success measured in this role?”
- “What are the biggest security challenges the organization is currently facing?”
About the Team and Culture
- “Can you tell me about the team structure and who I would work with most closely?”
- “How does the security team collaborate with other departments?”
- “What opportunities are there for mentorship or learning from senior team members?”
- “How does the organization support continuous learning and professional development in cyber security?”
- “What’s your favorite thing about working here?”
About Growth and Development
- “What does the career progression path look like for this role?”
- “Does the company support professional certifications like Security+, CEH, or CISSP?”
- “Are there opportunities to attend security conferences or training?”
- “How often do performance reviews happen, and how is feedback provided?”
About the Organization
- “How does leadership prioritize security initiatives?”
- “Can you tell me about a recent security project or initiative the team worked on?”
- “What’s the security team’s relationship with executive management?”
- “How does the organization stay current with emerging threats and security trends?”
About Next Steps
- “What are the next steps in the interview process?”
- “When can I expect to hear back about next steps?”
- “Is there anything about my background or experience you’d like me to clarify?”
Important: Don’t ask about salary, vacation, or work-from-home policies in early interviews. Save those for later stages or after receiving an offer.
Section 7: Final Preparation Checklist
One Week Before Interview
- Review all technical concepts from Part 1
- Practice STAR stories aloud
- Research the company thoroughly
- Prepare 6-8 questions to ask
- Review your resume—be ready to explain everything
- Test interview location route or video setup
One Day Before Interview
- Review your prepared stories
- Get good sleep—cognitive performance matters
- Prepare your outfit
- Print extra copies of resume
- Charge your phone/laptop
- Review company’s recent news
Interview Day Morning
- Eat a good breakfast
- Dress professionally
- Arrive 10-15 minutes early (or log in 5 minutes early for virtual)
- Bring notebook, pen, resume copies
- Turn off phone or set to silent
- Take a few deep breaths to calm nerves
During the Interview
- Smile and make eye contact
- Listen carefully to questions
- Take a moment to think before answering
- Use STAR method for behavioral questions
- Ask for clarification if needed
- Show enthusiasm for the role
- Take brief notes if helpful
- Thank interviewers for their time
After the Interview
- Send thank-you email within 24 hours
- Mention specific topics discussed
- Reiterate your interest
- Don’t obsess over small mistakes
- Reflect on what went well and what to improve
- Follow up appropriately if you don’t hear back
Section 8: Sample Thank-You Email
Subject: Thank you for the [Job Title] interview
Dear [Interviewer Name],
Thank you for taking the time to meet with me today to discuss the Cyber Security Analyst position at [Company Name]. I greatly enjoyed learning about your security team’s initiatives and the organization’s approach to protecting critical infrastructure.
Our conversation about [specific topic discussed] was particularly interesting. It reinforced my enthusiasm for this role and confirmed that my experience with [relevant skill/project] aligns well with the team’s needs.
I’m excited about the opportunity to contribute to [specific company initiative or challenge discussed], and I’m confident my skills in [relevant areas] would allow me to make meaningful contributions to your security program.
Thank you again for your consideration. Please don’t hesitate to reach out if you need any additional information. I look forward to hearing about next steps.
Best regards,
[Your Name]
[Your Phone]
[Your LinkedIn Profile]
🗣️ Ace Behavioural Interviews Like a Pro!
Module 4: Additional Preparation Elements

Why Your Resume Matters
Your resume is your first impression. Recruiters spend only 6-8 seconds scanning each resume. If yours doesn’t immediately show relevant skills and experience, it gets rejected before you ever get an interview.
Resume Structure for Cyber Security Roles
- Header Section
Include:
- Full name (larger font, bold)
- Phone number (professional voicemail message)
- Professional email address (firstname.lastname format, not party_guy123)
- LinkedIn profile URL (customized, not default random numbers)
- GitHub profile (if you have security projects)
- Location (city and state, not full address)
Don’t include:
- Photo (unless specifically requested)
- Age or date of birth
- Marital status
- Religion or political affiliations
- Full home address
- Professional Summary (3-4 lines)
This appears right below your header. It’s your elevator pitch.
Bad Example:
“Recent graduate looking for entry-level cyber security position to gain experience and grow my skills in the industry.”
Good Example:
“Cyber Security professional with hands-on experience in penetration testing, vulnerability assessment, and incident response. Proficient in Linux, Python, and security tools including Nmap, Metasploit, and Burp Suite. Completed 50+ CTF challenges and built home lab environment for practical security testing. Passionate about protecting organizations from emerging threats through proactive security measures.”
Formula for Professional Summary:
- Line 1: Your professional identity + key areas of expertise
- Line 2: Specific technical skills and tools
- Line 3: Quantifiable achievements or unique qualifications
- Line 4: What you bring to the organization
- Technical Skills Section
Organize skills into categories for easy scanning:
Example:
Security Skills: Vulnerability Assessment, Penetration Testing, Incident Response, Threat Analysis, VAPT, Security Auditing
Security Tools: Nmap, Metasploit, Burp Suite, Wireshark, OWASP ZAP, Kali Linux, John the Ripper, Hashcat, Hydra
Programming/Scripting: Python, Bash, PowerShell, SQL
Operating Systems: Linux (Ubuntu, Kali), Windows, Windows Server
Networking: TCP/IP, DNS, DHCP, VPN, Firewalls, IDS/IPS
Web Security: OWASP Top 10, SQL Injection, XSS, CSRF, Session Management
Compliance & Frameworks: NIST Cybersecurity Framework, MITRE ATT&CK, ISO 27001, GDPR
SIEM/SOC Tools: Splunk, ELK Stack, Wazuh (if applicable)
Cloud Security: AWS/Azure Security Basics (if applicable)
Important Tips:
- Only list skills you actually have—you’ll be tested on these
- Prioritize skills mentioned in the job description
- Don’t rate yourself (like “Python: 7/10”)—just list what you know
- Update this section for each job application
- Education Section
Format:
Degree Name (Bachelor of Technology in Computer Science)
Institution Name, Location
Graduation Date (Month Year) or Expected Graduation (Month Year)
GPA: (only if 3.5 or above)
Relevant Coursework: Network Security, Cryptography, Ethical Hacking, Web Application Security, Operating Systems, Computer Networks
Academic Projects:
- Built secure web application with authentication and authorization mechanisms
- Conducted penetration testing assessment on vulnerable web applications
- Implemented encryption algorithms in Python for secure communication
- Experience Section (Most Important)
Even without formal work experience, you can include:
- Internships
- Academic projects
- Personal projects
- Freelance work
- Volunteer work
- CTF competitions
- Bug bounty participation
- Open source contributions
Format for Each Entry:
Job Title
Company Name, Location
Duration (Month Year – Month Year)
Use bullet points starting with action verbs. Follow this formula:
Action Verb + Task + Tool/Method + Result/Impact
Bad Examples:
- Responsible for security testing
- Worked on incident response
- Helped with vulnerability scanning
Good Examples:
- Conducted vulnerability assessments on 15+ web applications using Burp Suite and OWASP ZAP, identifying 40+ security flaws including critical SQL injection vulnerabilities
- Analyzed 200+ security alerts daily using SIEM platform, reducing false positive rate by 30% through custom correlation rules
- Performed penetration testing on internal network infrastructure using Metasploit and custom Python scripts, documenting findings in detailed reports for management
- Assisted in incident response for ransomware attack, containing the threat within 2 hours and preventing data exfiltration to external servers
- Developed automated Python scripts for log analysis, reducing incident detection time from 4 hours to 30 minutes
- Participated in weekly threat hunting activities, discovering 3 previously undetected compromised endpoints through IOC analysis
- Created and delivered security awareness training to 100+ employees, reducing phishing click rates by 45%
Power Action Verbs for Cyber Security:
For Analysis: Analyzed, Assessed, Evaluated, Investigated, Examined, Identified, Detected, Monitored
For Implementation: Implemented, Deployed, Configured, Established, Developed, Created, Built, Designed
For Improvement: Optimized, Enhanced, Strengthened, Reduced, Improved, Increased, Streamlined
For Leadership: Led, Coordinated, Managed, Mentored, Trained, Presented, Collaborated
For Problem-Solving: Resolved, Troubleshot, Remediated, Mitigated, Prevented, Secured, Protected
- Certifications Section
List relevant certifications with dates:
Example:
Certifications:
- CompTIA Security+ | Credential ID: COMP001234567 | Valid: Oct 2024 – Oct 2027
- Certified Ethical Hacker (CEH) | EC-Council | Obtained: August 2025
- Google Cybersecurity Professional Certificate | Coursera | Completed: July 2025
If you’re pursuing certifications:
- CompTIA Security+ (In Progress – Expected: December 2025)
- Projects Section
If you don’t have work experience, make this section prominent.
Format:
Project Name | Tools Used | Duration
Brief description of project (1-2 lines) + bullet points showing what you did and learned
Example:
Home Penetration Testing Lab | VirtualBox, Kali Linux, Metasploitable, DVWA | Jan 2025 – Present
Built comprehensive home lab environment for practicing ethical hacking and penetration testing techniques
- Set up virtualized network with 5+ vulnerable machines including Metasploitable, DVWA, and Windows Server
- Performed reconnaissance, vulnerability scanning, exploitation, and privilege escalation on target systems
- Documented complete penetration testing reports following industry standards
- Practiced OWASP Top 10 vulnerabilities exploitation and remediation techniques
Web Application Security Scanner | Python, SQL | September 2025
Developed automated tool to scan web applications for common vulnerabilities
- Implemented detection modules for SQL injection, XSS, and directory traversal vulnerabilities
- Created detailed HTML reports with severity ratings and remediation recommendations
- Tested on 10+ intentionally vulnerable applications with 85% detection accuracy
- Published code on GitHub with comprehensive documentation
- Additional Sections (Optional)
Achievements:
- Winner, College Cyber Security CTF Competition (March 2025)
- Ranked in Top 5%, TryHackMe Platform (2000+ points)
- Found and responsibly disclosed 2 security vulnerabilities through bug bounty programs
Publications/Blog:
- Active cybersecurity blog with 20+ articles on penetration testing and web security
- Published research paper on “Modern Phishing Techniques” in college journal
Professional Memberships:
- Student Member, ISACA
- Member, OWASP Foundation
Resume Formatting Guidelines
Do:
- Use clean, professional template (not overly designed)
- Stick to one page for entry-level, two pages for experienced
- Use consistent formatting throughout
- Use 10-12 point font (Arial, Calibri, or Times New Roman)
- Save and send as PDF to preserve formatting
- Use bullet points, not paragraphs
- Include plenty of white space—don’t cram everything
Don’t:
- Use colors (unless very subtle and professional)
- Use multiple fonts
- Include personal pronouns (I, me, my)
- Write in complete sentences—use bullet fragments
- Use tiny fonts to fit more content
- Include irrelevant experience (high school activities, unrelated jobs)
- Use generic templates from Microsoft Word
Tailoring Your Resume for Each Job
Never send the same generic resume to every job. Customize for each application:
Step 1: Read the job description carefully and highlight key requirements
Step 2: Identify which of your skills and experiences match
Step 3: Reorder your skills section to prioritize what they’re looking for
Step 4: Adjust your project descriptions to emphasize relevant aspects
Step 5: Use exact keywords from the job description (many companies use ATS – Applicant Tracking Systems that scan for keywords)
Example:
If the job emphasizes “incident response” and “SIEM tools,” make sure these terms appear in your resume where relevant, not just “security monitoring” or “log analysis.”
Common Resume Mistakes to Avoid
Mistake 1: Lying or Exaggerating
Never claim skills or certifications you don’t have. You will be caught during technical interviews.
Mistake 2: Typos and Grammar Errors
Proofread 5+ times. Ask friends to review. Use Grammarly. One typo can eliminate you.
Mistake 3: Too Much Detail
Don’t explain every minor task. Focus on accomplishments and impact.
Mistake 4: Passive Language
“Was responsible for security testing” is weak. “Conducted security testing” is strong.
Mistake 5: No Quantifiable Results
“Improved security” is vague. “Reduced security incidents by 40%” is impressive.
Mistake 6: Including Irrelevant Information
Your summer job at a restaurant is only relevant if you’re showing work ethic for your very first tech role. Otherwise, skip it.
Mistake 7: Outdated Skills
Don’t list irrelevant or outdated technologies unless the job specifically requires them.
Section 2: Building a Cyber Security Portfolio

Why You Need a Portfolio
A portfolio proves you can actually do the work, not just talk about it. It differentiates you from hundreds of other candidates with similar resumes.
What to Include in Your Portfolio
- Personal Website or GitHub Profile
Create a professional online presence showcasing your work.
Personal Website Should Include:
- About Me section (who you are, what you do)
- Skills and expertise
- Projects showcase with descriptions
- Blog posts or articles (optional but valuable)
- Contact information
- Links to LinkedIn, GitHub, certifications
GitHub Profile Should Include:
- Complete profile with professional photo and bio
- Well-documented repositories with README files
- Security tools you’ve built
- Scripts for automation
- Write-ups of CTF challenges
- Contributions to open source security projects
- Documented Projects
For each project in your portfolio:
Include:
- Clear project title and objective
- Technologies and tools used
- Problem statement (what security issue you addressed)
- Your approach and methodology
- Code or configurations (where appropriate)
- Screenshots or demonstrations
- Challenges faced and how you solved them
- Results and lessons learned
- Professional documentation
Project Ideas:
Beginner Level:
- Password strength checker tool
- Network scanner using Python
- Log file analyzer
- Phishing email detector
- Basic encryption/decryption tool
- Port scanner with service detection
Intermediate Level:
- Web application vulnerability scanner
- Automated security audit tool
- Intrusion detection system
- Security dashboard using Python and Splunk
- Malware analysis report
- Penetration testing report on authorized targets
Advanced Level:
- Custom exploit development
- Security automation framework
- Threat intelligence aggregation platform
- Machine learning for anomaly detection
- Complete penetration testing engagement documentation
- Open source security tool contribution
- CTF Write-ups
Capture the Flag competitions demonstrate practical skills.
What to Document:
- Challenge name and category
- Initial analysis and reconnaissance
- Tools used
- Step-by-step solution process
- Flags captured
- Lessons learned
- Alternative approaches
Popular CTF Platforms:
- TryHackMe
- HackTheBox
- PicoCTF
- OverTheWire
- CTFtime
- VulnHub
- Blog Posts and Technical Writing
Writing demonstrates deep understanding and communication skills.
Blog Topics:
- How-to guides (How to set up a home penetration testing lab)
- Vulnerability explanations (Understanding SQL Injection attacks)
- Tool reviews and tutorials
- Security concepts explained simply
- CTF challenge walkthroughs
- Analysis of recent security breaches
- Personal learning journey and lessons
Where to Blog:
- Medium
- Dev.to
- Personal website
- LinkedIn articles
- GitHub pages
- Certifications and Training Completion
Document your continuous learning:
- Digital badges from certification providers
- Course completion certificates
- Training completion screenshots
- Conference attendance certificates
- Contributions and Community Involvement
Show you’re part of the security community:
- Open source contributions
- Forum participation (Stack Overflow, Reddit r/netsec)
- Security conference attendance or volunteering
- Bug bounty findings (responsibly disclosed)
- Mentoring or helping others learn
Portfolio Best Practices
Quality Over Quantity:
Better to have 3-5 excellent, well-documented projects than 20 half-finished ones.
Keep It Updated:
Add new projects and remove outdated content regularly.
Make It Accessible:
Ensure everything is easy to find and navigate. Test all links.
Professional Presentation:
Use proper grammar, formatting, and professional tone throughout.
Show Your Process:
Don’t just show results—explain your thinking and methodology.
Be Careful with Sensitive Information:
Never share proprietary information, company secrets, or vulnerabilities in production systems without permission.
Section 3: Cyber Security Certifications

Why Certifications Matter
Certifications validate your knowledge, show commitment to the field, and often satisfy job requirements. Many employers require or prefer specific certifications.
Entry-Level Certifications
CompTIA Security+
- Best for: Beginners entering cyber security
- Topics: Network security, threats and vulnerabilities, access control, cryptography
- Cost: Around $370 USD
- Study Time: 2-3 months
- Value: Widely recognized baseline certification, required for many government jobs
Google Cybersecurity Professional Certificate
- Best for: Complete beginners
- Topics: Security frameworks, network security, incident response, Python, SIEM tools
- Cost: Coursera subscription (around $49/month)
- Study Time: 3-6 months
- Value: Great foundation, includes hands-on labs, recognized by employers
CompTIA CySA+ (Cybersecurity Analyst)
- Best for: SOC analysts, threat analysts
- Topics: Threat detection, log analysis, SIEM, incident response
- Cost: Around $380 USD
- Study Time: 3-4 months
- Value: Bridges gap between Security+ and advanced certifications
Intermediate Certifications
Certified Ethical Hacker (CEH)
- Best for: Penetration testers, ethical hackers
- Topics: Reconnaissance, scanning, exploitation, post-exploitation, web application hacking
- Cost: Around $1,200 USD (with training)
- Study Time: 3-6 months
- Value: Internationally recognized, good for penetration testing roles
CompTIA PenTest+
- Best for: Penetration testers
- Topics: Planning, scoping, information gathering, vulnerability scanning, exploitation
- Cost: Around $380 USD
- Study Time: 3-4 months
- Value: Hands-on practical exam, more affordable than CEH
GIAC Security Essentials (GSEC)
- Best for: Security practitioners
- Topics: Access control, cryptography, incident response, network security
- Cost: Around $2,000 USD
- Study Time: 4-6 months
- Value: Highly respected, rigorous exam
Advanced Certifications
Offensive Security Certified Professional (OSCP)
- Best for: Experienced penetration testers
- Topics: Hands-on penetration testing, buffer overflows, privilege escalation
- Cost: Around $1,650 USD (with lab access)
- Study Time: 6-12 months
- Value: Extremely respected in industry, entirely practical exam (24-hour hands-on test)
Certified Information Systems Security Professional (CISSP)
- Best for: Security managers, architects, consultants
- Topics: 8 domains covering all aspects of information security
- Cost: Around $700 USD
- Study Time: 6-12 months
- Requirements: 5 years of paid work experience (or 4 years + degree)
- Value: Gold standard for security leadership roles
GIAC Certified Incident Handler (GCIH)
- Best for: Incident responders
- Topics: Incident handling, malware analysis, intrusion detection
- Cost: Around $2,000 USD
- Study Time: 4-6 months
- Value: Excellent for SOC and IR roles
Specialized Certifications
For Cloud Security:
- AWS Certified Security – Specialty
- Microsoft Certified: Azure Security Engineer Associate
- Google Professional Cloud Security Engineer
For Application Security:
- Certified Secure Software Lifecycle Professional (CSSLP)
- GIAC Web Application Penetration Tester (GWAPT)
For Forensics:
- GIAC Certified Forensic Analyst (GCFA)
- Certified Computer Forensics Examiner (CCFE)
Certification Strategy
For Entry-Level Job Seekers:
Start with Security+ → then specialize based on your career path
For Penetration Testing Career:
Security+ → CEH or PenTest+ → OSCP
For SOC Analyst Career:
Security+ → CySA+ → GCIH
For Security Engineering:
Security+ → CISSP (after gaining experience)
Free and Low-Cost Learning Resources
Don’t feel pressured to buy expensive training. Many excellent free resources exist:
Free Certifications:
- Cisco Cybersecurity Essentials
- IBM Cybersecurity Analyst Professional Certificate (free audit)
- Microsoft Security, Compliance, and Identity Fundamentals
Study Resources:
- Professor Messer (free Security+ video course)
- Cybrary (free basic courses)
- YouTube channels dedicated to specific certifications
- Official certification study guides from libraries
- Reddit communities for specific certifications
- Study groups and Discord servers
Section 4: Job Search Strategies
Where to Find Cyber Security Jobs
Job Boards:
- LinkedIn Jobs (most important)
- Indeed
- Glassdoor
- CyberSecJobs.com
- Dice.com (tech-focused)
- USAJobs.gov (government positions)
- Company career pages directly
Specialized Security Job Boards:
- InfoSec Jobs
- Cyber Security Jobsite
- ClearanceJobs.com (if you have/can get security clearance)
Networking Platforms:
- LinkedIn (connect with security professionals, recruiters)
- Security conferences (virtual and in-person)
- Local security meetups (OWASP chapters, security user groups)
- College career fairs
- Alumni networks
Job Search Best Practices
- Optimize Your LinkedIn Profile
Your LinkedIn is your online resume—make it strong:
Profile Photo:
- Professional headshot
- Clean background
- Appropriate attire
- Friendly expression
Headline:
Don’t just put “Student” or “Looking for opportunities”
Use: “Cyber Security Analyst | Penetration Testing | OWASP Top 10 | Python | Security+ Certified”
About Section:
Write 3-4 paragraphs about:
- Who you are professionally
- Your passion for cyber security
- Your key skills and experiences
- What you’re looking for
Experience Section:
Mirror your resume but you can be slightly more detailed
Skills Section:
Add 40-50 relevant skills and ask connections to endorse them
Recommendations:
Request recommendations from professors, internship supervisors, project teammates
Activity:
Post or share security content regularly (articles, thoughts, achievements)
- Apply Strategically
Don’t Just Click “Easy Apply” on Everything:
Quality applications are better than quantity
Application Strategy:
- Research the company thoroughly
- Customize your resume for each application
- Write a tailored cover letter (when requested or optional)
- Follow up appropriately after 1-2 weeks
Entry-Level Reality Check:
- Don’t be discouraged by “2-3 years experience required”—apply anyway if you have strong projects and skills
- Many “entry-level” jobs have inflated requirements
- Internships and projects count as experience
- Leverage Your Network
80% of jobs are filled through networking, not applications.
How to Network:
- Connect with cyber security professionals on LinkedIn
- Attend local security meetups and conferences
- Join online security communities
- Participate in CTF competitions and meet people
- Reach out to alumni in security roles
- Informational interviews (ask people about their jobs, not for jobs directly)
Networking Message Template:
“Hi [Name],
I’m [Your Name], currently [your situation—student, recent grad, career changer]. I’m passionate about cyber security, particularly [specific area].
I came across your profile and was impressed by your work in [something specific about them]. I’d love to learn more about your experience in [their role/company].
Would you be open to a brief 15-minute call? I’m not asking for a job—I’m just seeking advice from someone whose career path I admire.
Thank you for considering!
Best regards,
[Your Name]”
- Work with Recruiters
Recruiters can help, but be strategic:
Good Recruiters:
- Specialize in cyber security
- Communicate clearly about roles
- Provide interview preparation help
- Give honest feedback
Red Flags:
- Promise jobs that seem too good to be true
- Pressure you to accept offers quickly
- Don’t clearly explain the role or company
- Ask for money (legitimate recruiters never charge candidates)
Entry-Level Position Titles to Search For
- Junior Security Analyst
- SOC Analyst (Tier 1)
- Security Operations Analyst
- Cybersecurity Analyst
- Information Security Analyst
- Junior Penetration Tester
- Security Engineer (Associate/Junior)
- Incident Response Analyst (Junior)
- Vulnerability Analyst
- IT Security Specialist
Alternative Paths Into Cyber Security
If you can’t find direct security roles:
Entry Points:
- IT Help Desk → SOC Analyst
- Network Administrator → Security Engineer
- System Administrator → Security Analyst
- QA Tester → Security Tester
- Developer → Application Security Engineer
Many security professionals started in general IT and transitioned.
Section 5: Handling Technical Assessments
Types of Technical Assessments
- Take-Home Assignments
You’re given a project to complete in a few days.
Common Assignments:
- Analyze a packet capture file and identify suspicious activity
- Perform vulnerability assessment on a test application
- Write security automation scripts
- Create incident response plan for a scenario
- Security architecture design
How to Excel:
- Read instructions carefully and follow them exactly
- Document your process and thinking
- Present results professionally (clear reports, organized code)
- Meet the deadline—late submissions are usually rejected
- Test everything before submitting
- Include a README explaining your work
- Live Coding/Scripting Challenges
You write code while interviewers watch.
Common Tasks:
- Write Python script to parse log files
- Create simple network scanner
- Implement basic encryption algorithm
- Parse and analyze data structures
- Automate security tasks
How to Excel:
- Talk through your thinking process
- Ask clarifying questions before starting
- Write clean, commented code
- Test your code as you go
- Don’t panic if you get stuck—explain your thought process
- Practice on platforms like HackerRank or LeetCode beforehand
- Practical Lab Exercises
You’re given access to a lab environment to solve security challenges.
Common Scenarios:
- Find and exploit vulnerabilities in web application
- Analyze malware sample
- Investigate security incident using logs
- Configure security tools
- Privilege escalation on Linux/Windows systems
How to Excel:
- Take notes throughout the exercise
- Document your methodology
- Use systematic approaches (don’t just randomly try things)
- Explain your findings clearly
- Show your work even if you don’t complete everything
- Technical Interviews with Whiteboard
You solve problems or explain concepts at a whiteboard.
Common Requests:
- Draw network architecture with security controls
- Explain how a specific attack works
- Design security solution for a scenario
- Trace the flow of an attack through systems
How to Excel:
- Start by clarifying the problem
- Think aloud—share your reasoning
- Draw clearly with labels
- Ask questions throughout
- Organize your whiteboard space logically
Practice Resources for Technical Assessments
For Coding:
- HackerRank
- LeetCode
- CodeSignal
- Python security automation tutorials
For Security Skills:
- TryHackMe (guided labs)
- HackTheBox (advanced challenges)
- PentesterLab
- DVWA (Damn Vulnerable Web Application)
- PortSwigger Web Security Academy
For Incident Response:
- Security Blue Team (free and paid courses)
- SANS Cyber Aces tutorials
- Incident response scenarios on GitHub
Section 6: Salary Negotiation
Research Before Negotiating
Know your worth before discussing salary:
Research Resources:
- Glassdoor salary reports
- PayScale
- LinkedIn Salary Insights
- Levels.fyi (for tech companies)
- Robert Half Salary Guide for Technology
- Ask people in similar roles (networking)
Factors Affecting Salary:
- Geographic location (San Francisco vs. smaller cities)
- Company size (startups vs. enterprises)
- Industry (finance and healthcare often pay more)
- Your experience and skills
- Certifications
- Education level
- Cost of living in the area
Typical Entry-Level Cyber Security Salaries
United States (2025):
- SOC Analyst: $55,000 – $75,000
- Junior Security Analyst: $60,000 – $80,000
- Penetration Tester (Junior): $65,000 – $85,000
- Security Engineer (Entry): $70,000 – $95,000
Higher in major tech hubs (San Francisco, New York, Seattle).
India (2025):
- SOC Analyst: ₹3,50,000 – ₹6,00,000
- Security Analyst: ₹4,00,000 – ₹7,00,000
- Penetration Tester: ₹4,50,000 – ₹8,00,000
Negotiation Strategy
When They Ask About Salary Expectations:
Early in Process:
“I’m focused on finding the right role fit right now. I’m sure we can agree on fair compensation once we determine I’m the right candidate. What’s the budgeted range for this position?”
If Pushed:
Give a range based on research: “Based on my research for this role in [location], I’m looking for something in the $65,000 to $75,000 range, but I’m flexible depending on the complete compensation package and growth opportunities.”
After Receiving an Offer:
Don’t Accept Immediately:
“Thank you for the offer! I’m excited about this opportunity. Can I have a couple of days to review everything carefully?”
Review the Complete Package:
- Base salary
- Bonuses
- Health insurance
- Retirement contributions
- Vacation/PTO days
- Remote work options
- Professional development budget
- Certification reimbursement
- Relocation assistance
- Stock options (if applicable)
Negotiation Email Template:
“Dear [Hiring Manager],
Thank you again for the offer for the [Position] role. I’m very excited about the opportunity to join [Company] and contribute to [specific project/team].
After carefully reviewing the offer, I was hoping we could discuss the base salary. Based on my research for similar positions in [location], as well as my [specific skills/certifications/experience], I was expecting something closer to $[X amount].
I’m confident I can bring significant value to the team through [specific contributions you’ll make]. Is there flexibility in the compensation package to reach $[desired amount]?
I’m happy to discuss this further and am looking forward to joining the team.
Best regards,
[Your Name]”
Important Negotiation Rules:
Do:
- Always negotiate professionally and politely
- Focus on your value, not your needs
- Be prepared to justify your request
- Consider the full package, not just salary
- Get everything in writing
Don’t:
- Lie about other offers (it’s a small industry)
- Make ultimatums unless you’re prepared to walk away
- Accept verbally then try to renegotiate
- Be aggressive or entitled
- Forget to express enthusiasm for the role
Section 7: Continuous Learning Resources
Free Online Learning Platforms
Comprehensive Courses:
- Cybrary (free and paid cyber security courses)
- Professor Messer (excellent Security+ preparation)
- SANS Cyber Aces (free tutorials)
- YouTube channels (Network Chuck, John Hammond, David Bombal, LiveOverflow)
Hands-On Practice:
- TryHackMe (structured learning paths)
- HackTheBox (advanced challenges)
- OverTheWire (wargames for beginners)
- PentesterLab (web application security)
- PortSwigger Web Security Academy (free, excellent)
Documentation and Reading:
- OWASP (web application security)
- NIST Cybersecurity Framework
- MITRE ATT&CK
- CIS Controls
- Security blogs and news sites
Books Worth Reading
For Beginners:
- “The Web Application Hacker’s Handbook” by Dafydd Stuttard
- “Hacking: The Art of Exploitation” by Jon Erickson
- “Practical Malware Analysis” by Michael Sikorski
- “Linux Basics for Hackers” by OccupyTheWeb
For Networking:
- “TCP/IP Illustrated” by Richard Stevens
- “Network Security Essentials” by William Stallings
For Career Development:
- “The Cybersecurity Career Handbook” by Helen Patton
- “Tribe of Hackers” by Marcus J. Carey (interviews with security pros)
News and Industry Updates
Stay current with security news:
Websites:
- Krebs on Security
- The Hacker News
- Dark Reading
- BleepingComputer
- Threatpost
- Security Week
Podcasts:
- Darknet Diaries (storytelling about hacks)
- Risky Business
- Security Now
- Malicious Life
Social Media:
Follow security researchers and professionals on:
- Twitter (X) – #infosec, #cybersecurity
- Reddit (r/netsec, r/AskNetsec, r/cybersecurity)
Communities to Join
Online:
- Discord servers (TryHackMe, HackTheBox communities)
- OWASP chapters
- Reddit security communities
- Security Stack Exchange
Local:
- DEFCON groups
- OWASP local chapters
- Security BSides conferences
- Local security meetups
Conferences to Attend
Major Conferences:
- DEF CON (Las Vegas)
- Black Hat
- RSA Conference
- BSides (local, smaller, more accessible)
Student Benefits:
Many conferences offer discounted or free student tickets.
Section 8: Building Your Home Lab
Why Build a Home Lab
Hands-on practice is essential. A home lab lets you:
- Practice without risking real systems
- Test new tools safely
- Break things and learn
- Build portfolio projects
- Prepare for certifications
- Experiment freely
Basic Home Lab Setup
What You Need:
Hardware:
- Decent computer (8GB RAM minimum, 16GB recommended)
- 100GB+ free disk space
- Modern processor (Intel i5/Ryzen 5 or better)
Software (All Free):
- Virtualization: VirtualBox or VMware Workstation Player
- Operating Systems:
- Kali Linux (penetration testing)
- Ubuntu/Debian (general Linux practice)
- Windows 10 (target practice with trial version)
- Windows Server (trial version)
- Vulnerable Machines:
- Metasploitable 2/3
- DVWA
- OWASP WebGoat
- VulnHub machines
Home Lab Ideas
Network Lab:
- Set up multiple VMs simulating small company network
- Configure firewall rules
- Practice network scanning with Nmap
- Set up VPN connections
- Analyze traffic with Wireshark
Web Security Lab:
- Install DVWA or WebGoat
- Practice OWASP Top 10 exploits
- Learn Burp Suite
- Test security tools
- Build and secure your own web applications
SOC Analyst Lab:
- Set up ELK stack or Splunk
- Generate logs from various sources
- Create correlation rules
- Practice incident detection
- Build security dashboards
Active Directory Lab:
- Set up Windows Server domain controller
- Join Windows clients to domain
- Practice common AD attacks
- Learn PowerShell for security
Lab Safety Rules
Critical Rules:
- Keep lab isolated from your home network (use host-only networking)
- Never practice attacks on systems you don’t own or have permission for
- Don’t expose vulnerable machines to the internet
- Keep lab VMs updated and snapshot regularly
- Back up your configurations
Section 9: Industry Trends to Know
Current Hot Topics in Cyber Security (2025)
- AI and Machine Learning in Security
- AI-powered threat detection
- Automated incident response
- Security AI tools (ChatGPT for security, code analysis)
- Adversarial AI attacks
- Zero Trust Architecture
- “Never trust, always verify” model
- Identity-based security
- Microsegmentation
- Continuous authentication
- Cloud Security
- Securing AWS, Azure, Google Cloud
- Container security (Docker, Kubernetes)
- Cloud-native security tools
- Shared responsibility model
- Ransomware Evolution
- Double and triple extortion
- Ransomware-as-a-Service
- Supply chain attacks
- Backup security critical
- IoT and OT Security
- Smart device vulnerabilities
- Industrial control systems
- Medical device security
- Connected vehicle security
- Supply Chain Attacks
- Software supply chain risks
- Third-party vendor risks
- Open source vulnerabilities
- Code signing and verification
- Privacy Regulations
- GDPR compliance
- CCPA and privacy laws
- Data protection requirements
- Privacy-by-design
- DevSecOps
- Security integrated into development
- Shift-left security
- Security automation in CI/CD
- Infrastructure as Code security
Emerging Career Paths
Growing Roles:
- Cloud Security Engineer
- DevSecOps Engineer
- AI Security Specialist
- Threat Intelligence Analyst
- IoT Security Specialist
- Blockchain Security Analyst
- Privacy Engineer
The Reality Check
Job Search Reality:
- You’ll get rejected—a lot. It’s normal.
- Entry-level positions are competitive
- You might need to apply to 50-100 positions
- First job is the hardest to get
- Once you have experience, opportunities increase dramatically
Don’t Give Up When:
- You get rejected from your dream company (reapply later)
- You don’t hear back from applications (follow up politely)
- You fail a technical assessment (learn from it and improve)
- You don’t know something in an interview (nobody knows everything)
Success Mindset
Things Successful Candidates Do:
- Consistent Learning:
Spend 1-2 hours daily learning something new—watch tutorials, practice on TryHackMe, read security news. - Build in Public:
Share your learning journey on LinkedIn. Post about projects, certifications, achievements. - Help Others:
Answer questions in forums, help classmates. Teaching reinforces your knowledge. - Stay Curious:
When you see a security breach in the news, research how it happened. - Practice Communication:
Technical skills get you interviews. Communication skills get you jobs. - Network Genuinely:
Build real relationships, not just transactional connections. - Document Everything:
Keep track of what you learn, projects you complete, problems you solve.
30-Day Action Plan Before Interview
Week 1: Technical Review
- Days 1-2: Review all Part 1 questions on fundamentals and networking
- Days 3-4: Practice Linux commands and scripting
- Days 5-7: Review web security and cryptography concepts
Week 2: Hands-On Practice
- Days 8-10: Complete 5 TryHackMe rooms relevant to job
- Days 11-13: Work on portfolio project or documentation
- Day 14: Review and update GitHub/portfolio
Week 3: Behavioral Preparation
- Days 15-17: Write out 10 STAR stories
- Days 18-19: Practice stories aloud, record yourself
- Days 20-21: Mock interviews with friends or online platforms
Week 4: Final Preparation
- Days 22-23: Research target companies thoroughly
- Days 24-25: Prepare questions to ask interviewers
- Day 26: Update and tailor resume and LinkedIn
- Day 27: Review industry trends and recent security news
- Day 28: Light review of technical concepts (don’t cram)
- Day 29: Prepare interview outfit, test tech setup
- Day 30: Rest, relax, get good sleep
Interview Day Confidence Boosters
Morning Of:
- Listen to motivating music
- Review your achievement list (remind yourself of your capabilities)
- Do power poses (research shows it reduces anxiety)
- Arrive/log in early
- Positive self-talk: “I’ve prepared well. I can do this.”
During Interview:
- Remember: Interviewers want you to succeed
- They’re evaluating fit, not trying to trick you
- It’s okay to say “I don’t know, but here’s how I’d find out”
- Pause before answering—thinking shows thoughtfulness
- Smile and show enthusiasm
After Interview:
- Don’t over-analyze every word you said
- Send thank-you email same day
- Reflect on what went well and what to improve
- Keep applying to other positions (don’t put all hopes on one)
- Move forward with confidence
Your Cyber Security Journey
Remember why you chose this field. Cyber security professionals protect people, companies, and critical infrastructure. Every day, you’ll solve puzzles, learn new things, and make a real difference.
The journey from student to professional is challenging but achievable. You have:
220+ technical questions and answers (Part 1)
50 AI-powered learning prompts (Part 2)
Communication and behavioral skills (Part 3)
Complete preparation toolkit (Part 4)
Now it’s time to take action:
- Review all four parts systematically
- Practice daily with hands-on labs and AI prompts
- Build your portfolio and update your resume
- Apply strategically to relevant positions
- Network with professionals in the field
- Prepare thoroughly for each interview
- Believe in your abilities and keep improving
Remember: Every security professional started exactly where you are now. The difference between those who succeed and those who don’t isn’t talent—it’s persistence, continuous learning, and refusing to give up.
You’ve got this. Now go ace that interview and launch your cyber security career!
Quick Reference Checklist
Before Applying:
☐ Resume tailored for job
☐ LinkedIn profile optimized
☐ Portfolio/GitHub updated
☐ Cover letter written (if required)
☐ References prepared
Before Interview:
☐ Company researched thoroughly
☐ Job description reviewed and matched to skills
☐ Technical concepts reviewed
☐ STAR stories prepared and practiced
☐ Questions for interviewers prepared
☐ Interview outfit ready
☐ Tech setup tested (for virtual interviews)
☐ Resume copies printed
☐ Directions/login information confirmed
After Interview:
☐ Thank-you email sent within 24 hours
☐ Notes taken about interview experience
☐ Follow-up plan established
☐ Continued job search (don’t wait)
After Offer:
☐ Reviewed complete compensation package
☐ Researched market rates
☐ Negotiated professionally if appropriate
☐ Got everything in writing
☐ Gracefully declined other opportunities
☐ Prepared for first day
🧩 Combine Technical + Behavioural Skills the Smart Way
🧭 View Full Cybersecurity Roadmap →
CONCLUSION

This completes the Cyber Security Interview Preparation Guide – all 4 parts covering:
✅ Part 1: 220+ Technical Interview Questions & Answers
✅ Part 2: 50 Self-Preparation Prompts Using ChatGPT
✅ Part 3: Communication Skills and Behavioural
✅ Part 4: Additional Preparation Elements
This comprehensive guide provides everything students need to prepare for cyber security interviews—from technical mastery to professional presence, from resume building to salary negotiation, from portfolio creation to continuous learning.
The content is written in simple, humanized language without citations, designed to help students not just pass interviews but truly understand the field and build successful cyber security careers.
Your preparation starts now. Good luck!
🎓 Your Cybersecurity Career Starts Now!
📘 All Resources • 🧭 Roadmap • 🎯 Join Course
